SGC: Towards Automating Code-Reuse Attacks Using Synthesized Gadget Chains
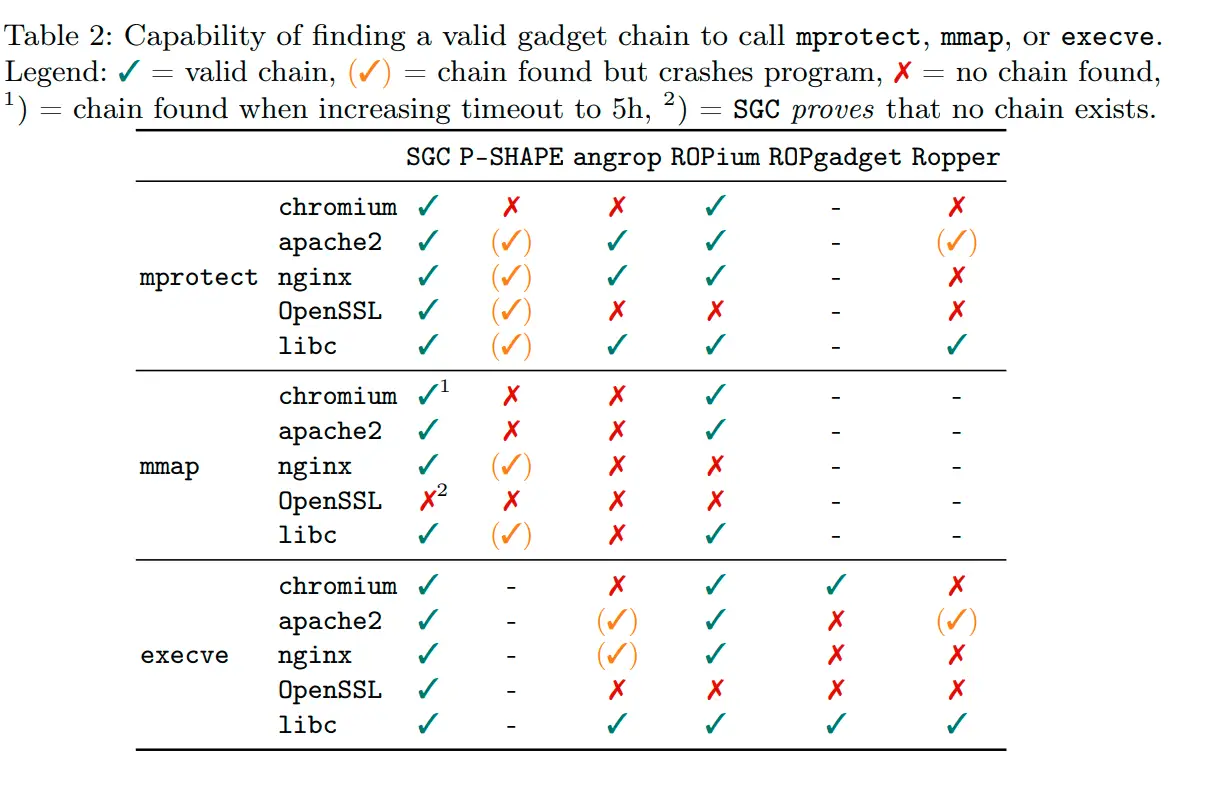
SGC is a tool to automatically synthesize gadget chains. It builds a logical formula to encode the execution state at the time when the attacker can divert execution flow to the gadget chain as well as the attacker’s desired program state that the gadget chain should construct. By extracting and then logically encoding gadgets, we query an SMT solver to decide whether a valid gadget chain exists. Check out the paper for details.

Features
What SGC can do – a non-exhaustive list:
- use gadgets with untypical instructions or side-effects
- build gadget chains
- prove no gadget chain can exist (sparing you further looking at the problem)
- model all complex constraints (that can be expressed as logic formula!)
SGC’s Workflow
The general workflow is to
- Manually identify a target and a desired state (and encode this information in a target configuration file
- Run SGC’s extractor.py to automatically extract all functions from the target and disassemble all gadgets. These steps have to be conducted only once, the disassembly results are stored (“cached”) in the targets directory to allow re-use.
- SGC’s synthesizer.py can synthesize a gadget chain for the gadgets (or a subset of them). The synthesis process can use a multitude of different settings (different chain lengths, sizes of subsets, …). The default settings can be found in synthesizer_config_default.json.
- In an optional last step, you can verify the validity and applicability of the gadget chains using symbolic execution and/or GDB (refer to verify_se.py / verify_gdb.py in ./verification).
Install
Copyright (C) 2021 RUB-SysSec