SharpHide: Tool to create hidden registry keys
SharpHide
Just a nice persistence trick to confuse DFIR investigation. Uses NtSetValueKey native API to create a hidden (null-terminated) registry key. This works by adding a null byte in front of the UNICODE_STRING key valuename.
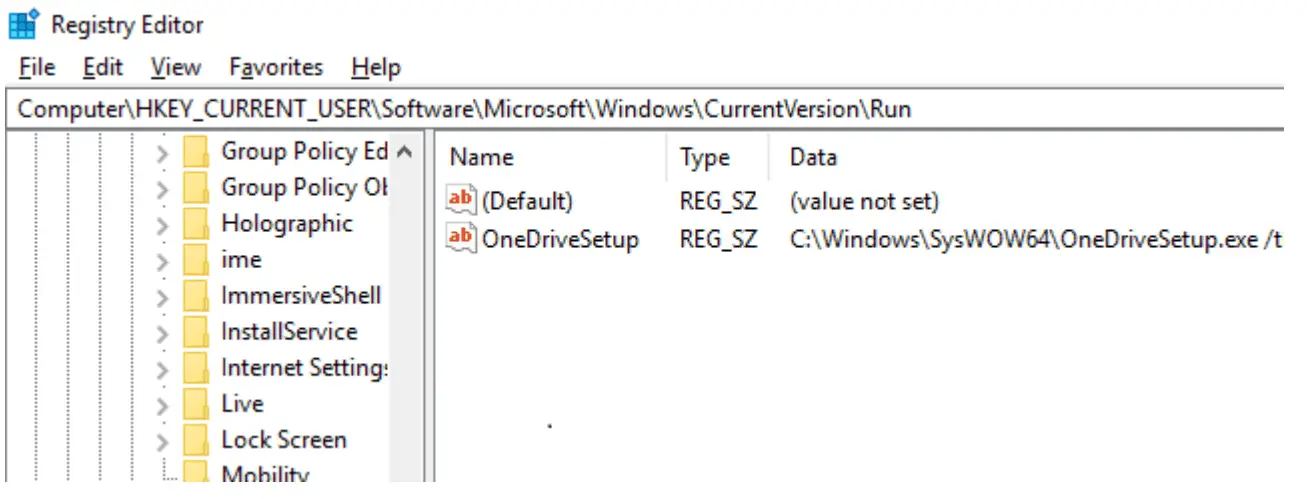
The tool uses the following registry path in which it creates the hidden run key: (HKCU if user, else HKLM)\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.”
Technique
INVISIBLE PERSISTENCE
CONVENTIONAL PERSISTENCE
Malware that is running without elevated privileges on Windows has limited options for regaining execution after a system reboot (aka persistence). Malware that elevates privileges using either zero-day or public exploits has more options for persisting. However, zero-days are expensive and their use risks their exposure, and public exploits will not work on patched systems. Most malware is stuck using well-known persistence techniques that are easily detected. The most straightforward persistence technique is to write a value to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run (or
the analogous key in HKEY_LOCAL_MACHINE). The values of this key are commands which Windows runs when the user logs in (in the case of HKEY_CURRENT_USER) or as it boots (in the case of HKEY_LOCAL_MACHINE). Malware writes the path to its executable file to the Run key. In this way, it regains execution after a reboot. Because this is a well-known technique, a suspicious value in the Run key is a red flag that the system is infected. It also discloses the location of the malware on the system which makes collecting a sample to analyze very straightforward.
FILELESS BINARY STORAGE
CONVENTIONAL FILE STORAGE ON DISK
Anti-virus software scans files on disk. A/V software hashes files and sends the signatures to the cloud. Some anti-virus performs heuristic checks on files stored on disk. Suspected malware files can even be silently sent to the cloud. To counter this, malware has several options. The files on disk can be generic droppers, that reach out to the Internet and download more substantial modules (which are loaded in memory, without touching disk). Malware can also craft the executables stored on disk to not trip anti-virus heuristics. For example, since anti-virus often scans for high-entropy segments in PEs (which indicate compressed or encrypted data), malware can avoid using encryption and compression to protect its executables. Since anti-virus has heuristics that scan import tables, malware can avoid importing suspicious functions. Such countermeasures are burdensome to the malware developers and, in any case, do not guarantee that their binaries will not be sent to the cloud.
Download && Use
Author: Cornelis de Plaa (@Cneelis) / Outflank





