Image: Threatfabric
A recent cybersecurity study has exposed the machinations of “SecuriDropper,” a malicious product exemplifying the burgeoning “dropper-as-a-service” (DaaS) trend, which strategically infects selected devices with malware at the behest of cybercriminals via a specialized dropper.
SecuriDropper, in the iteration scrutinized by ThreatFabric experts, targets Android smartphones and adeptly circumvents Google’s implemented security measures to deliver malware to devices specified by hackers.
Android droppers serve as a conduit for the deployment of secondary malicious code onto compromised devices, akin to brokers of initial access in the mobile context. This lucrative enterprise enjoys demand among various cybercriminal syndicates.
ThreatFabric researchers contend that dropper creators are continually evolving, aspiring to outpace the fortifying efforts of security experts. For instance, a security feature introduced by Google in Android 13 is the “Restricted Settings” option, which forbids applications installed from external sources from obtaining permissions to access notifications and the special services function. Such permissions are frequently exploited by banking trojans.

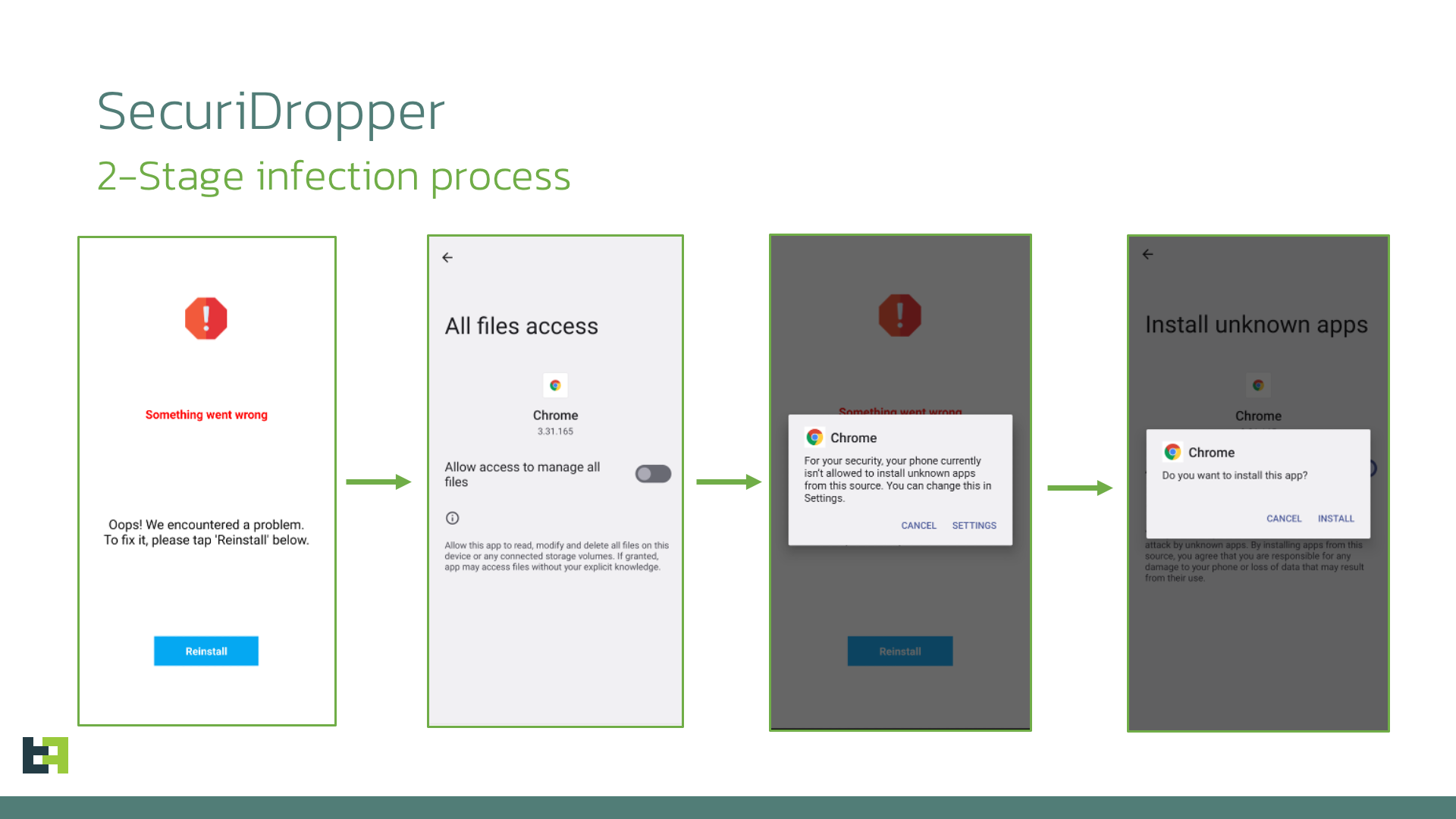
Nevertheless, SecuriDropper successfully navigates around these limitations by utilizing an alternative API to install malicious code, mimicking the process used by app stores to install new applications. This malware is disseminated outside of Google Play, often masquerading as popular Google applications, including Chrome and Google Search.
Upon installation and execution, the dropper prompts the user with a notification of improper installation, suggesting a reinstallation, during which it initiates a new installation process, compelling the victim to grant the necessary permissions to the malicious app.
ThreatFabric researchers have observed Android banking trojans such as SpyNote and ERMAC being disseminated via SecuriDropper on phishing sites and platforms of third-party vendors, including Discord.
In addition to SecuriDropper, the researchers have also encountered other malware circumventing Android’s restricted setting access. One such pernicious program is “Zombinder,” which is being sold on cybercriminal forums for $1,000.
Zombinder derives its name from its characteristic of “binding” a legitimate application with code that facilitates the deployment of the malicious payload onto the infected device. Essentially, Zombinder couples the dropper to a legitimate app.
Currently, it remains unclear whether there is any connection between SecuriDropper and Zombinder. It is only evident that as Android continues to raise the bar of security with each new iteration, cybercriminals also adapt and devise methods to circumvent protective measures.
“Dropper-as-a-Service (DaaS) platforms have emerged as potent tools, allowing malicious actors to infiltrate devices to distribute spyware and banking Trojans. These malicious payloads, once unleashed, can compromise users’ privacy and financial security,” concluded ThreatFabric.