solarflare: Credential Dumping Tool for SolarWinds Orion
solarflare
Credential Dumping Tool for SolarWinds Orion.
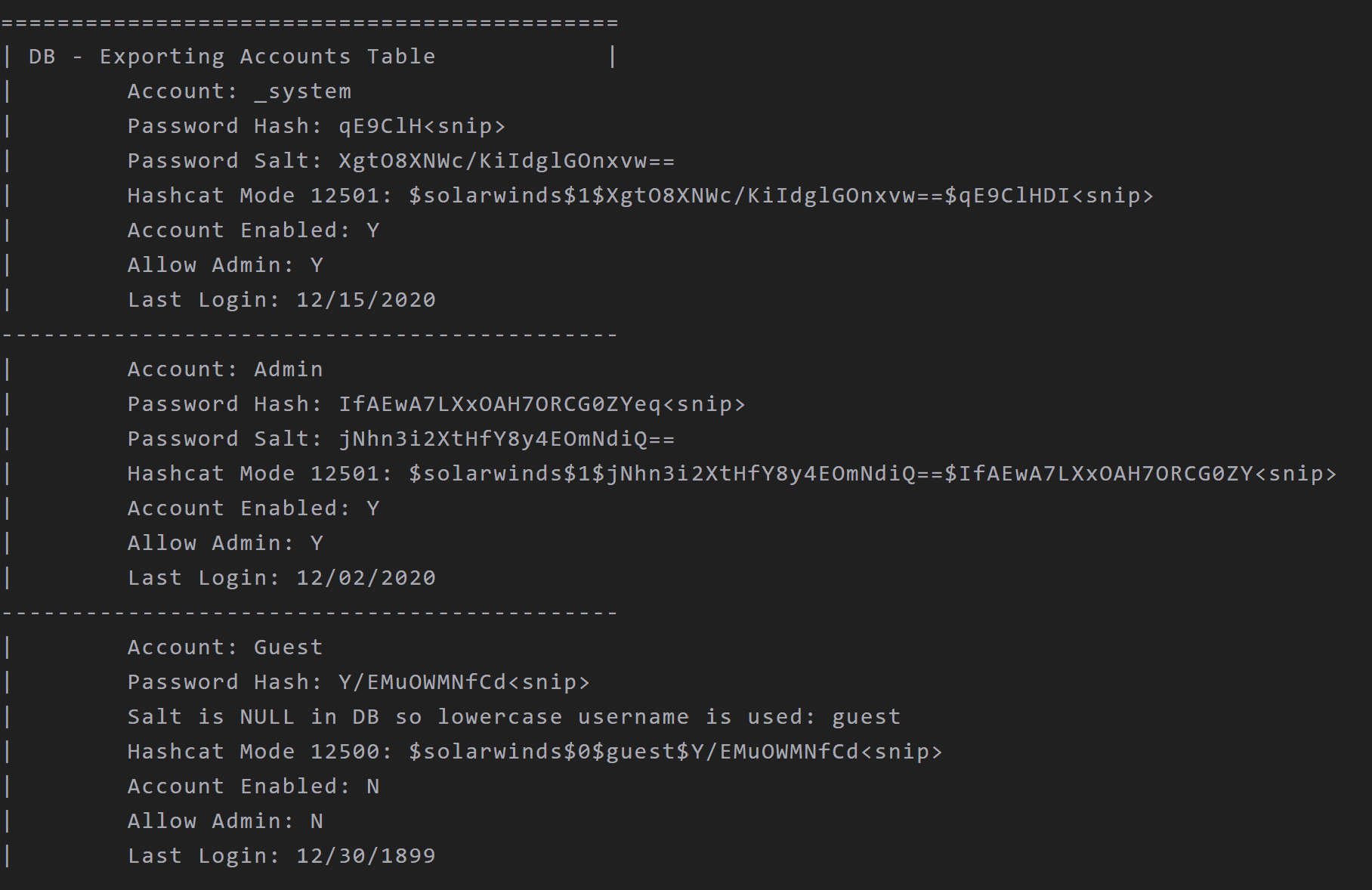
SolarFlare is a Authentication Audit / Password dumping tool originally designed for Red Team engagements, but can be used to audit the exposure SolarWinds Orion systems pose to an organization.
Function
Erlang Cookie
This function simply reads the
.erlang.cookiefile from theProgramDatadirectory where it’s stored. You can find this file at%PROGRAMDATA%\SolarWinds\Orion\RabbitMQ\.erlang.cookie. It is a randomized string created during installation. This string does not change as far as I have observed. This string is also stored in the database.RSA Key
The “SolarWinds-Orion” RSA key is stored in the SYSTEM/LocalMachine certificate store and is generated during install. This certificate is used as the PKI based encryption/decryption for credentials stored int the database. I do not know why this certificate is generated in a way that makes it exportable. But, it doesn’t not need to be exportable for the decryption to be used. This certificate can be used along with the Atradis tool on Github to decrypt credentials from the database, offline.
DAT file
The DAT file is a recent (2019/2018?) additional encryption that was added to SolarWinds Orion. The file is also located in the ProgramData directory:
%PROGRAMDATA%\SolarWinds\Keystorage\CryptoHelper\default.dat. This file is encrypted with the SYSTEM/LocalMachien DPAPI master keys. Once decrypted, much like the exporting of the RSA private key, it can be used to decrypt the AES based encrypted accounts in the database, offline.More…
Download
Copyright (c) 2020, Rob Fuller
All rights reserved.





