A recent report from G Data stated that the recently discovered remote-access SocketPlayer malware is using a particular library, socket.io, “This particular library was designed for use in web applications that require real-time communication between two parties and which are reliant of bi-directional communication” that allows operators to interact with infected devices “without needing it to take the first step“.
The SocketPlayer backdoor differs from most bank trojans, backdoors, and keyloggers that use typical one-way communication systems. By using the socket.io library, real-time two-way communication between applications can be achieved. According to this feature, malware handlers no longer need to wait for the infected device to initiate communications, the attacker can contact the infected computer.
Allegedly, the backdoor SocketPlayer once installed successfully on the compromised machine can receive the operator’s commands and perform various operations such as sniffing, screenshots, grabbing and running code. The researchers also found that SocketPlayer can also selectively use other functions, for example, like a keylogger, although there is no actual keylogger function in the back door. At present, it seems that there has been no specific use.
The backdoor SocketPlayer infection path starts with the downloader’s sandbox detection. If it passes the test, the downloader downloads an executable file and decrypts it, and then uses the Invoke method to run the decryption program in memory.
The called program will create a socket connection for the host (Host is http://93.104.208.17:5156/socket.io), at the same time, create a registry key that implements persistence. Next check if there is a Process Handler/Folder, if not, you need to create one. After that, you also need to create an autostart key with the value “Handler”. Also, SocketPlayer downloads another downloadable SocketPlayer executable that decrypts and runs in memory.

G Data’s security researchers discovered two variants of the SocketPlayer backdoor during the study:
- Thefirst variant is a ~100KB file which does exactly what a typical downloader does – downloading a file
and executing it.- Same as variant 1, there is also an old version and a new version. Both versions have a similar initial routine as in 2. Initial routine. The old version only uses the C:\Users\USERNAME\Music path and downloads the data from hxxp://173.249.39.7:1337/uploads/excutbls/ with the filename specified via socket.io from the
server.
Security researchers noticed a series of changes between the two variants of SocketPlayer, including:
- The c2 port has changed from 3000 to 7218
- The file location changed from C:\Users\USERNAME\Music\Player\Player.exe to
C:\Users\USERNAME\Music\Media Player\Player.exe- The information that is sent in the initial routine changed a bit. In the old version[1] the
author sends the string “,1.1,1” to the c2. In the new version the program sends “,1.2,1”,
telling the c2 that the new version runs on the machine.- To the commands Fdrive,fdir,smfdir,procs,prockil,gtscreen and kylgs the variable susrid is
added to be sent to the server. This is done to identify the infected systems better.- The functionality stscrnpercnt is added. This feature assists the gtscreen function to set the
quality of the image.- The gtscreen function additionally to the susrid also sends the computer name with the
picture.- The storage location of upldex is changed to
C:\Users\User\AppData\Roaming\Microsoft\Windows\Templates. An autostart key to the
registry is added. The downloaded file is also executed.- The kylgs function also switched to use the above path to read the file klsetup.txt.
- The destt function additionally checks if the following path and files are available. If so, it
deletes them. C:\Users\USERNAME\AppData\Roaming\Process Handler
C:\Users\USERNAME\AppData\Roaming\Process Handler\Handler.exe,
C:\Users\User\AppData\Roaming\Microsoft\Windows\Templates\Image.exe and
C:\Users\User\AppData\Roaming\Microsoft\Windows\Templates\Media.exe.
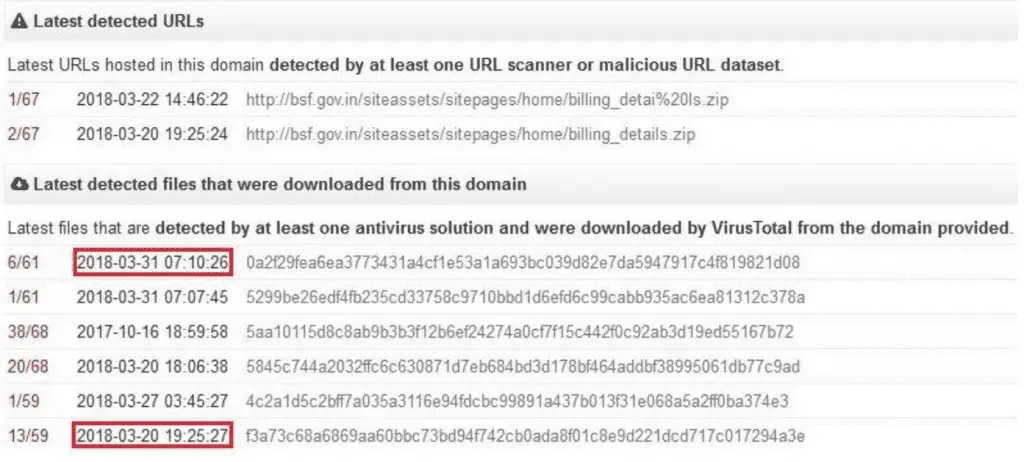
The report shows that a sample of known malware was distributed through an Indian website, but it is unclear how the back door spreads. However, whether the site was used for infection or just for mirroring, it is clear that the malware has not been noticed for a long time.
Source, Image: gdatasoftware