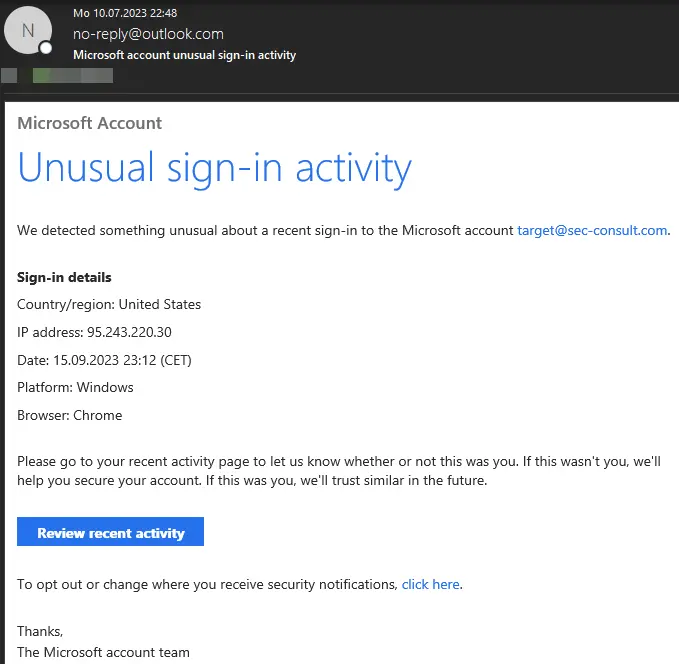
Using HTML with SMTP smuggling to create a convincing phishing e-mail
In the ever-evolving landscape of cyber threats, a new attack technique named SMTP Smuggling has emerged, threatening the integrity of email communication worldwide. Discovered by Timo Longin, renowned for his expertise in DNS attacks, and SEC Consult, part of the digital transformation company Eviden, this technique exploits vulnerabilities in the Simple Mail Transfer Protocol (SMTP) to send out spoofed emails that can bypass traditional authentication mechanisms.
SMTP, the backbone protocol for sending, receiving, and relaying emails, is now at the center of this new cybersecurity challenge. SMTP Smuggling capitalizes on discrepancies in how outbound and inbound SMTP servers interpret message data endings. This variance allows attackers to “smuggle” spoofed emails through, making them appear as if they originate from trusted domains.

This technique is not just a theoretical concern. An alarming analysis revealed that SMTP Smuggling could enable attackers to spoof emails from millions of domains, including giants like Microsoft, Amazon, PayPal, eBay, GitHub, Outlook, Office365, Tesla, and Mastercard. Demonstrations included sending emails that appeared to come from ‘admin(at)outlook.com’, highlighting the severity of the threat.
Upon discovery, vendors such as GMX (Ionos), Microsoft, and Cisco were alerted. GMX acted swiftly, patching the vulnerability in about ten days. Microsoft, assigning a moderate severity rating to the issue, released a patch in mid-October. Cisco, however, does not recognize this as a vulnerability, suggesting configuration changes to mitigate the threat.
Notably, some free and open-source mail transfer agents are susceptible to SMTP Smuggling. This includes popular software like Postfix, sendmail, and exim, all of which have been assigned CVE identifiers – CVE-2023-51764 (Postfix), CVE-2023-51765 (sendmail), and CVE-2023-51766 (Exim).
While SMTP Smuggling can bypass email authentication mechanisms like SPF, DKIM, and DMARC, it’s important to note that spam filters may still catch these emails based on content or other factors. However, this doesn’t diminish the importance of addressing this technique directly.
For system administrators and IT professionals, the immediate steps include:
1. Updating Software: Ensuring mail servers are running the latest versions with patches applied.
2. Configuration Review: Checking and modifying configurations, especially in systems identified as vulnerable, like Cisco Secure Email instances.
3. Enhanced Monitoring: Keeping an eye on email traffic for signs of SMTP Smuggling and other unusual activities.
4. Education and Awareness: Informing users about the potential of spoofed emails, even from seemingly trustworthy sources.
SMTP Smuggling represents a significant shift in email-based attack strategies, underlining the necessity for continuous vigilance in the cybersecurity world. As attackers find novel ways to exploit longstanding protocols, the incident reinforces the importance of collaborative research and proactive security measures in the digital era.
The discovery of SMTP Smuggling is a reminder of the dynamic nature of cyber threats. In the face of such sophisticated techniques, staying informed, upgrading systems, and adopting best practices in email security are more crucial than ever for organizations and individuals alike.