Silver 0.1 RC releases: Mass scan IPs for vulnerable services
Silver
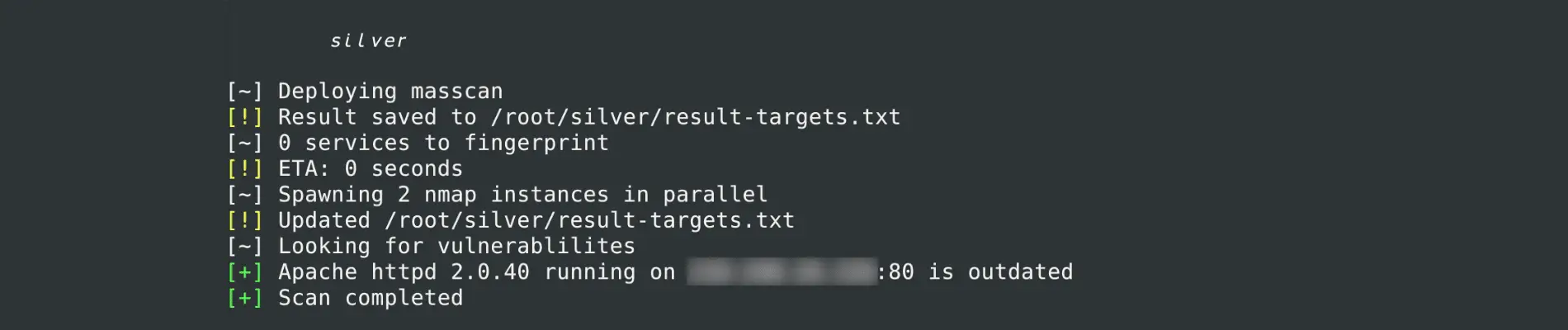
Mass Vulnerability Scanner
masscan is fast, nmap can fingerprint software and vulners is a huge vulnerability database. Silver is a front-end that allows complete utilization of these programs by parsing data, spawning parallel processes, caching vulnerability data for faster scanning over time and much more.
Features
- Resumable scanning
- Slack notifcations
- multi-core utilization
- Vulnerability data caching
- Smart Shodan integration*
*Shodan integration is optional but when linked, Silver can automatically use Shodan to retrieve service and vulnerability data if a host has a lot of ports open to save resources. Shodan credits used per scan by Silver can be throttled. The minimum number of ports to trigger Shodan can be configured as well.
Changelog v0.1 RC
- bug fixes
- support for hostnames
- save nmap’s output as well
- disable host discovery in nmap
- –rate option for controlling masscan’s pps rate
Install
Requirement:
git clone https://github.com/s0md3v/Silver.git cd Silver pip3 install -r requirements.txt
Configuration
Slack WebHook, Shodan API key and limits can be configured by editing respective variables in /core/memory.py
Setting up Slack notifications
- Create a workspace on slack, here
- Create an app, here
- Enable WebHooks from the app and copy the URL from there to Silver’s /core/memory.py file.
Use
Note: Silver scans all TCP ports by default i.e. ports 0-65535.
Scan host(s) from command line
python3 silver.py 127.0.0.1 python3 silver.py 127.0.0.1/22 python3 silver.py 127.0.0.1,127.0.0.2,127.0.0.3
Scan top ~1000 ports
python3 silver.py 127.0.0.1 --quick
Scan hosts from a file
python3 silver.py -i /path/to/targets.txt
Set max number of parallel nmap instances
python3 silver.py -i /path/to/targets.txt -t 4
Copyright (C) 2019 s0md3v
Source: https://github.com/s0md3v/





