
A new analysis by Trend Research has shed light on intrusion techniques involving the malware-as-a-service (MaaS) framework known as SocGholish, highlighting its critical role in facilitating the distribution of RansomHub ransomware.
According to the analysis, the threat actor cluster identified as “Water Scylla” uses a multi-stage approach to propagate SocGholish, primarily through compromised legitimate websites. These websites are infected with malicious scripts that redirect visitors to fraudulent browser update pages, deceiving users into downloading malware disguised as legitimate updates.
SocGholish is characterized by its highly obfuscated JavaScript loader, which employs a range of evasion techniques that enable it to bypass traditional signature-based detection methods effectively. The primary method of propagation for SocGholish involves the compromise of legitimate websites.
Trend Research emphasized, “SocGholish is characterized by its obfuscated JavaScript loader, which uses various evasion techniques to bypass traditional detection methods, primarily propagating through compromised legitimate websites.”
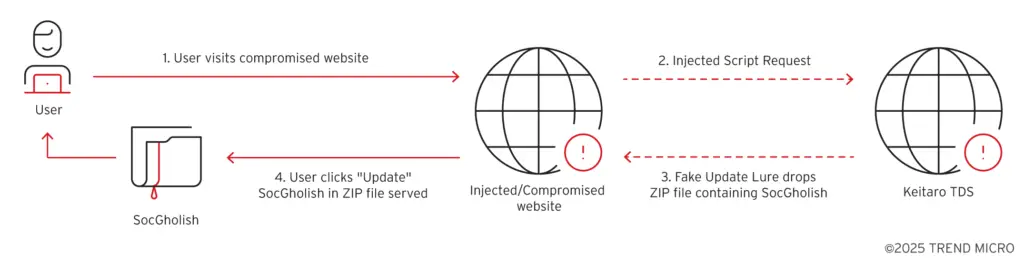
Threat actors inject malicious scripts into these sites to hijack user traffic. When users visit these compromised sites, they are redirected to deceptive webpages that masquerade as legitimate browser update notifications. Through social engineering tactics, users are convinced to download a malicious ZIP file. This file contains a JavaScript file, which is the SocGholish loader.
Water Scylla collaborates with threat actors operating rogue Keitaro Traffic Distribution System (TDS) instances to distribute SocGholish Payloads. These TDS instances are commercial traffic distribution systems that deliver SocGholish and filter unwanted traffic from sandboxes and researchers. Trend Micro telemetry from 2025 alone has identified thousands of compromised websites injected with scripts pointing to these malicious TDS domains, which may lead to SocGholish infections depending on the geolocation of the visitor.
The complex intrusion set Water Scylla is composed of multiple stages that involve compromised websites, collaboration with threat actors operating malicious Keitaro TDS instances, SocGholish payload delivery, and post-compromise activity that leads to RansomHub. As of the start of 2025, SocGholish detections have been highest in the United States, with government organizations among the most affected.
The SocGholish loader is highly versatile and capable of executing arbitrary tasks as directed by its operators. It can download and execute malicious payloads, including backdoor components and stealer routines. It can also exfiltrate sensitive information, collecting and sending data from infected systems back to its command-and-control (C&C) infrastructure. Additionally, it can execute arbitrary commands, allowing threat actors to perform a wide range of malicious activities on the compromised system. These backdoors provide threat actors with persistent access to infected systems, facilitating further exploitation and payload deployment.
SocGholish’s key role in enabling initial access for ransomware warrants the attention of defenders to thwart attacks. This particular cluster deploys backdoor components to enable initial access for RansomHub ransomware-as-a-service (RaaS) affiliates. Ransomhub is a top ransomware player in terms of the number of organizations impacted by data breaches, just behind Akira in second place and CLOP in first, and SocGholish a key enabler of these attacks.
The analysis provides a detailed breakdown of the intrusion techniques and tools used by Water Scylla:
- Compromised Websites and Malicious Scripts: Threat actors inject malicious scripts into legitimate websites to redirect user traffic to fake update pages.
- Keitaro TDS: Rogue Keitaro Traffic Distribution System instances are used to deliver SocGholish payloads and filter unwanted traffic.
- Fake Update Pages: Users are lured to fake update pages that drop ZIP files containing the SocGholish payload.
- JavaScript Loader: The SocGholish loader, delivered via a malicious JavaScript file, is characterized by its obfuscation and evasion techniques.
- Backdoor Components: SocGholish drops second-stage payloads, including backdoor components, to provide persistent access to infected systems.
- Python Backdoor: A Python-based backdoor is deployed to gain persistent access, relay connections, and facilitate command and control, data exfiltration, and ransomware deployment.
- Credential Access and Exfiltration Tools: The threat actors use various tools and techniques to steal sensitive credentials, including extracting app-bound encryption keys from browsers and copying login data.
- certutil Utility: The certutil utility is abused to extract registry hives from Volume Shadow Copies.
- Reverse Shell Deployment: SSH reverse shells with port forwarding are deployed for command and control and data exfiltration.
- NIRCMD: The NIRCMD tool is downloaded and executed to collect screenshots from compromised environments.
The analysis indicates that the threat actors engage in hands-on keyboard interaction, performing various tasks such as:
- Collecting detailed system and network information.
- Enumerating user accounts and groups.
- Searching for files containing credentials.
- Extracting Wi-Fi profiles.
- Connecting to multiple hosts using compromised credentials and deploying BAT files for further exploitation.
Trend Research’s most recent tracking of SocGholish C&C infrastructure shows 18 active C&C servers, whose domains are rotated at least once per week – with some fluctuations in the frequency of domain rotation. This technique, known as domain shadowing, is desirable from a threat actor perspective, because it enables them to leverage the reputation of more mature domains which are less likely to be blocked by automated detection systems.
Trend Research emphasizes critical preventive strategies, urging organizations to deploy advanced detection and response solutions, enhance logging and network monitoring, secure CMS and web applications, and isolate outdated systems.
Related Posts:
- SocGholish Malware: The Silent Threat Lurking in Fake Browser Updates
- SocGholish Campaign Targets Business Networks via Fake Browser Updates
- 10,000 WordPress Websites Compromised to Deliver macOS and Windows Malware
- Fake Browser Updates Lead to Malicious BOINC Installations
- Malicious Go Packages Target Developers with Hidden Loader Malware on Linux and macOS