The executable file with Microsoft Word icon
In a recent analysis conducted in March and April 2024, the NetbyteSEC Detecx (NBS) team exposed a sophisticated malware campaign orchestrated by the notorious SharpPanda APT group, specifically aimed at targets in Malaysia. The malicious executable, disguised as a harmless Microsoft Word document titled “REKOD MINIT KSN KEPADA YAB PM 2023 – 15.exe,” was designed to establish a backdoor connection, granting attackers unauthorized access to compromised systems.

Upon dissecting the malware’s intricate workings, the NBS team discovered that it employed various techniques to evade detection and achieve its objectives. The malware utilized XOR decryption to conceal critical strings used for its functionality, including URL paths, Windows API calls, and mutex names. By creating a unique mutex, the malware ensured that only one instance could run on an infected machine, effectively preventing multiple infections.
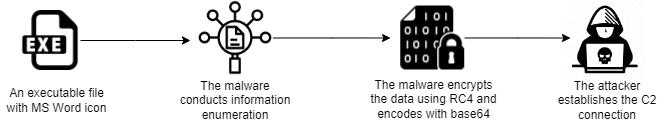
One of the malware’s core functions involved collecting extensive information about the compromised system, including hostname, OS details, usernames, network interfaces, installed programs, and running processes. This valuable data was then encrypted using the RC4 algorithm and encoded with Base64 before being transmitted to the attacker’s command-and-control (C2) server located in Hong Kong.
The communication with the C2 server was established using Windows Sockets API, further demonstrating the malware’s sophistication and stealth. The encrypted data, embedded within the URL path parameter, made it difficult for security solutions to detect the malicious traffic.
The SharpPanda APT group has a history of targeting government entities and critical infrastructure in the Asia-Pacific region. This latest campaign against Malaysia highlights the persistent threat posed by state-sponsored actors. Organizations and individuals in Malaysia are strongly advised to exercise caution when dealing with unsolicited emails and attachments, especially those disguised as official documents.
To mitigate the risk of falling victim to such attacks, it is crucial to implement robust security measures, including up-to-date antivirus software, regular security patches, and employee awareness training on identifying and reporting suspicious activity.