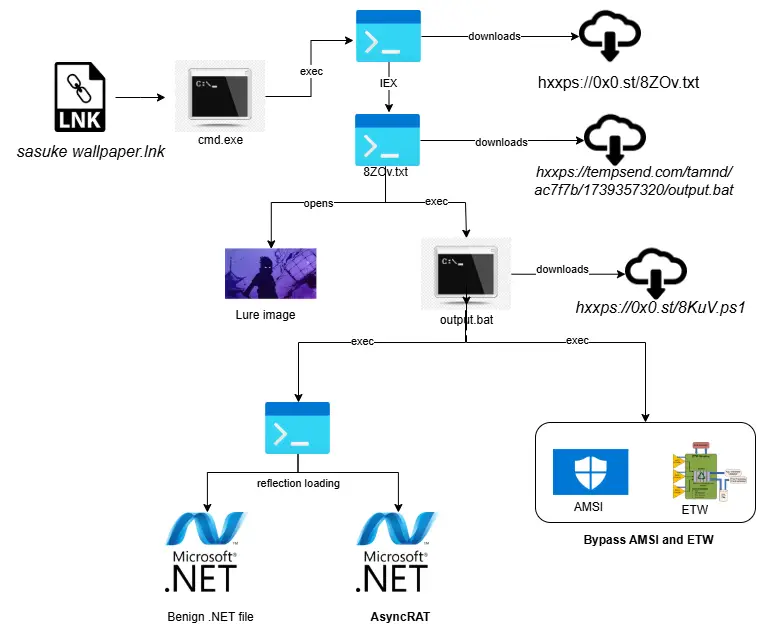
Infection chain | Source: CRIL
A new malware campaign uncovered by Cyble Research and Intelligence Labs (CRIL) is leveraging Null-AMSI to bypass Windows security defenses and deploy AsyncRAT, a powerful remote access trojan (RAT). This attack method effectively evades traditional security tools, allowing attackers to establish persistent access to compromised systems.
The attack begins with malicious LNK files disguised as wallpapers featuring popular animated characters, tricking users into executing them.
“The malware uses a multi-stage execution process, using obfuscated PowerShell scripts to fetch additional payloads from the remote server,” explains the CRIL.
Once the user opens the LNK file, it executes an obfuscated PowerShell script that retrieves a second-stage payload from an external source. This payload is then executed directly in memory, leaving no trace on disk.
The attackers employ Null-AMSI, an open-source tool available on GitHub, to bypass the Antimalware Scan Interface (AMSI) and Event Tracing for Windows (ETW).
“By employing reflection and native .NET functions, the malware dynamically manipulates AMSI in memory without triggering security alerts,” the report says.
This technique allows the malware to:
- Modify AMSI protections in memory, preventing antivirus software from scanning malicious scripts.
- Disable ETW logging, making it difficult to detect malicious activity.
- Use AES encryption and GZIP compression to obfuscate payloads, complicating static analysis.
Once AMSI and ETW protections are neutralized, the final payload, AsyncRAT, is executed in memory using reflection loading techniques.
“The final payload is executed into memory using reflection loading, bypassing traditional security measures while ensuring persistence and executing AsyncRAT for remote control,” the report warns.
AsyncRAT provides the attacker with full control over the compromised system, enabling:
- Keystroke logging and credential theft
- Remote command execution
- Exfiltration of sensitive data
- Installation of additional malware
For further details, visit the Cyble Research and Intelligence Labs (CRIL) full report.
Related Posts:
- AsyncRAT Rises Again: Malware Abuses Legitimate Services for Stealthy Delivery
- Beware of Fake Downloads: AsyncRAT Spreads via Popular Software Cracks
- AsyncRAT Malware Campaign Exploits Bitbucket to Deliver Multi-Stage Attack
- Evasive Phishing Campaign Delivers AsyncRAT and Infostealer
- Cybercriminals Exploit Ebooks to Spread AsyncRAT Malware