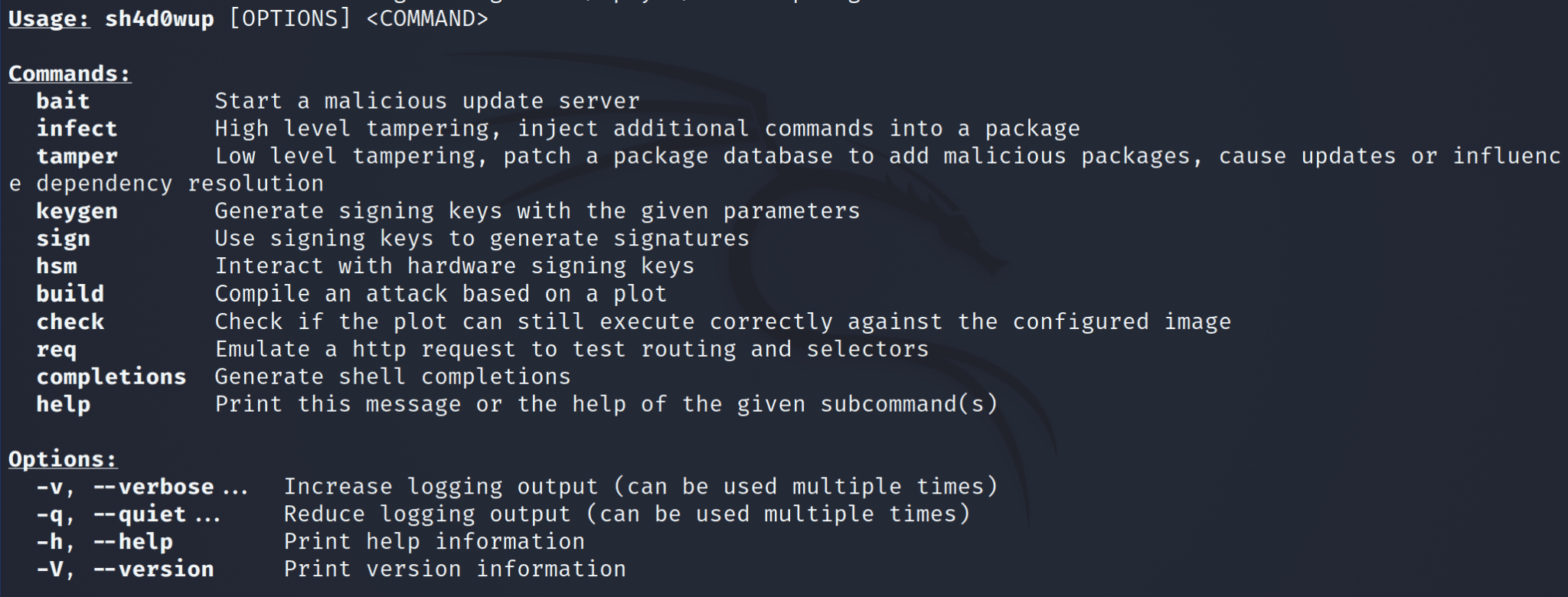
sh4d0wup v0.9.1 releases: Signing-key abuse and update exploitation framework
sh4d0wup
Have you ever wondered if the update you downloaded is the same one everybody else gets or did you get a different one that was made just for you? Shadow updates are updates that officially don’t exist but carry valid signatures and would get accepted by clients as genuine. This may happen if the signing key is compromised by hackers or if a release engineer with legitimate access turns grimy.
sh4d0wup is a malicious http/https update server that acts as a reverse proxy in front of a legitimate server and can infect + sign various artifact formats. Attacks are configured in plots that describe how http request routing works, how artifacts are patched/generated, how they should be signed and with which key. A route can have selectors so it matches only if eg. the user-agent matches a pattern or if the client is connecting from a specific ip address. For development and testing, mock signing keys/certificates can be generated and marked as trusted.
Compile a plot
Some plots are more complex to run than others, to avoid long startup time due to downloads and artifact patching, you can build a plot in advance. This also allows to create signatures in advance.
sh4d0wup build ./contrib/plot-hello-world.yaml -o ./plot.tar.zst
Run a plot
This spawns a malicious http update server according to the plot. This also accepts yaml files but they may take longer to start.
sh4d0wup bait -B 0.0.0.0:1337 ./plot.tar.zst
Changelog v0.9.1
- Fix build issues with Rust 1.72.0
- Add a default key type for ssh keys (
ed25519) and default key sizes for each key type (rsa=> 4096,dsa=> 1024,ecdsa=> 256,ed25519=> 256)- It’s now sufficient to run
sh4d0wup keygen sshto generate a burner ssh key
- It’s now sufficient to run
- Add
--secret-key-onlyand--public-key-onlyflags tosh4d0wup keygento ease scripting - Updated dependencies
Install & Use

Copyright (C) 2023 kpcyrd





