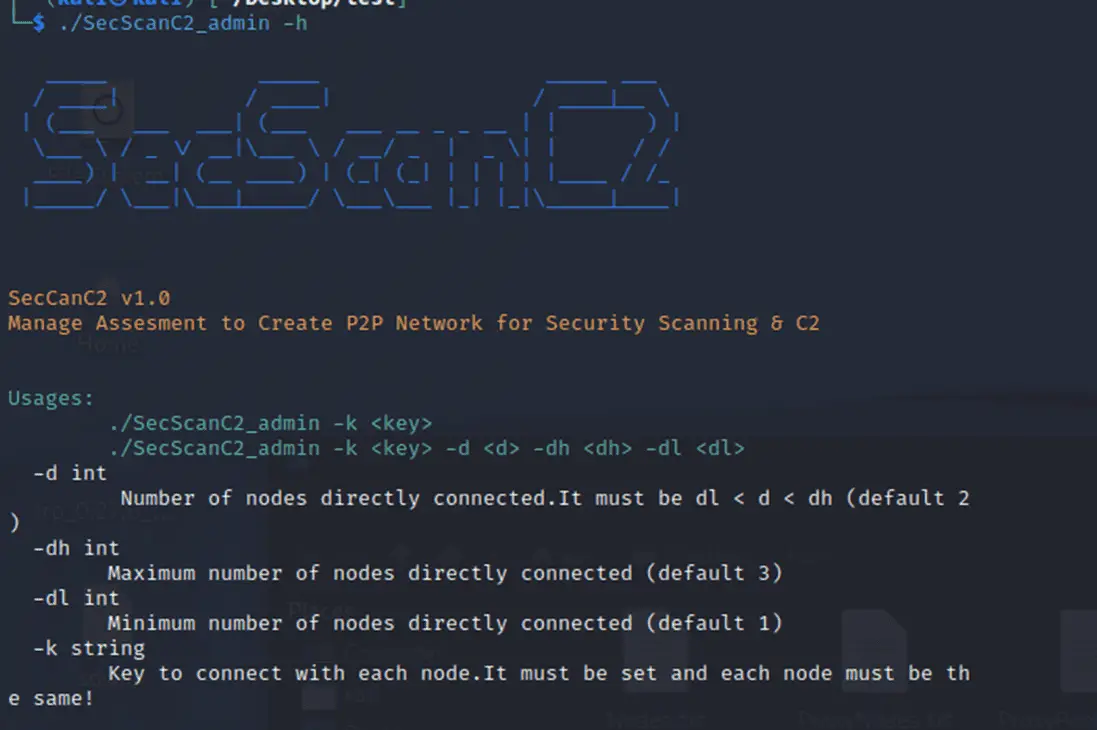
SecScanC2
SecScanC2 can manage assessment to create a P2P network for security scanning & C2. The tool can assist security researchers in conducting penetration testing more efficiently, preventing scanning from being blocked, and protecting themselves from being traced.
Features
- P2P: build a large number of Internet nodes into a P2P network
- Prevent scanning from being blocked: randomly or specify nodes as proxy pools, all nodes in the P2P network will start a SOCKS proxy, and the proxies will be put into the proxy pools. When we do detection and scanning, we can connect to the proxy pool, and the proxy pool will randomly select a proxy for every request.
- Can effectively hide C2 servers to prevent traceability: The decentralized structure adopts the publish-subscribe model to complete the information interaction of each node. The C2 node publishes the command to the P2P network. The command randomly selects nodes in the network for multi-hop transmission. After the target node subscribes to the command, it executes the command and publishes the execution result of the command to the P2P network. The execution result randomly selects nodes for multi-hop transmission. The C2 node finally subscribes to the command execution result. Throughout the process, the C2 node does not directly interact with the target node. So the C2 node can avoid being traced.

Role
SecScanC2 has two kinds of roles:
admin: The admin node used by the penetration tester
node: The ordinary node deployed by the penetration tester
SecScanC2_admin: create an admin node.
SecScanC2_ node: create an ordinary node.
The startup parameters of both programs are the same.