A new study by Dor Segal, a security researcher at Silverfort, has revealed a critical vulnerability in FIDO2, the popular passwordless authentication standard designed to protect against phishing and man-in-the-middle (MITM) attacks. The research demonstrates that, despite its strong security features, FIDO2-authenticated sessions can still be hijacked through MITM attacks, potentially exposing sensitive user data and compromising accounts.

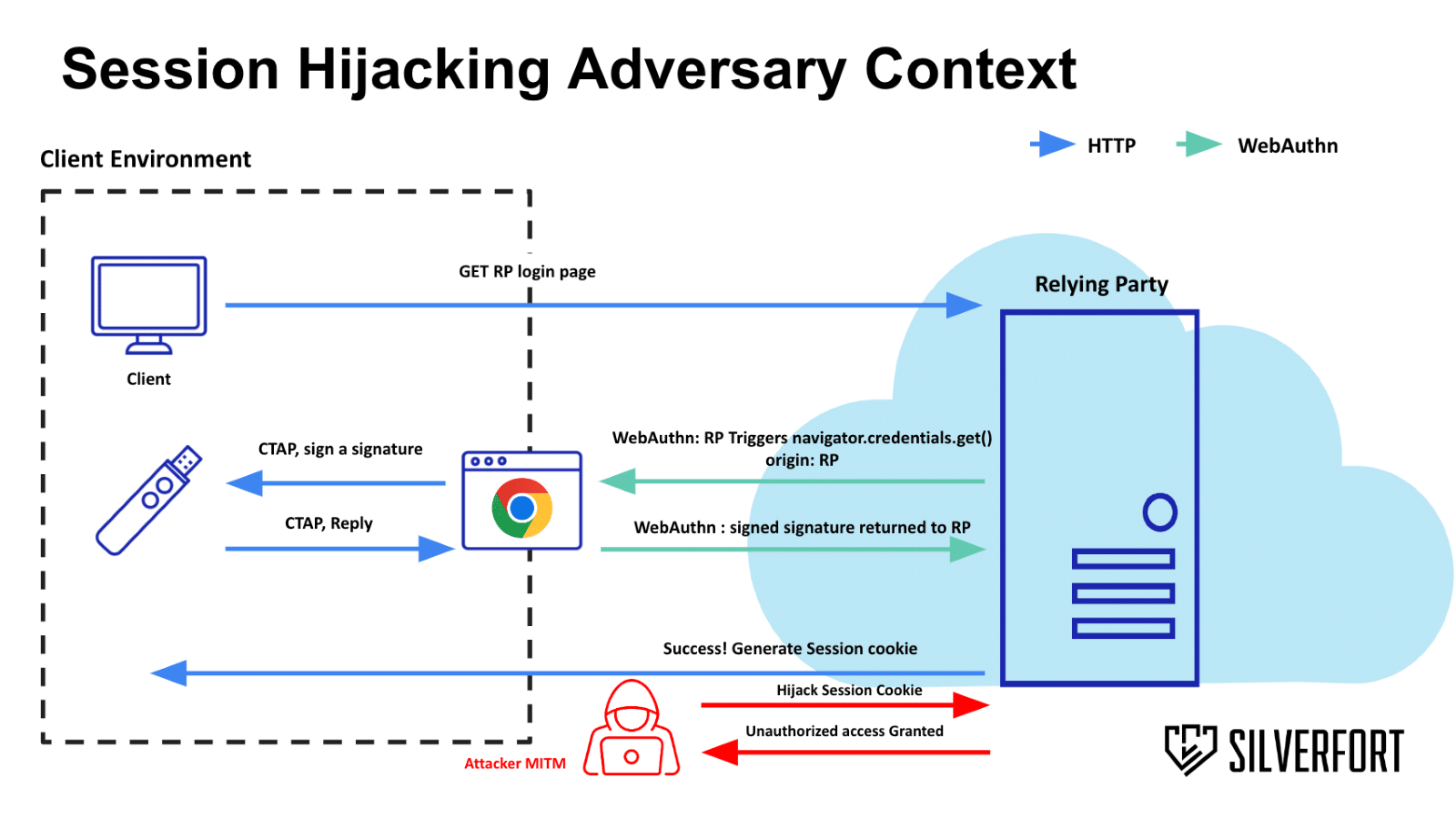
FIDO2 operates on a two-step authentication process managed by the browser, involving the WebAuthn API for client-server interactions and the Client to Authenticator Protocol (CTAP) for hardware communication. This setup is based on public key cryptography, where the client generates a key pair, retaining the private key and transmitting the public key for signature verification during login.
While FIDO2 effectively prevents phishing attacks by verifying domain origins, it falls short in protecting session tokens after authentication. Segal discovered that many identity providers (IdPs) do not validate the source device using the session token, allowing attackers who successfully execute an MITM attack to steal the token and hijack the user’s session.
The research delves into sophisticated MITM attack methods, such as DNS/DHCP spoofing, ARP poisoning, and SLAAC, that are still feasible despite TLS protections. Even more alarming, state actors have managed to decrypt TLS by compromising organizational certificates, exemplified by attacks on Active Directory Certification Services.
Segal’s research tested several real-world scenarios, including Yubico Playground, Entra ID SSO (Microsoft), and PingFederate. In each case, he demonstrated how an attacker could bypass FIDO2’s protections and gain unauthorized access to user accounts and sensitive information. These scenarios demonstrate varying levels of security and expose how different configurations can either hinder or facilitate MITM attacks. For instance, in the Yubico Playground, a simple session cookie can be exploited to gain unauthorized access, underscoring the need for rigorous validation mechanisms beyond initial authentication.