SlackPirate – Slack Enumeration and Extraction Tool
This is a tool developed in Python which uses the native Slack APIs to extract ‘interesting’ information from a Slack workspace given an access token.
As of May 2018, Slack has over 8 million customers and that number is rapidly rising – the integration and ‘ChatOps’ possibilities are endless and allow teams (not just developers!) to create some really powerful workflows and Slack bot/application interactions.
As is the way with corporations large and small, it is not unusual for tools such as Slack to fly under the Information Security governance/policy radar which ultimately leads to precarious situations whereby sensitive and confidential information end up in places they shouldn’t be.
The purpose of this tool is two-fold:
- Red-teamers can use this to identify and extract sensitive information, documents, credentials, etc from Slack given a low-privileged account to the organisation’s Workspace. This could allow an attacker to pivot on to other systems and/or gain far more intimate knowledge and inner-workings of corporate systems/applications
- Blue-teamers can use this to identify and detect sensitive information on the Workspace that perhaps shouldn’t exist on there in the first instance. Blue-teamers can use this information for internal training and awareness purposes by demonstrating the output of the tool and the type of ‘things’ that could be used and abused by (internal as well as external) attackers.
The tool allows you to easily gather sensitive information for offline viewing at your convenience.

Information Gathering
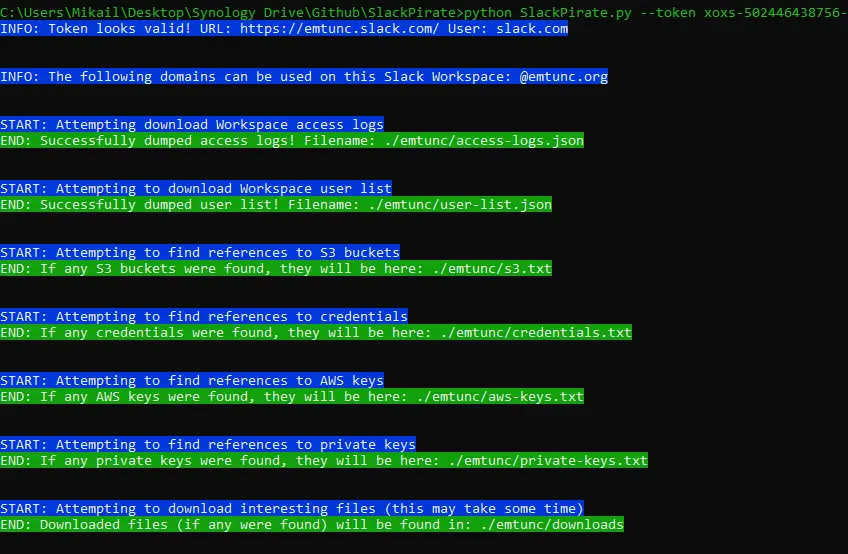
The tool uses the native Slack APIs to extract ‘interesting’ information and looks for the following information, today:
- Print to standard output the domains (if any) that are allowed to register for the Workspace – I’ve seen stale, old and forgotten domains here that can be purchased and used to register for the Workspace
- Links to S3 buckets
- Passwords
- AWS Access/Secret keys
- Private Keys
- References to links and URLs that could provide further access to sensitive materials – think: Google Docs, Trello Invites, links to internal systems, etc
- Files which could contain sensitive information such as .key, .sh, the words “password” or “secret” embedded in a document, etc
Changelog v0.20
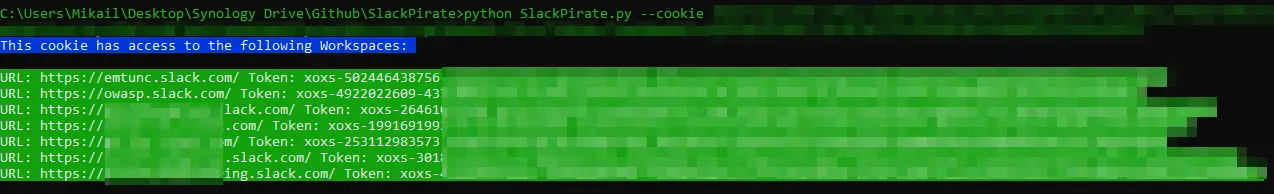
You can now run SlackPirate in interactive mode by using the –interactive flag. The tool will run you through the process of copy/pasting the Slack Cookie/Token, choosing a Workspace (or multiple!) and lastly, choosing scan options.
Download && Use
Copyright (C) 2018 emtunc