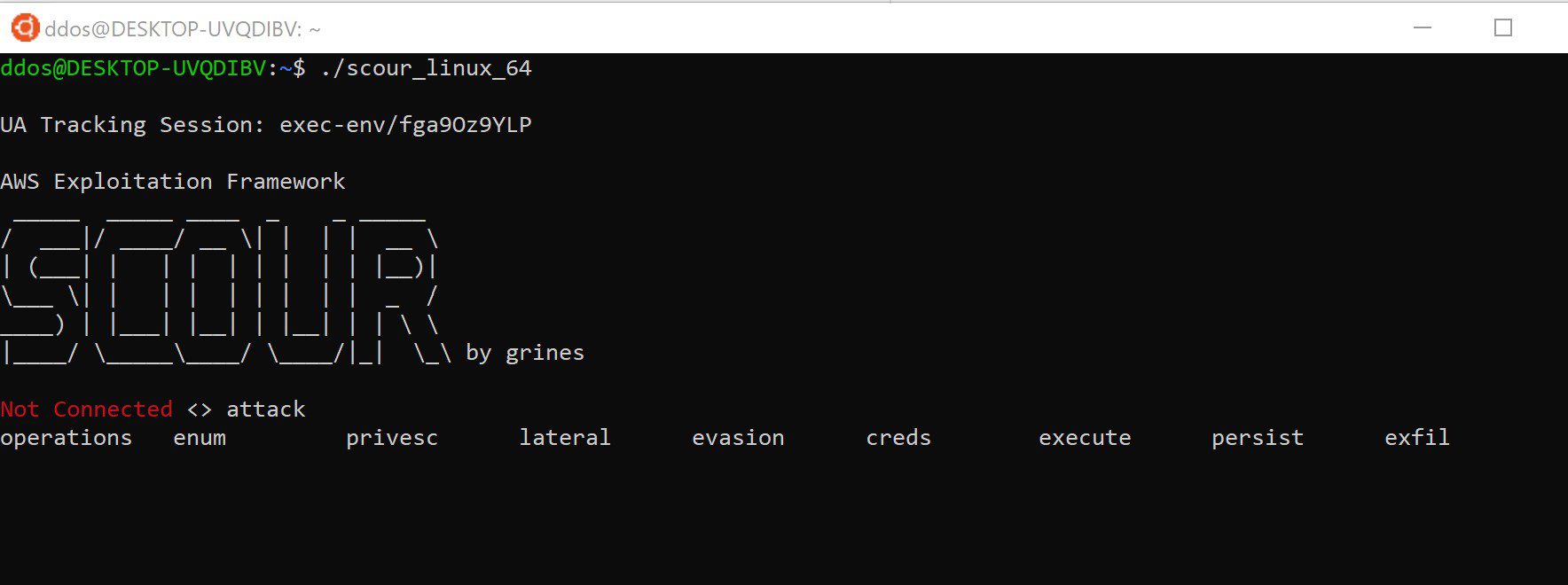
Scour – AWS Exploitation Framework
Scour is a modern module-based AWS exploitation framework written in golang, designed for red team testing and blue team analysis. Scour contains modern techniques that can be used to attack environments or build detections for defense.
Features
- Command Completion
- Dynamic resource listing
- Command history
- Blue team mode (tags attacks with unique User-Agent)
Scour uses a range of modules:
- Operations (2)
- Enumeration (7)
- Privilege Escalation (3)
- Lateral Movement (2)
- Evasion (5)
- Credential Discovery (4)
- Execution (2)
- Persistance (7)
- Exfiltration (1)
Basic Commands in Scour
- token profile <profile_name> <region> will list the available aws profiles stored in ~/aws/credentials.
- token AssumeRole <role_name> <region> will assume the role from same or cross-account. ** requires an active session
- help module will return the applicable help information for the specified module. **help TBD
- attack evasion <tactic> will run the specified module with its default parameters.
Running Scour From the command line
- scour will enter cli mode
- Not Connected <> token profile apiuser us-east-1 sets the session to use for commands that require one
- Connected <apiuser/us-east-1> actively connected to an aws profile from (~,/aws/credentials) in (region)
- Connected <apiuser/us-east-1> attack enum <attack> tab completion with list available enumeration tactics
- Connected <apiuser/us-east-1> attack privesc <attack> tab completion with list available privilege escalation tactics
- Connected <apiuser/us-east-1> attack lateral <attack> tab completion with list available lateral tactics
- Connected <apiuser/us-east-1> attack evasion <attack> tab completion with list available evasion tactics
- Connected <apiuser/us-east-1> attack creds <attack> tab completion with list available credential discovery tactics
- Connected <apiuser/us-east-1> attack execute <attack> tab completion with list available execution tactics
- Connected <apiuser/us-east-1> attack persist <attack> tab completion with list available persistence tactics
- Connected <apiuser/us-east-1> attack exfil <attack> tab completion with list available exfiltration tactics