Bootkitty passes the verification process | Image: Binarly REsearch
Security researchers from Binarly and ESET have uncovered “Bootkitty,” the first-ever UEFI bootkit designed to target Linux systems. This new threat exploits the LogoFAIL vulnerability (CVE-2023-40238), a UEFI firmware flaw, to bypass Secure Boot protections and inject malicious payloads.
As detailed by ESET researchers Martin Smolar and Peter Strýček, Bootkitty is a proof-of-concept bootkit capable of infecting the Linux kernel. They stated, “While this appears to be a proof-of-concept rather than an active threat, Bootkitty signals a major shift as attackers expand bootkit attacks beyond the Windows ecosystem.”
This marks a significant milestone in the progression of firmware-based threats, previously exemplified by malware such as BlackLotus and MoonBounce. ESET’s analysis highlighted that Bootkitty exploits “operating system bootloaders [as] a vast attack surface that is often overlooked by defenders.”
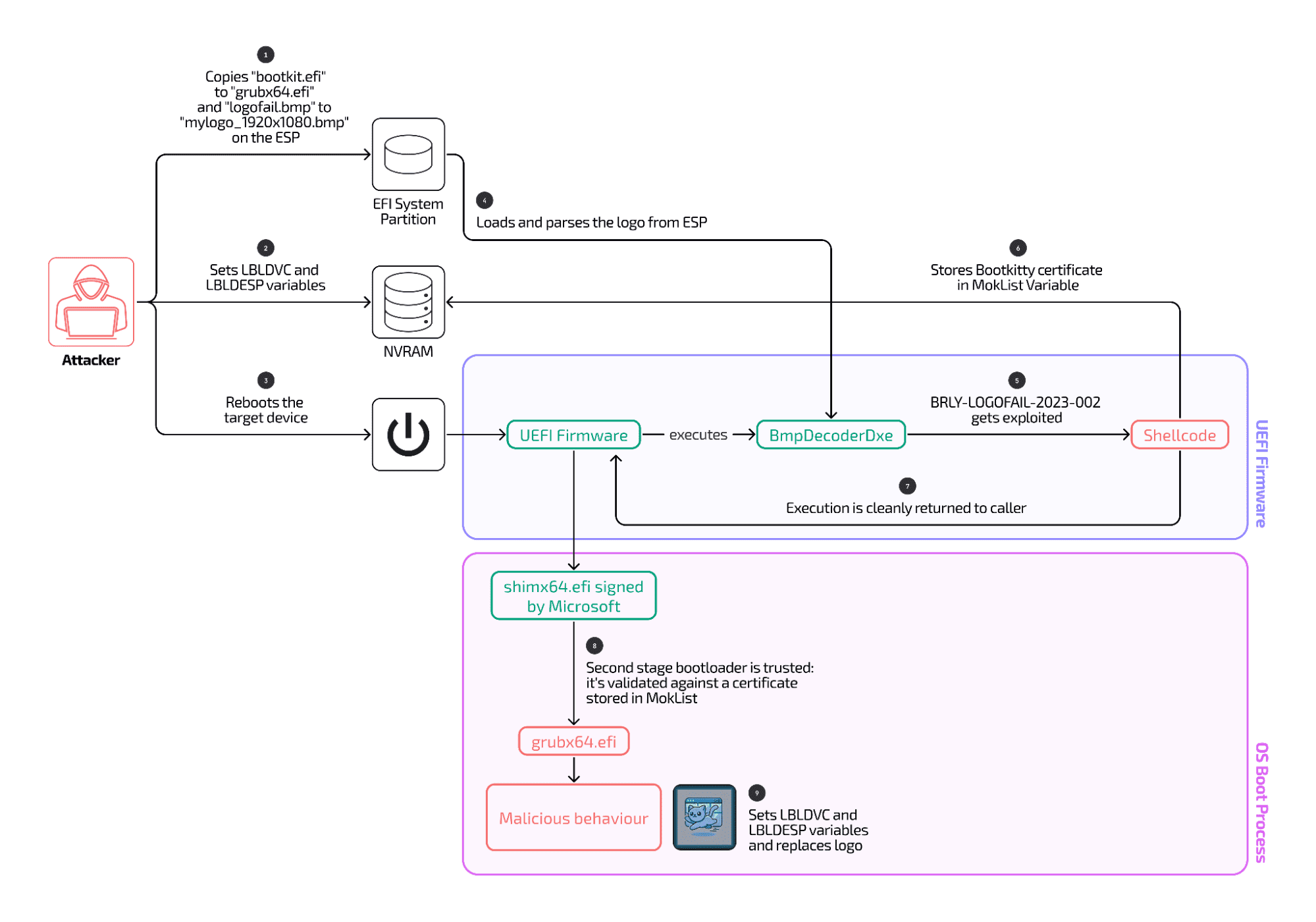
The vulnerability at the heart of Bootkitty, LogoFAIL (CVE-2023-40238), was first presented by Binarly at BlackHat EU 2023. The flaw lies in the BmpDecoderDxe module within UEFI firmware, where improper handling of BMP image parsing allows attackers to execute malicious shellcode.
As Binarly researchers explained, “The exploit uses embedded shellcode within a BMP image to bypass Secure Boot protections by injecting rogue certificates into the MokList variable.” This rogue MokList enables the bootkit to be trusted by the system’s Secure Boot components, allowing it to load during the early boot process.
Bootkitty’s infection chain begins with tampered BMP files, specifically named logofail.bmp, embedded with shellcode. Binarly’s analysis revealed that these malicious files:
- Contain embedded shellcode designed to tamper with Secure Boot’s MokList variable.
- Exploit vulnerabilities to achieve arbitrary code execution within the UEFI environment.
- Replace legitimate boot logos with rogue logos to maintain stealth.
The researchers noted that this technique ensures, “the shellcode restores the original instructions, hiding the exploit activity and effectively clearing all traces of the bootkit.”
The vulnerability impacts UEFI firmware in devices from Acer, HP, Fujitsu, and Lenovo. While some manufacturers, like Insyde, have issued patches, numerous unpatched devices remain vulnerable. Notably, Lenovo devices using specific firmware versions were identified as prime targets due to their compatibility with Bootkitty’s exploit chain.
Bootkitty and LogoFAIL underscore the critical need for robust firmware-level security. Binarly emphasized, “It’s been more than a year since we first sounded the alarm about LogoFAIL, yet many affected parties remain vulnerable.”
To defend against such threats:
- Update Firmware: Users are advised to apply the latest firmware patches from their device manufacturers.
- Leverage Detection Tools: Organizations using the Binarly Transparency Platform receive proactive detection capabilities for LogoFAIL and related bootkit components.
- Secure Boot Enhancements: Implement additional Secure Boot checks to prevent rogue certificates.
The full report, including technical details and further implications, is available from Binarly and ESET.
Related Posts:
- ESET Unveils “Bootkitty”: The First UEFI Bootkit Targeting Linux Systems
- Your Boot Logo is Hackable: LogoFAIL Exposes Millions of Devices
- LogoFAIL Vulnerabilities Expose Firmware Attacks: Endpoint Security Solutions at Risk
- PKfail Vulnerability: A New Threat to UEFI Security Unveiled by Binarly Research Team