SleuthQL: Burp History parsing tool to discover potential SQL injection points
SleuthQL is a python3 script to identify parameters and values that contain SQL-like syntax. Once identified, it will then insert SQLMap identifiers (*) into each parameter where the SQL-esque variables were identified.

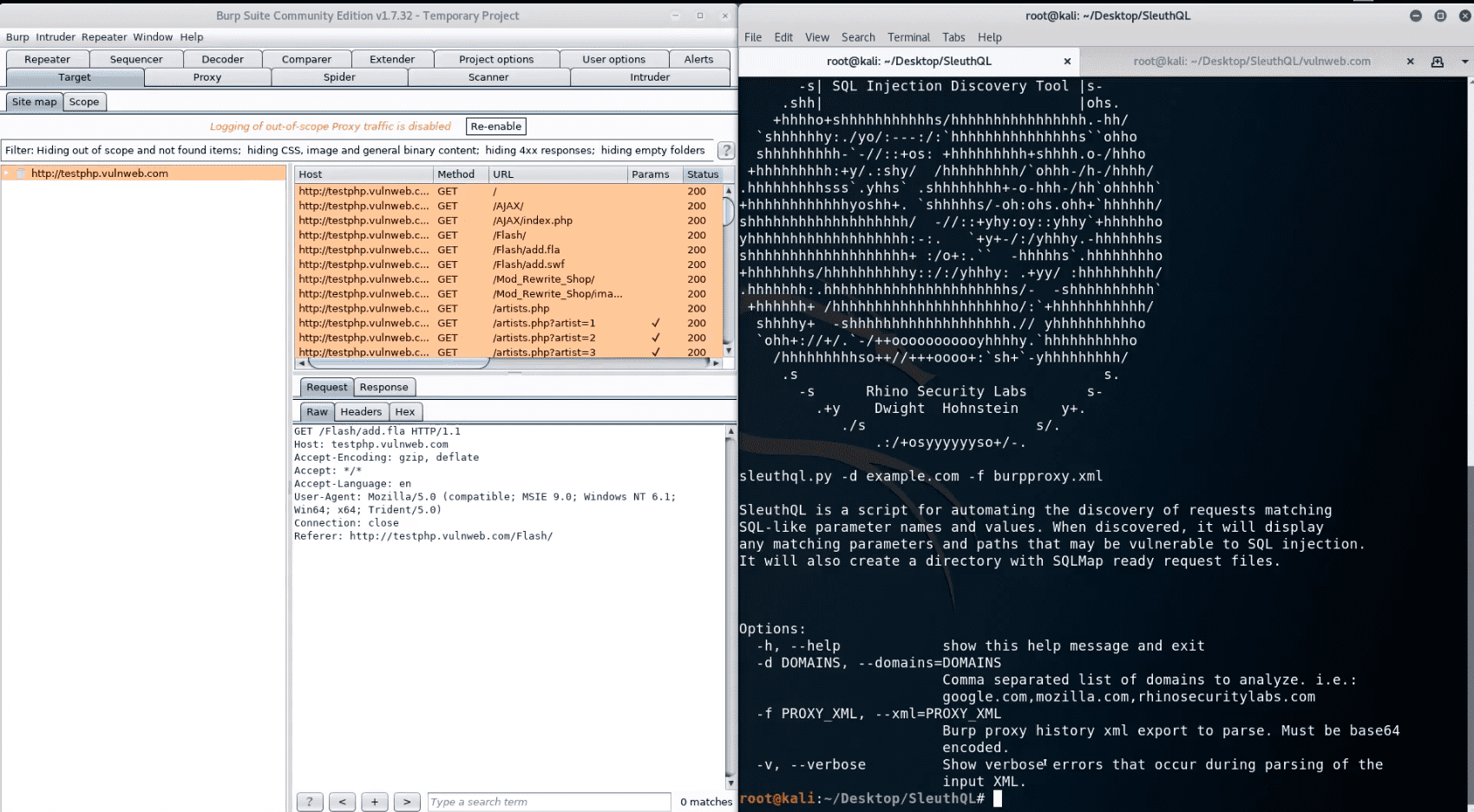
SleuthQL requires an export of Burp’s Proxy History. To gain this export, simply navigate to your proxy history tab, highlight every item and click “Save Items”. Ensure that each request is saved using base64 encoding. When SleuthQL scans the proxy history file, outside of the regular URL parameters, it will be able to identify vulnerable parameters from the following request content-types:
- application/json
- application/x-www-form-urlencoded
- multipart/form-data
There are cases where this tool will break down. Namely, if there are nested content-types (such as a base64 encoded parameter within JSON data), it will not be able to identify those parameters. It also does not cover Cookies, as too often something such as CloudFlare will flag a parameter we’re not interested in.
Burp Pro’s scanner is great but isn’t as full featured as SQLMap. Thus, if we can prioritize requests to feed into SQLMap in a batch-like manner and look for results this way, we can increase the detection rate of SQL injection.
Download
git clone https://github.com/RhinoSecurityLabs/SleuthQL.git
Use
Output Files
For each potentially vulnerable request, the SQLMap parameterized request will be saved under $(pwd)/$domain/ as text files.
Demo
Copyright (c) 2018 djhohnstein
Source: https://github.com/RhinoSecurityLabs/