
A sophisticated cyber-espionage campaign targeting organizations across China, Hong Kong, and Taiwan has been uncovered by Intezer’s research team. The attacks, attributed to the advanced persistent threat (APT) group Silver Fox, utilize a newly identified loader named PNGPlug to deliver the ValleyRAT malware.
The campaign begins with phishing websites that lure victims into downloading malicious Microsoft Installer (MSI) packages disguised as legitimate software. According to the report, “The installer performs two critical tasks: deploying a benign application to maintain the illusion of legitimacy and extracting an encrypted archive containing the malware payload.”
The MSI package uses the Windows Installer’s CustomAction feature to execute malicious code. Upon execution, it decrypts and deploys key components, including:
libcef.dll(PNGPlug Loader): A 220MB file inflated with junk code to evade detection.down.exe: A legitimate application masking malicious activities.aut.pngandview.png: Malicious payloads masquerading as PNG images.
The PNGPlug loader is responsible for initiating the attack, decrypting payloads, and injecting malicious processes into memory. Intezer explains, “The use of .png file extensions for malicious payloads is a key stealth tactic and inspired the name PNGPlug.”
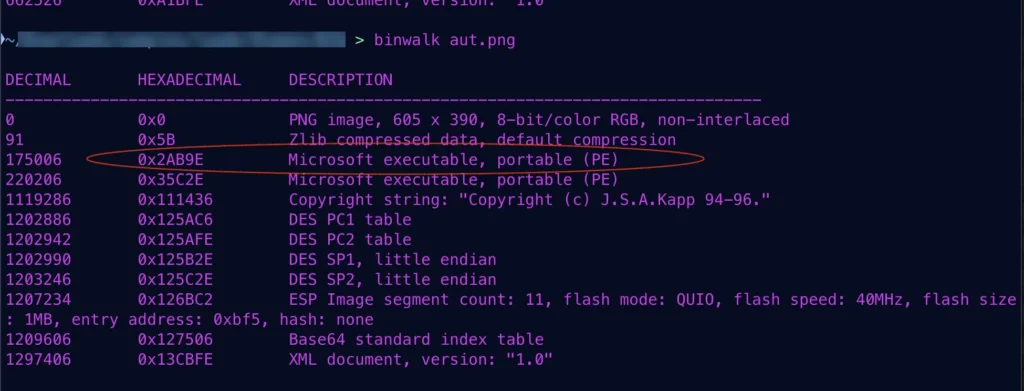
ValleyRAT, the primary malware deployed in this campaign, is designed for stealth and persistence. It leverages:
- Memory-based Shellcode Execution: Reducing its file footprint to evade detection.
- Privilege Escalation: Gaining elevated system access for further exploitation.
- Scheduled Tasks and Registry Modifications: Ensuring persistence on infected systems.
“The malware’s stages include initial execution, deployment of obfuscated shellcode, and a loader module that fetches additional malicious components from its command-and-control (C2) server,” the report notes.
The Silver Fox APT group, known for its espionage operations, is behind this campaign. They employ sophisticated tactics, including:
- Phishing Techniques: Using trojanized files and SEO-optimized websites to lure victims.
- Espionage Tools: Deploying malware like ValleyRAT and Gh0st RAT for surveillance and data exfiltration.
Intezer’s researchers link the campaign to Silver Fox with high confidence, citing victimology, malware infrastructure, and tactics.
The PNGPlug and ValleyRAT campaign exemplifies the adaptability and persistence of APT groups like Silver Fox. Intezer concludes, “This flexibility underscores the evolving nature of the threat landscape, emphasizing the urgent need for advanced detection and prevention mechanisms to counter these stealthy and persistent attacks.”