SCWF: CTF tool for identifying, brute forcing and decoding encryption schemes
Solve Crypto With Force (SCWF)
CTF tool for identifying, brute forcing and decoding encryption schemes in an automated way.
Click here for the live version (use Chrome).
Crypto CTF (sub)challenges can roughly be categorized as follows:
- Weak implementation/configuration of strong cryptographic schemes (e.g. RSA based challenges)
- Weak cryptographic cipher usage (e.g. Vigenère)
- Obfuscation (e.g. Skip, Railfence)
- Encodings (e.g. Base32, Morse)
While case 1 is arguably the most fun to solve, cases 2 to 4 are still used in CTFs, i.e. CyberLympics. It can take a lot of time figuring out what it exactly is. This is especially true since no available tool does the identification of which cipher/encoding is used.
Solve Crypto With Force (SCWF) was created in 2014 as a “scratch your own itch” to automate the identification and decryption of the above-mentioned cases 2 to 4 in certain CTF’s (cough CyberLympics). This allowed brainpower to be used for other, more fun challenges to be solved.
SCWF uses statistical analysis to identify which encoding or encryption is used and grade the output using a dictionary. It will grade each output by identifying English words, links and flags. You input a challenge in the top textarea and it will make a graph in an attempt to solve it.
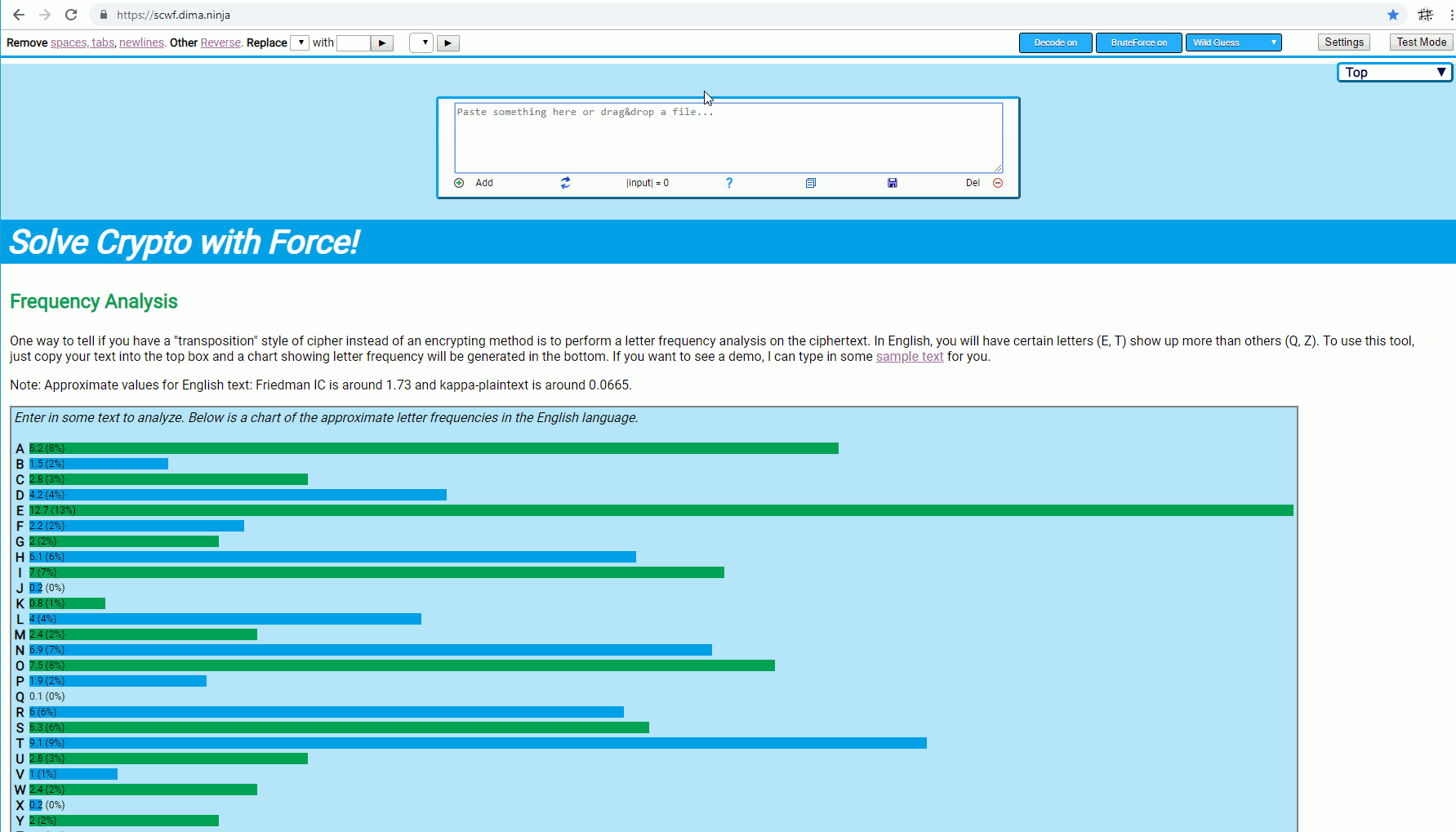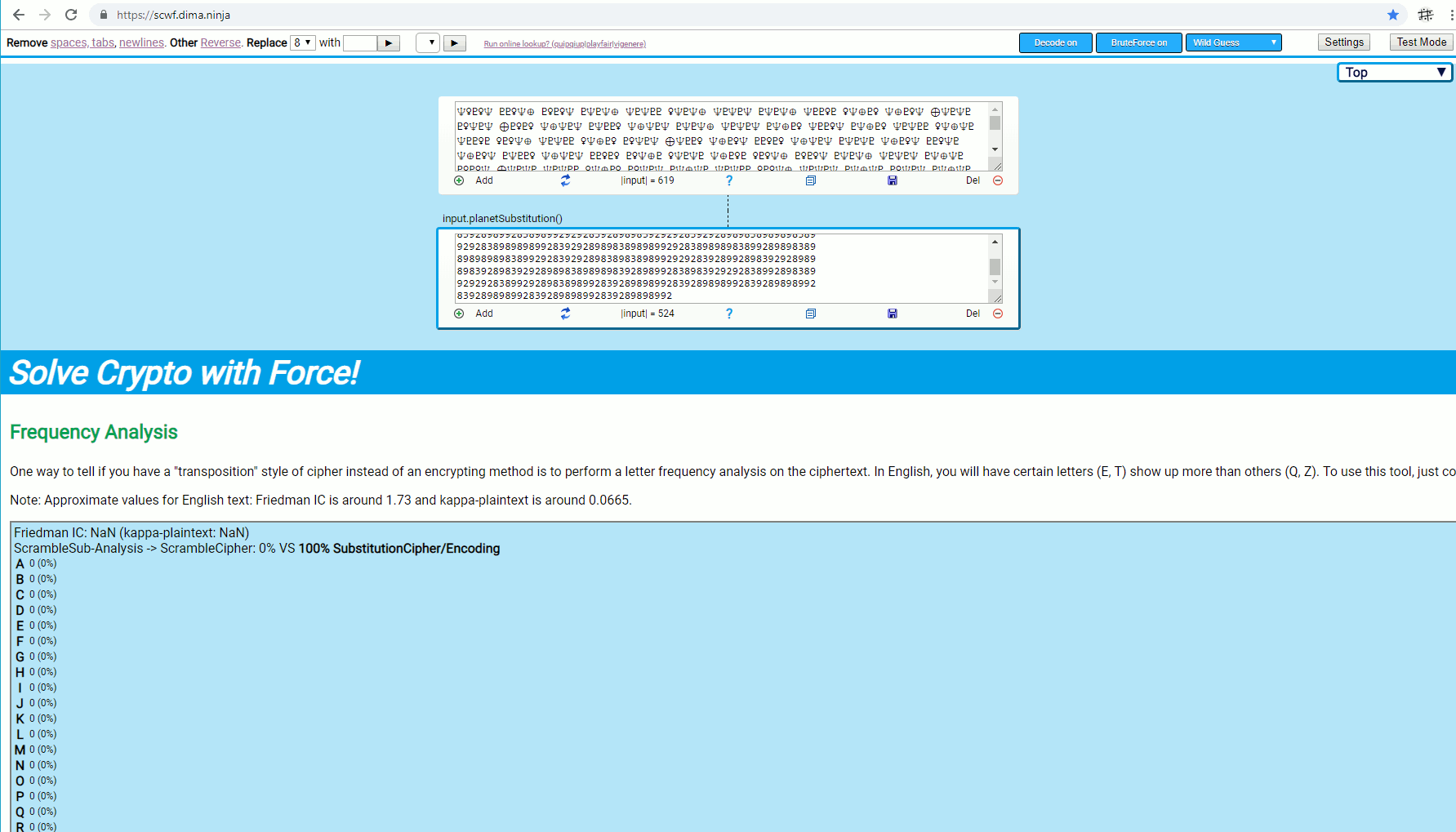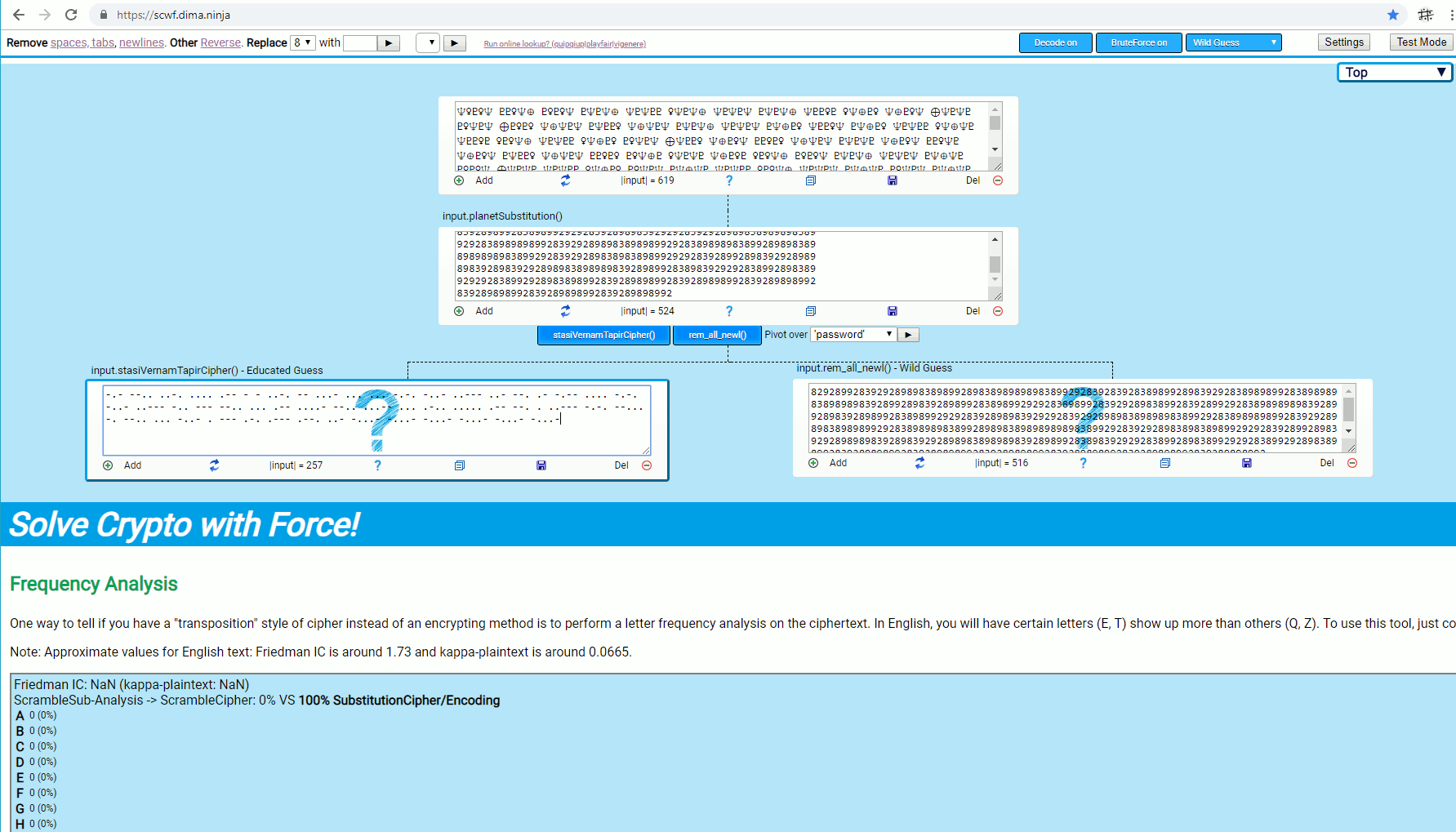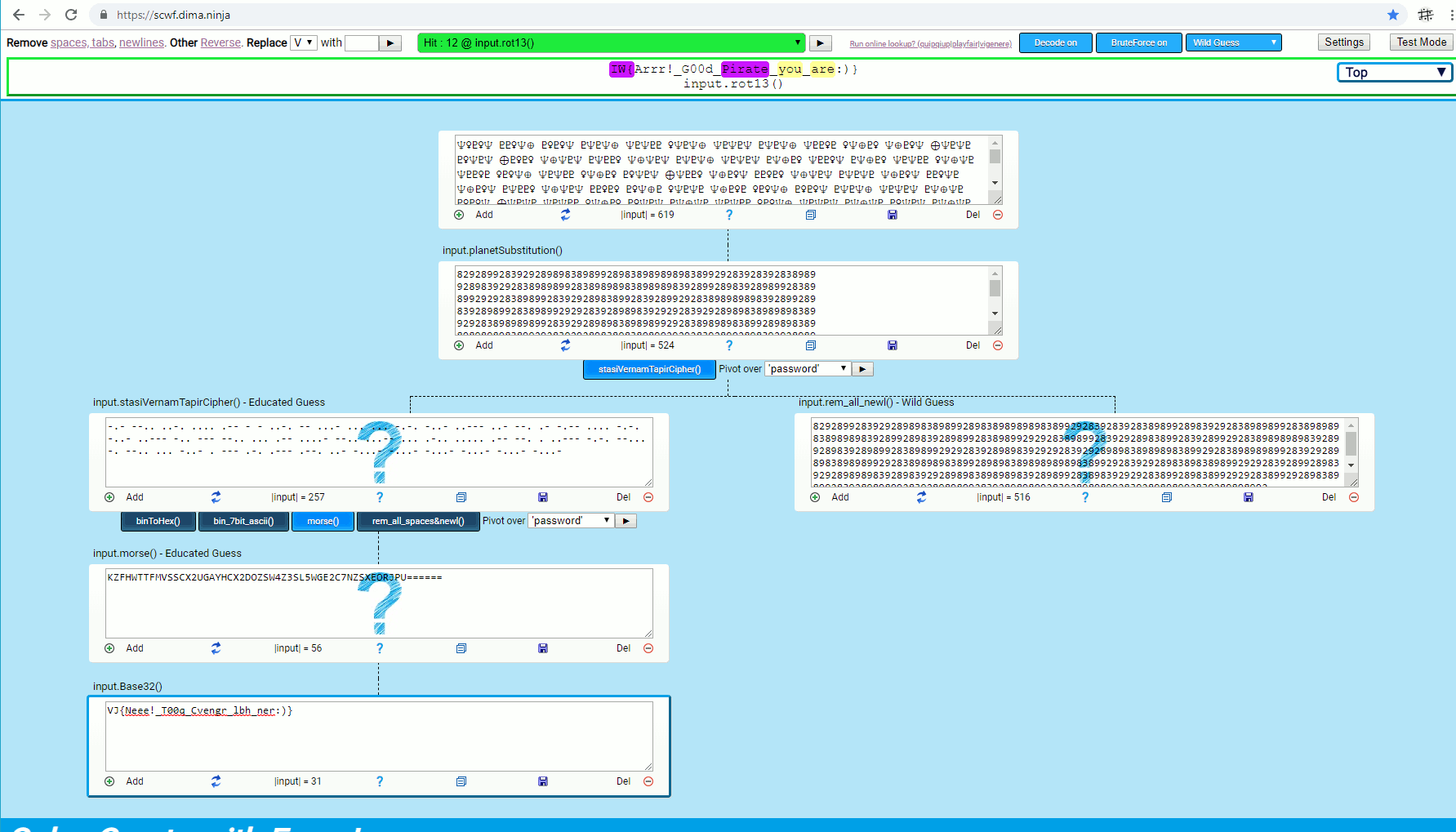 A graph that is created within a few seconds from this example input: 2016 Internetwache CTF – crypto pirate 50
A graph that is created within a few seconds from this example input: 2016 Internetwache CTF – crypto pirate 50
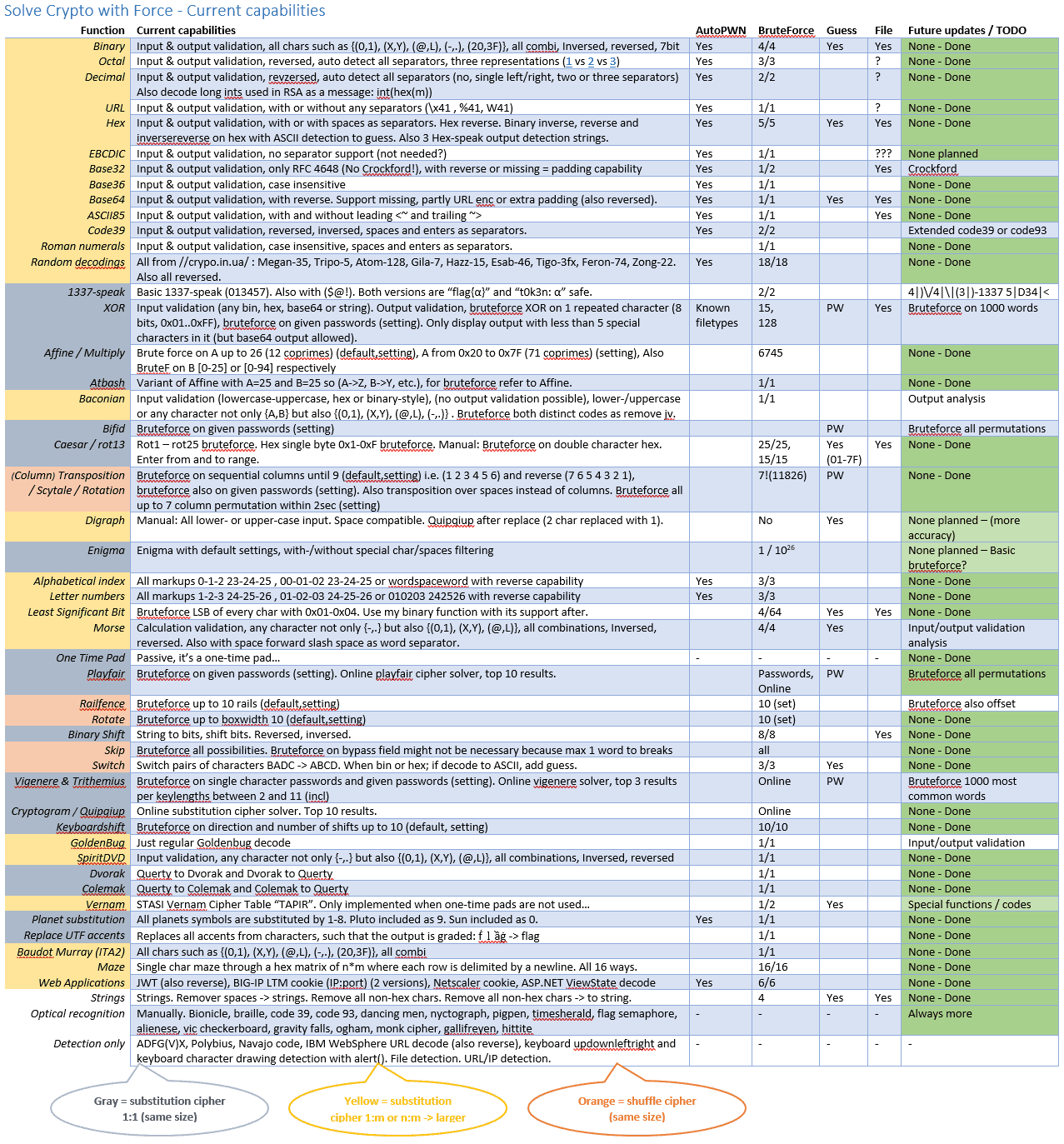
Currently, the following ciphers can be identified and solved fully or to a certain extent: 
Copyright (C) 2019 DaWouw





