sharem: ultimate Windows shellcode tool
sharem
SHAREM is intended to be the ultimate Windows shellcode tool, with support to emulate over 12,000 WinAPIs, virtually all user-mode Windows syscalls, and SHAREM provides numerous new features. SHAREM was released on September 29, 2022, at Virus Bulletin, the top malware conference globally. SHAREM contains an emulator, a disassembler, timeless debugging, brute-force deobfuscation, and many other features. SHAREM’s emulator can also display complete structures (or even structures within structures) and it can allow encoded shellcode to deobfuscate itself. SHAREM logs output from all WinAPIs and Windows syscalls analyzed, and it also breaks each into many categories and subcategories. SHAREM’s complete code coverage also allows it to discover unreachable functionality.
SHAREM’s disassembler is able to integrate discovered functions into the disassembly, labeling each in the disassembler. SHAREM also will display the decrypted form of the encoded shellcode in the disassembler, so it is not necessary to debug the shellcode.

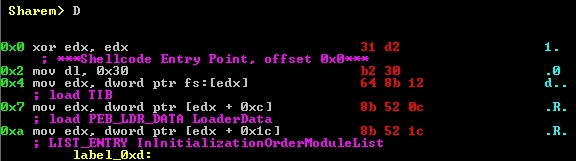
SHAREM can also generate other useful data about a sample. From the main menu, the D option can be used to generate annotated disassembly of a shellcode file. This option allows the user to easily look through the code and identify where significant malicious actions occur, such as PEB walking sequences.
Options regarding the disassembly feature can be found in the option accessible by typing d in the main menu.
The disassembly engine is done with several custom analysis functions, and it is done through static analysis. It is significantly more accurate at analyzing shellcode than all other disassemblers. However, it is recommended to run the disassembler only after having emulated the shellcode. The reason why is that API’s that are identified can then be identified in the disassembly. Additionally, SHAREM will combine the results of the emulation to improve the static analysis. When the emulation is run with code coverage, the results can be nearly flawless. Note that when emulated, the results of emulation are prioritized and “override” any differences (if any) from static analysis, but it is done byte by byte.
If the shellcode was encoded but has been deobfuscated, the disassembler by default will show the deobfuscated shellcode, rather than the encoded bytes – which are meaningless to the user.
The disassembler provides the rich, aesthetically pleasing coloring for different elements of the disassembly. It also saves the disassembly as a text file, and as a JSON file. The JSON file can be imported into a website, as can all the results.






