In the ever-evolving world of cybersecurity, a new, potent threat has surfaced, challenging the perceived boundaries of hardware security. This threat, known as SLAM (Spectre based on Linear Address Masking), emerges from the intersection of hardware features intended for memory efficiency and the notorious Spectre vulnerabilities. SLAM illustrates a pivotal shift in the landscape of transient execution attacks, exploiting vulnerabilities in both Intel and AMD CPUs that were previously considered secure against such attacks.

The genesis of SLAM lies in the features introduced by Intel and AMD for optimizing memory usage, namely Linear Address Masking (LAM) and Upper Address Ignore (UAI). These features were designed to enhance memory safety checks in software by allowing the use of untranslated bits of 64-bit linear addresses for storing metadata. However, researchers from VUSec discovered that instead of bolstering security, these features inadvertently expanded the Spectre attack surface.
SLAM diverges from traditional Spectre attacks by exploiting “unmasked” Spectre gadgets. These gadgets, unlike their “masked” counterparts, encode high-entropy secrets as dereferenced pointers, a technique previously considered impractical for exploitation due to challenges in transmitting the secret over microarchitectural covert channels. SLAM, however, overcomes these challenges by employing a novel covert channel based on address translation, exploiting modern Translation Lookaside Buffers (TLBs), and leveraging the LAM/UAI features to bypass canonicality checks. This innovative approach allows SLAM to target generic Spectre gadgets that are abundant in high-value targets like the Linux kernel.
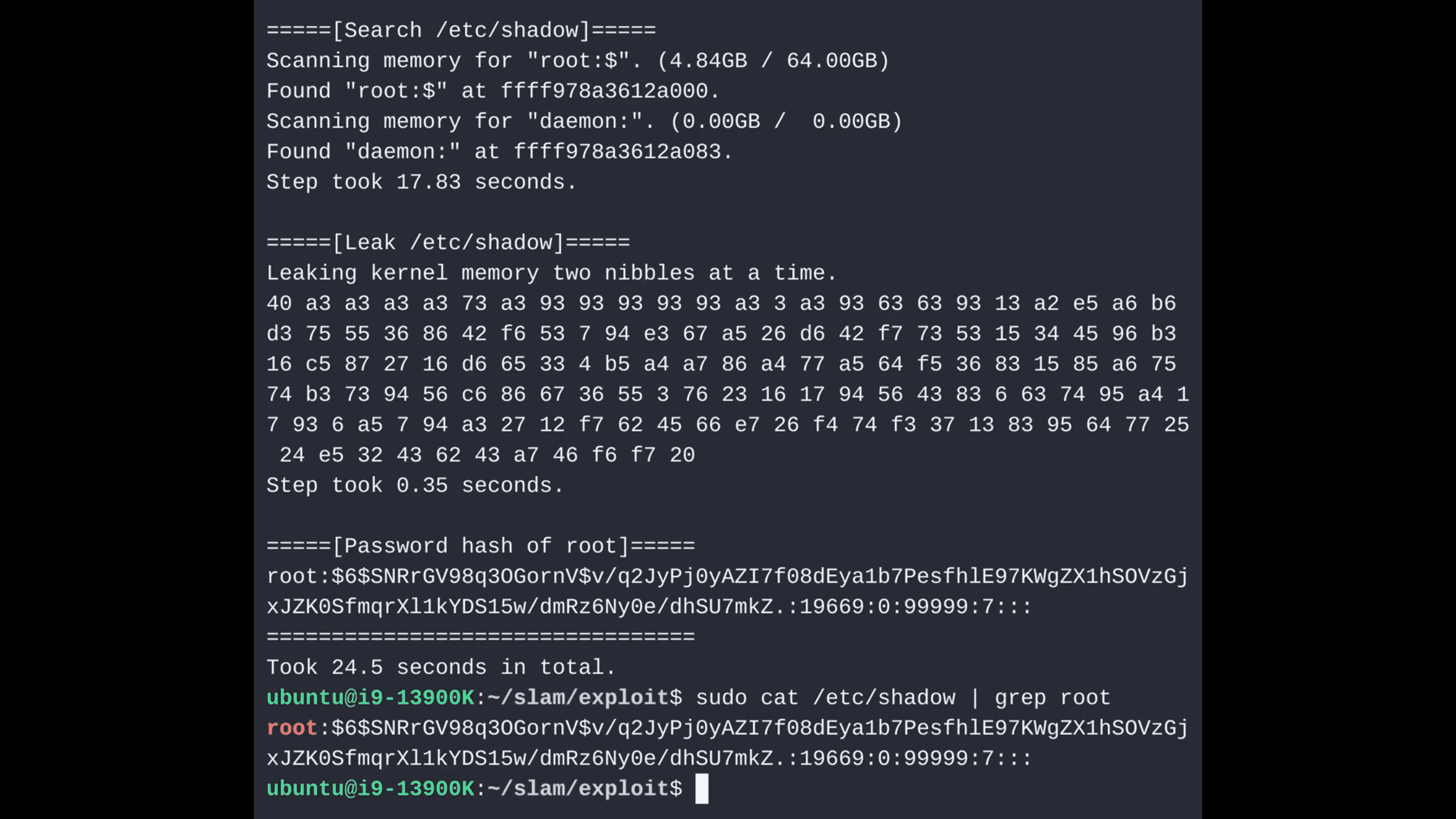
At its core, SLAM is a methodical process of data exfiltration, beginning with the expansion of the leakage surface from kernel pointers to user pointers. This expansion is achieved by exploiting the address translation process, which precedes Supervisor Mode Access Prevention (SMAP) checks. The crux of SLAM is its ability to manipulate the covert channel to support noncanonical address translation, a feature made possible by the LAM/UAI functionality in next-generation CPUs.
To transform this covert channel into a practical tool for leaking secrets, SLAM implements techniques for reducing entropy. This is accomplished by sliding the pointer referencing the secret data across iterations, thus revealing the secret one byte at a time. Additionally, SLAM employs just-in-time reload buffer remapping to manage the enormous potential address space, ensuring efficient data retrieval. These techniques collectively enable SLAM to leak high-entropy secrets in a byte-by-byte fashion, similar to classic masked Spectre gadgets.
In short, the following CPUs are affected:
- Existing AMD CPUs vulnerable to CVE-2020-12965;
- Future Intel CPUs supporting LAM (both 4- and 5-level paging);
- Future AMD CPUs supporting UAI and 5-level paging;
- Future Arm CPUs supporting TBI and 5-level paging.
The emergence of SLAM represents a significant new chapter in the ongoing narrative of Spectre vulnerabilities. It underscores the complex interplay between hardware features intended for performance optimization and the unforeseen security risks they can introduce. SLAM’s ability to exploit unmasked Spectre gadgets in modern kernels, including those equipped with the latest security defenses, highlights the ever-present need for vigilance in the realm of cybersecurity.