Image: Assetnote
ServiceNow, a widely used platform for business transformation, has recently disclosed three critical security vulnerabilities that could have severe consequences for organizations worldwide. These vulnerabilities, identified as CVE-2024-4879, CVE-2024-5217, and CVE-2024-5178, affect various versions of the Now Platform, including Washington D.C., Vancouver, and Utah releases.
The most alarming of these flaws are CVE-2024-4879 and CVE-2024-5217, both carrying a critical CVSSv4 score of 9.3 and 9.2, respectively. These vulnerabilities enable unauthenticated remote attackers to execute arbitrary code within the Now Platform, potentially leading to complete system compromise, data theft, and disruption of critical business operations.
The third vulnerability, CVE-2024-5178, with a CVSSv4 score of 4.0, allows administrative users to gain unauthorized access to sensitive files on the web application server. While not as severe as the previous two, this flaw still poses a significant risk of data exposure and unauthorized access to confidential information.
Chain Reaction: Vulnerabilities Leading to Full Database Access and MID Server Compromise
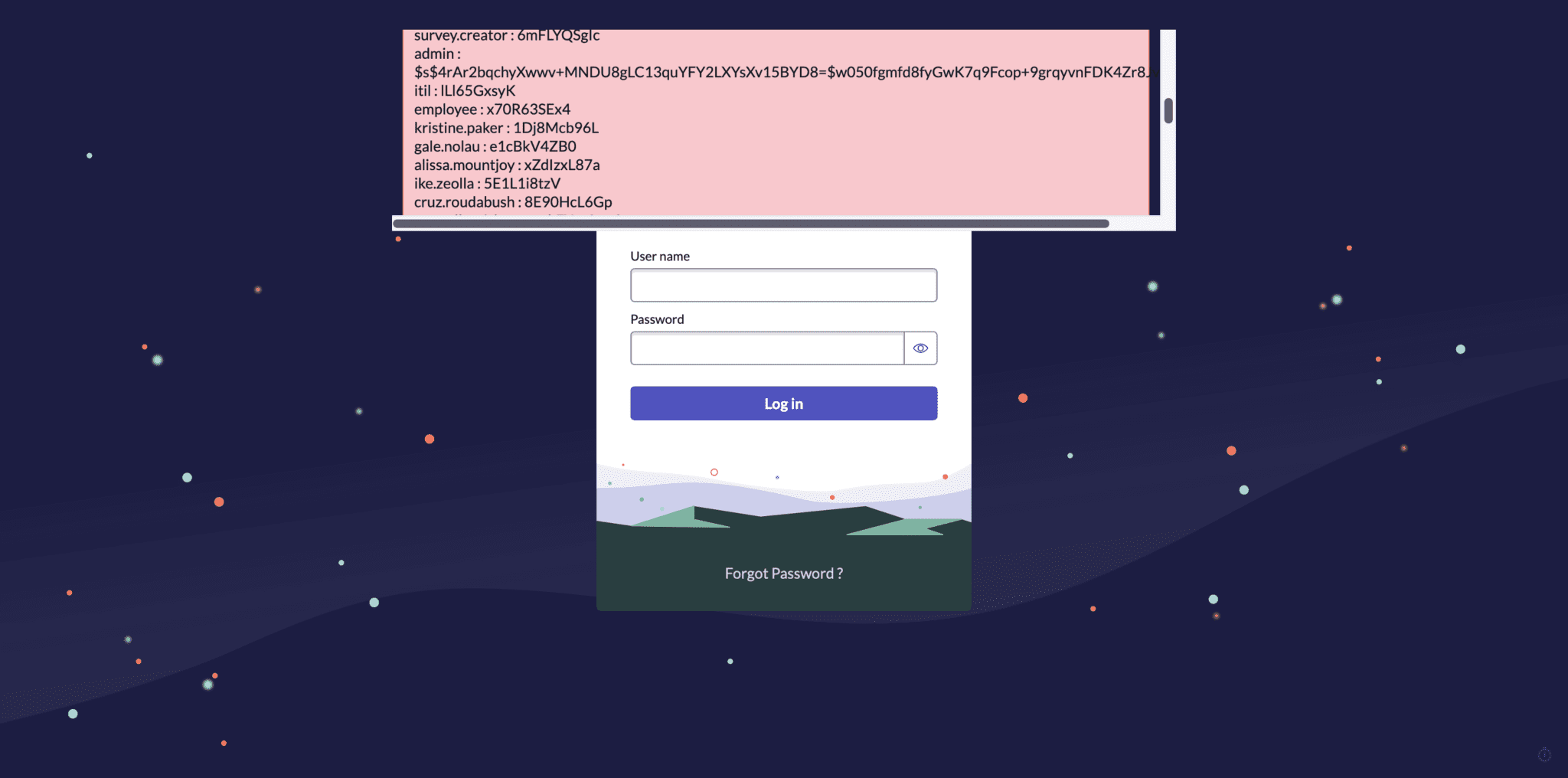
The situation is further exacerbated by the findings of cybersecurity researchers at Assetnote, who discovered a chain of vulnerabilities that could lead to full database access and complete control of any MID servers configured with ServiceNow. This means that attackers exploiting these vulnerabilities could gain access to a vast amount of sensitive data and potentially disrupt or sabotage critical infrastructure.
Immediate Action Required: Patch Now!
ServiceNow has released patches and hotfixes to address these vulnerabilities [1,2,3]. It is crucial for organizations using ServiceNow to apply these updates immediately to protect their systems and data from potential attacks.