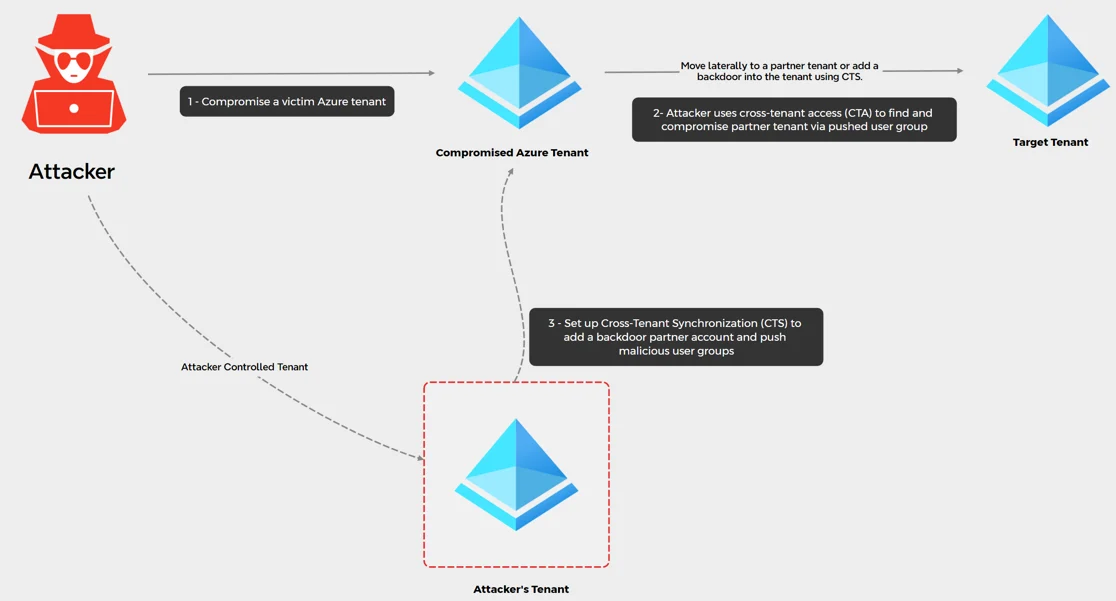
Cross-Tenant Synchronization attack in Azure
A new wave of ransomware attacks targeting cloud infrastructures has put the insurance and financial industries on high alert. According to a recent report from EclecticIQ analysts, the Scattered Spider group has been leveraging advanced social engineering tactics and exploiting cloud-native tools to launch a series of highly sophisticated attacks.
Scattered Spider, an activity cluster notorious for its cloud-based attacks, has been increasingly active in recent months. The group employs a variety of techniques, including vishing (voice phishing) and smishing (SMS phishing), to deceive and manipulate IT service desks and identity administrators. These social engineering tactics allow the group to gain unauthorized access to privileged cloud accounts, manipulate Multi-Factor Authentication (MFA) settings, and steal sensitive credentials.
One of the more alarming trends is Scattered Spider’s use of cloud-native features to maintain persistent access to compromised systems. These legitimate tools, often built into cloud environments, make it difficult for organizations to detect malicious activities.
EclecticIQ’s report highlights that Scattered Spider has primarily targeted insurance and financial services, focusing on cloud-based platforms like Microsoft Entra ID (formerly Azure Active Directory), AWS EC2, and various Software-as-a-Service (SaaS) platforms such as Okta, ServiceNow, and VMware Workspace ONE. The group’s phishing campaigns often mimic the Single Sign-On (SSO) portals of these services, tricking high-privileged users into divulging their login credentials.

US-based financial services
In a surge of attacks from January to February 2024, the group resumed smishing campaigns, bypassing traditional email filters by targeting users directly on their mobile devices. These attacks aim to steal credentials and One-Time Passwords (OTPs), even bypassing MFA protections, which are a key defense in many cloud environments.
Scattered Spider has demonstrated an acute understanding of cloud infrastructures, frequently taking advantage of accidental cloud authentication token leakage. These tokens, often exposed in public repositories such as GitHub, are used to gain unauthorized access to corporate cloud environments. The attackers then use automated tools to scan for vulnerable cloud systems, enabling them to expand their operations with minimal effort.
The report also reveals a potential partnership between Scattered Spider and the infamous BlackCat/ALPHV ransomware group. Analysts believe that Scattered Spider’s deep cultural familiarity with Western business practices has made them a valuable asset for BlackCat, enhancing the latter’s ability to effectively target Western organizations. This collaboration is likely to lead to more sophisticated and widespread attacks in the future.
In addition to their phishing and token-stealing tactics, Scattered Spider has adopted SIM swapping techniques to bypass MFA protections. By deceiving mobile carriers into transferring victims’ phone numbers to attacker-controlled SIM cards, the group intercepts MFA codes sent via SMS, gaining access to cloud platforms like Okta and ServiceNow.
Once inside a compromised account, Scattered Spider can move laterally across the network, creating unauthorized virtual machines (VMs) that bypass security systems and remain undetected. These newly created VMs often lack endpoint detection and response (EDR) tools, providing the attackers with a persistent foothold in the network.
Organizations must act swiftly to strengthen their defenses, particularly against the social engineering tactics and cloud-native exploitation techniques employed by Scattered Spider. Without immediate action, the next wave of attacks could bring even more disruption to critical industries.
Related Posts:
- New Phishing Campaigns from Scattered Spider Target Finance and Insurance Industries
- BlackCat Ransomware and Beyond: Deciphering Scattered Spider’s Latest TTPs
- 17-Year-Old Suspected Cybercriminal Nabbed in UK, Tied to MGM Hack
- US Enterprises Targeted: Silent Push Unmasks Scattered Spider’s Phishing Web
- Phishing Campaign Bypasses MFA to Target Meta Business Accounts, Putting Millions at Risk