Sigma Hunting App
A Splunk App containing Sigma detection rules, which can be updated dynamically from a Git repository.
Motivation
Most of the modern Security Operations Center (SOC) store the detection rules in a central repository such as GitHub or GitLab as part of the Dev Sec Ops development approach. Furthermore, Sigma as a generic signature description language is used in many SOCs. Updating the Sigma rules from a Sigma repository to Splunk was still a manual time-consuming task. The Sigma Hunting App solves that problem by providing a dedicated Splunk App, which can be used to dynamically update Sigma detection rules from a Git repository. The triggered detection rules are stored in a separate threat-hunting index helping the SOC Analyst in their investigations. Additionally, the Sigma Hunting App for Splunk uses the information of the Mitre ATT&CK Matrix to enrich the triggered detection rules.
The Sigma Hunting App for Splunk provides the following features:
- dynamically update of Sigma detection rules from a remote Git repository
- Store triggered detection rules in a dedicated index
- Enrichment of triggered detection rules with data from the Mitre ATT&CK Matrix
- Providing powerful dashboards for investigation: security posture, host investigator, APT investigator, lateral movement investigator
- Whitelist App to adapt the detection rules to your environment
Update of Sigma Detection Rules
The Sigma detection rules can be updated from the Sigma Hunting App: 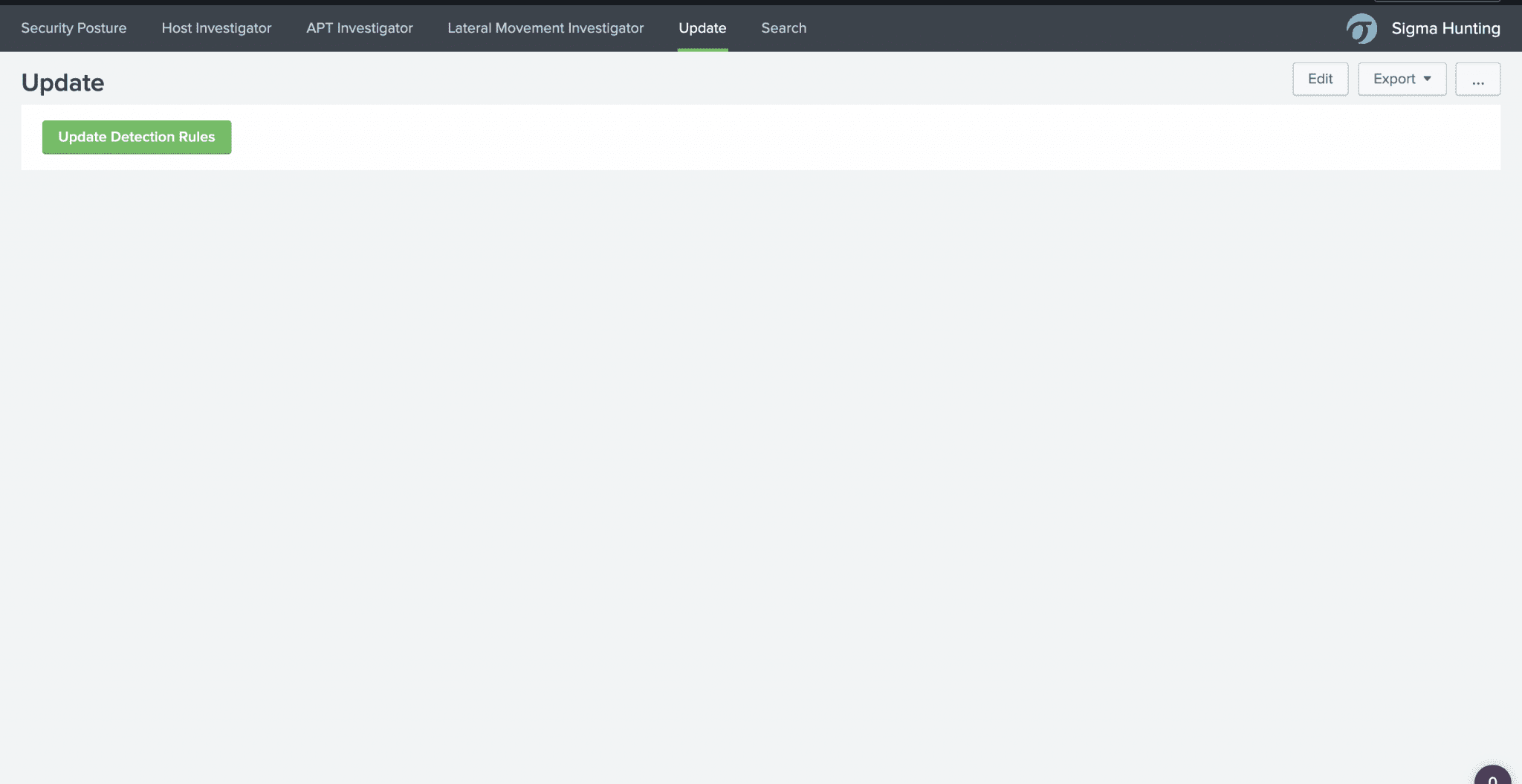
The remote Git repository can be configured through the Set-Up view of the Sigma Hunting App:
Store triggered Detection Rules in a dedicated Index
The triggered Detection Rules are stored in the threat-hunting index: 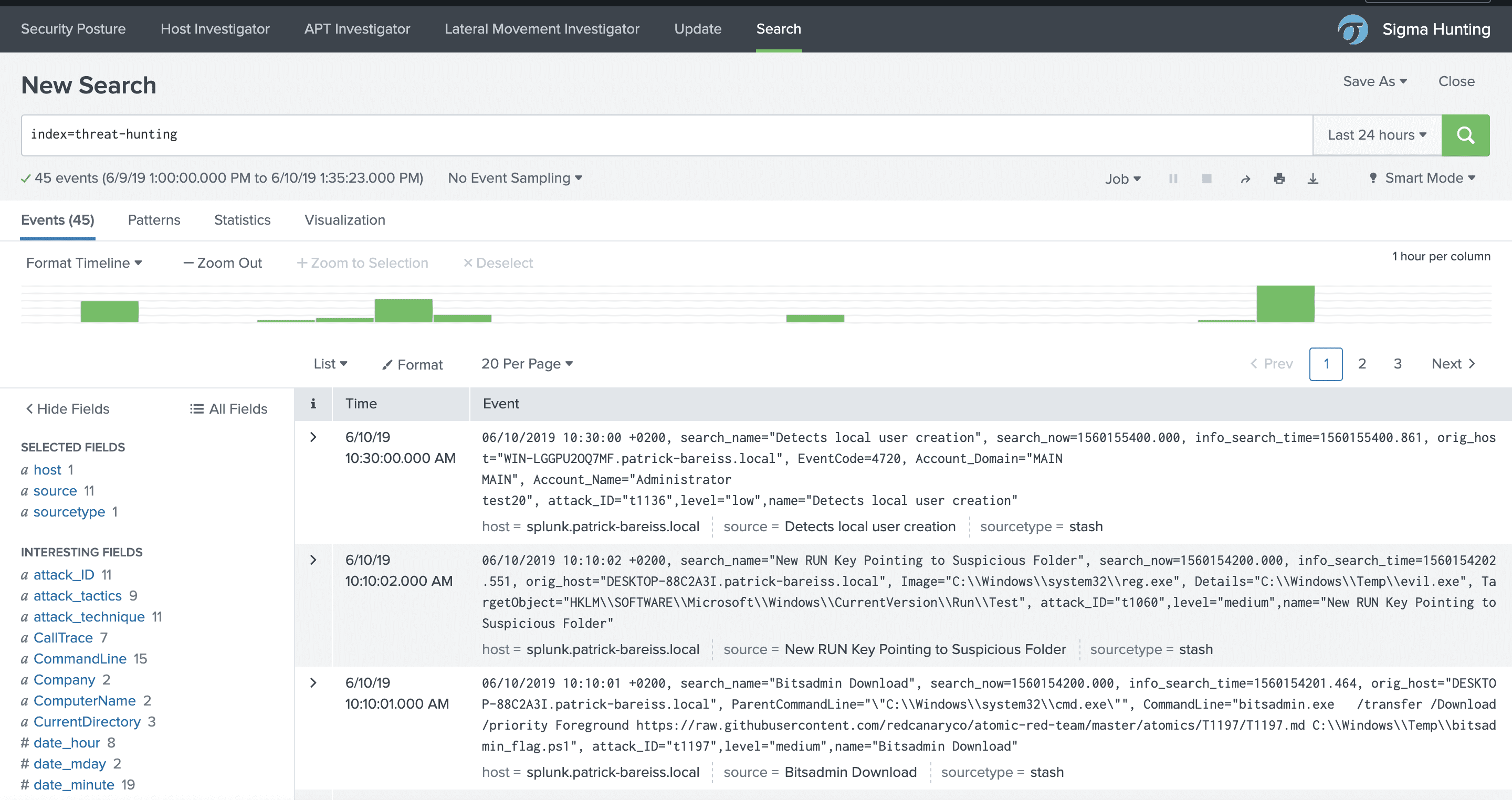
Enrichment with Mitre ATT&CK Data
The triggered Detection Rules in the threat-hunting index are enriched with Mitre ATT&CK Data such as Technique, Tactics, ID, Threat Actors.
Providing Investigation Dashboards
There exist several dashboards for investigations. The security posture dashboard gives you an overview of the triggered detection rules categorized into Mitre ATT&CK Tactics: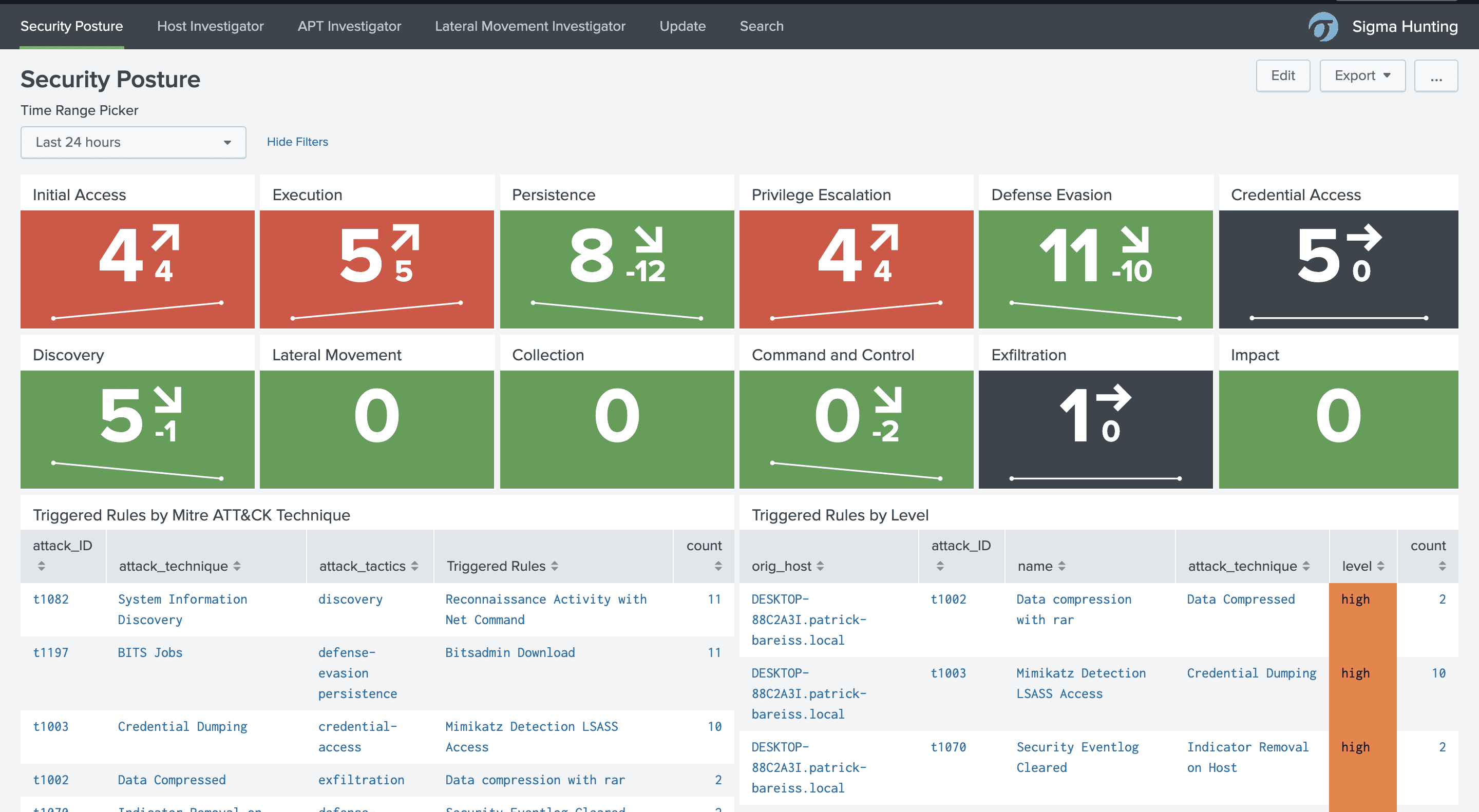
The Host Investigator supports you to perform investigation for a specific host. It shows the different triggered detection rules in a timeline chart: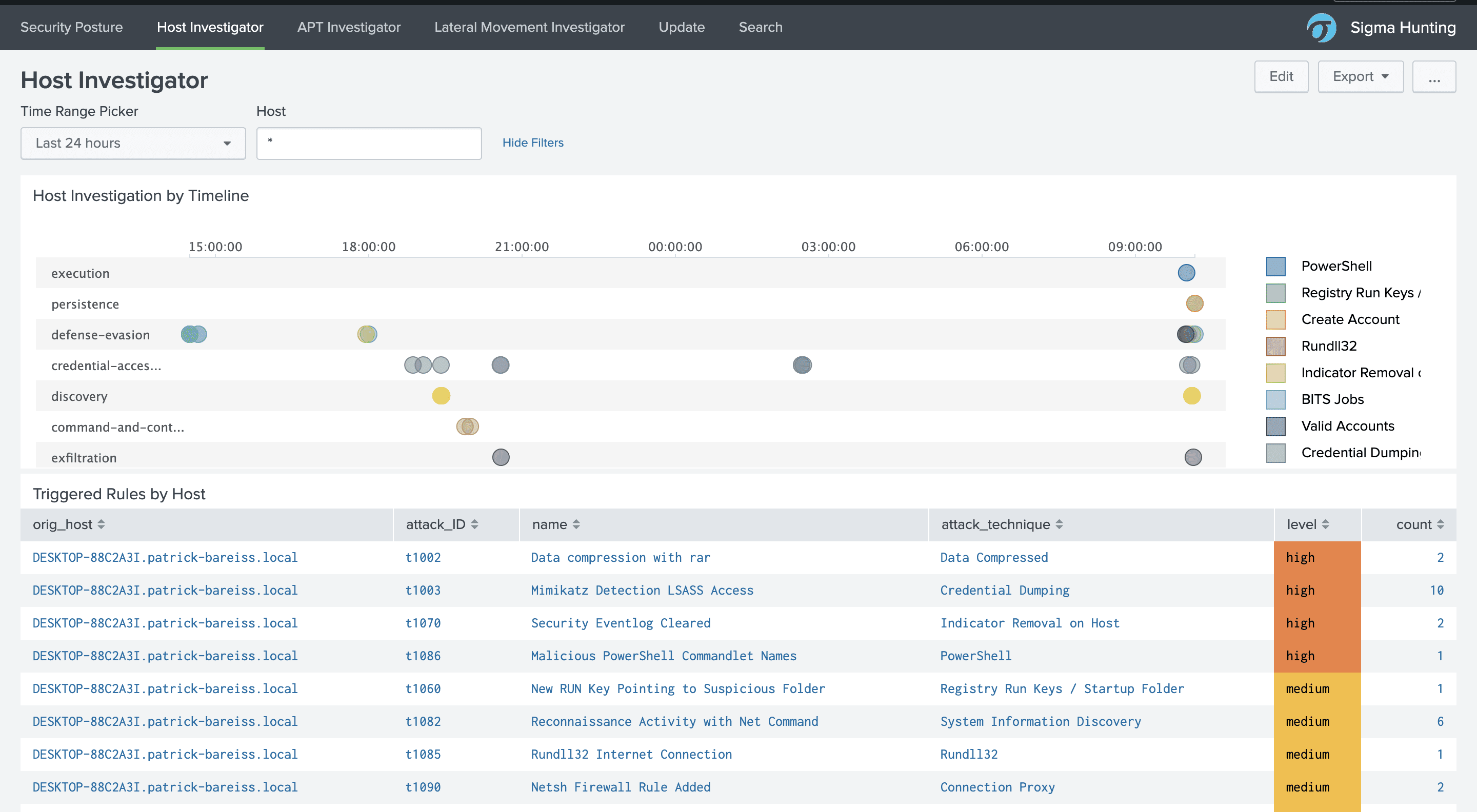
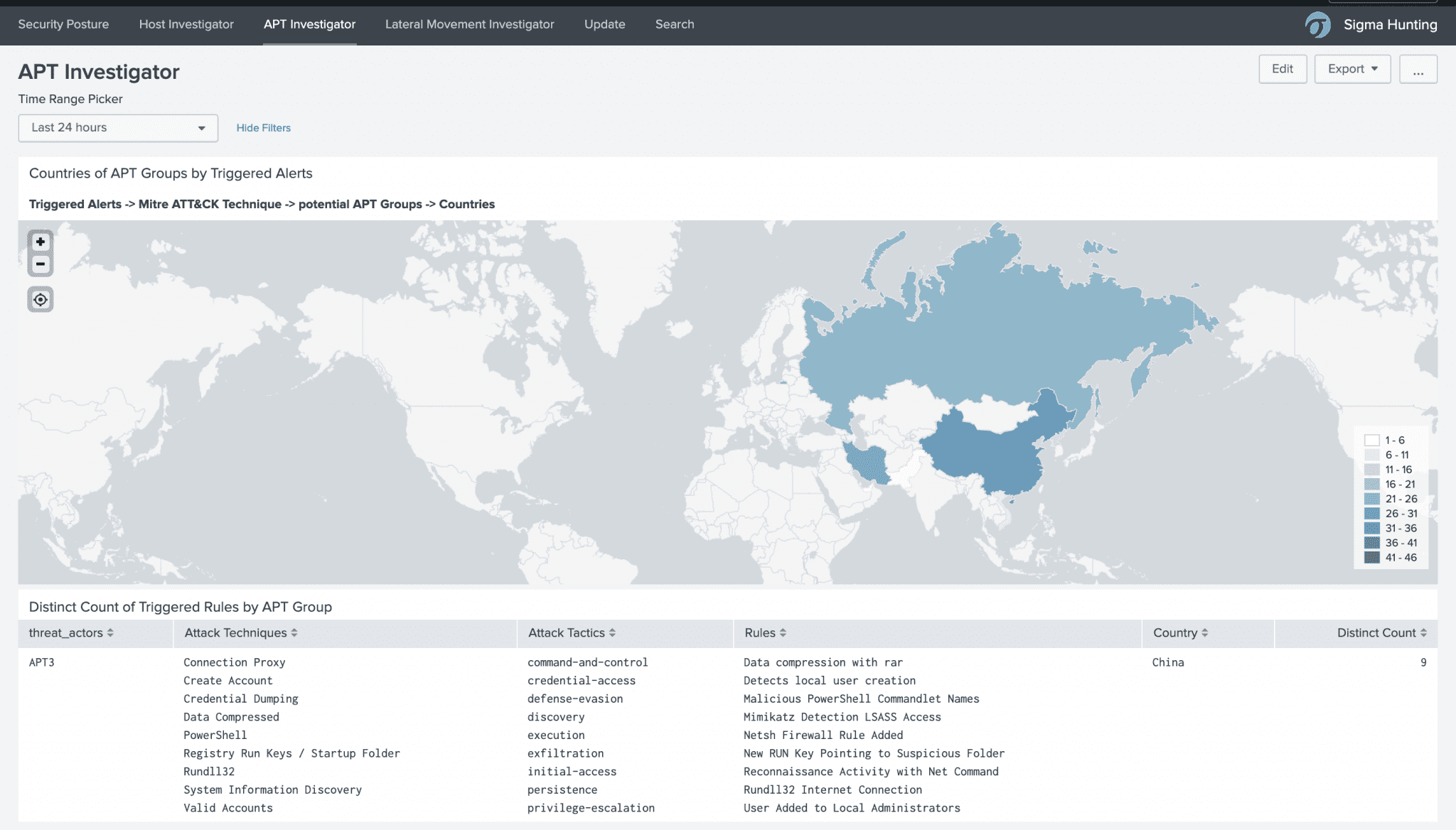
The APT investigator tries to identify, which threat actor is attacking you by using the information of the triggered detection rules: 
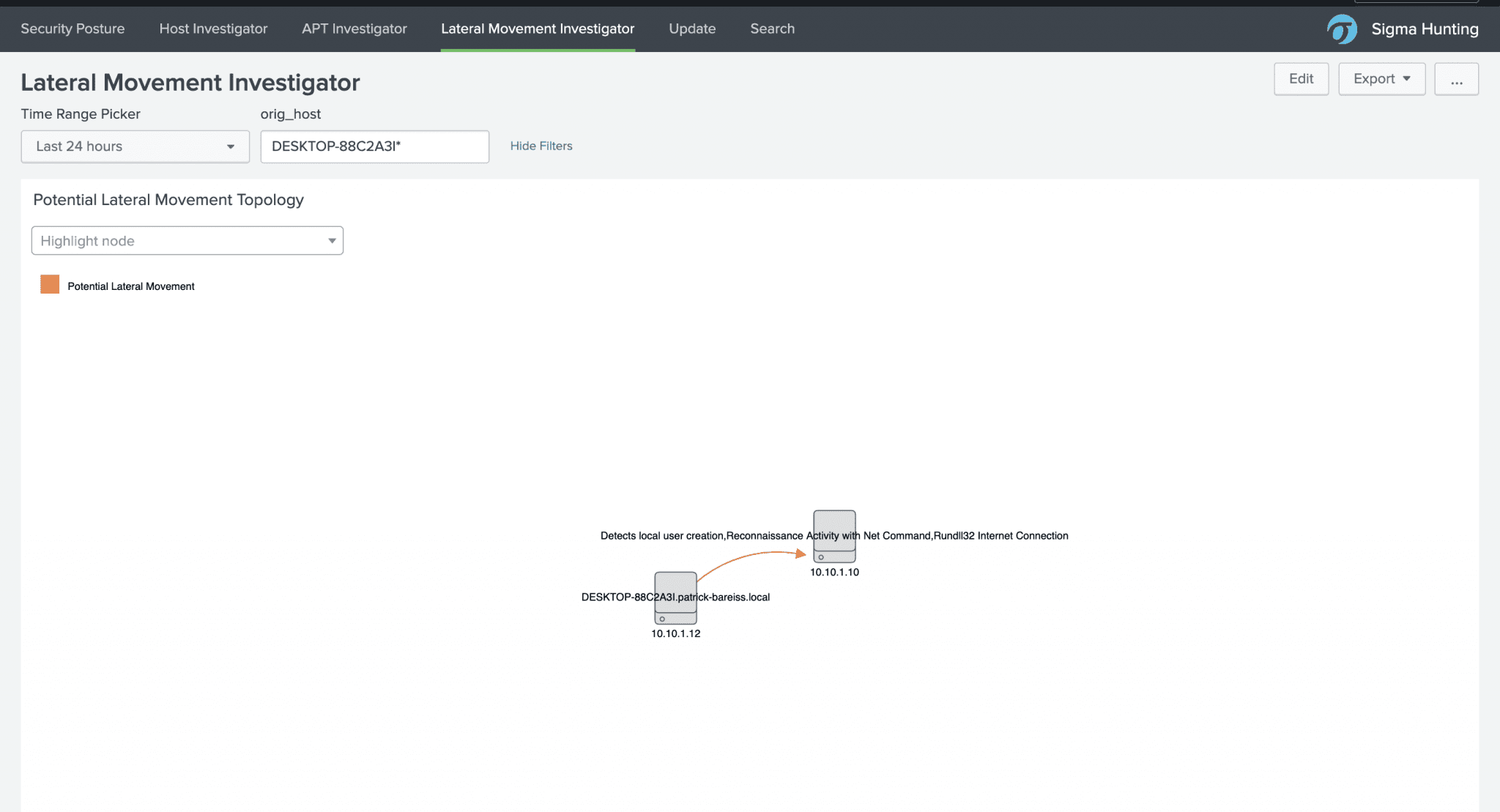
The Lateral Movement Investigator uses the information of triggered alerts in combination with firewall data in order to find lateral movement. It identifies if the same detection rule was triggered for two hosts and there was a network connection between them:
Sigma Hunting Whitelist App for Splunk
The Sigma Hunting Whitelist App contains the whitelist for your detection rules. That helps the SOC Analysts to tune the detection rules and define exceptions/whitelists: 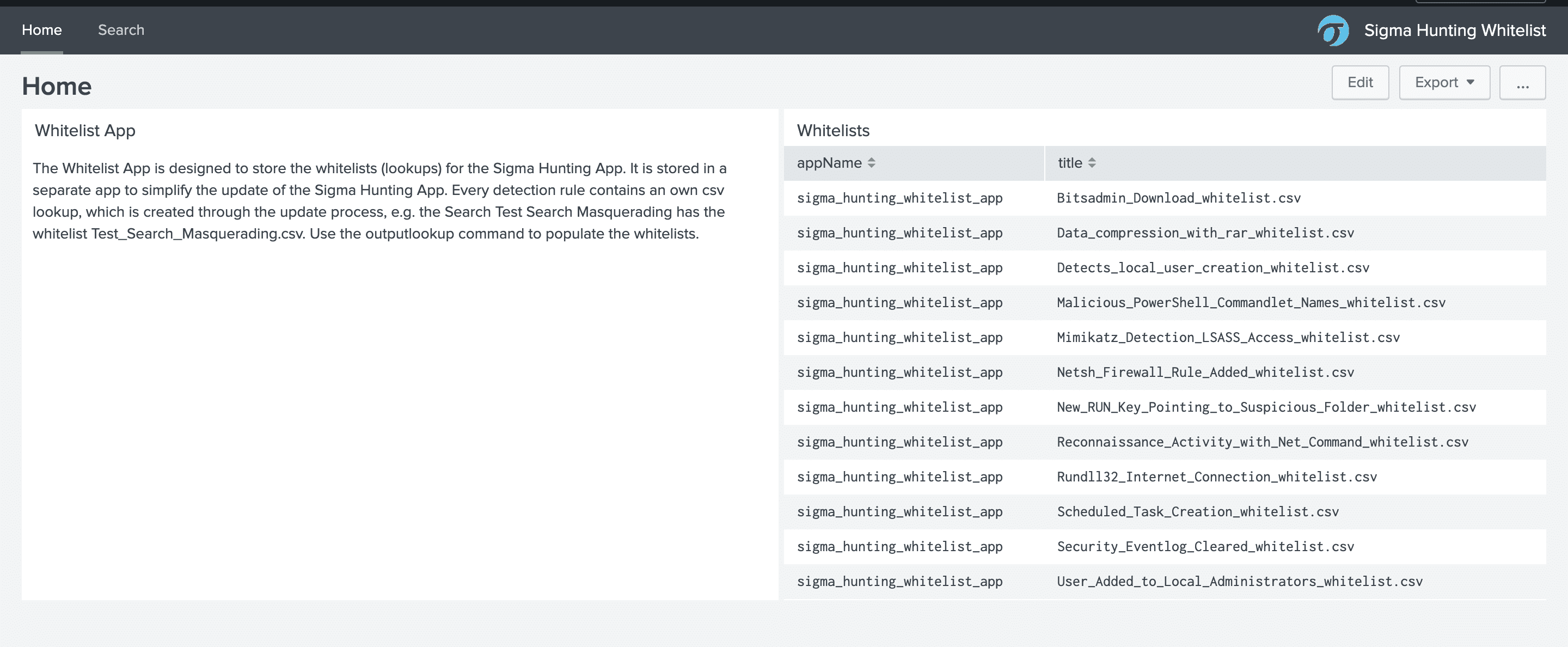
Install && Use
Copyright (c) 2019 P4T12ICK