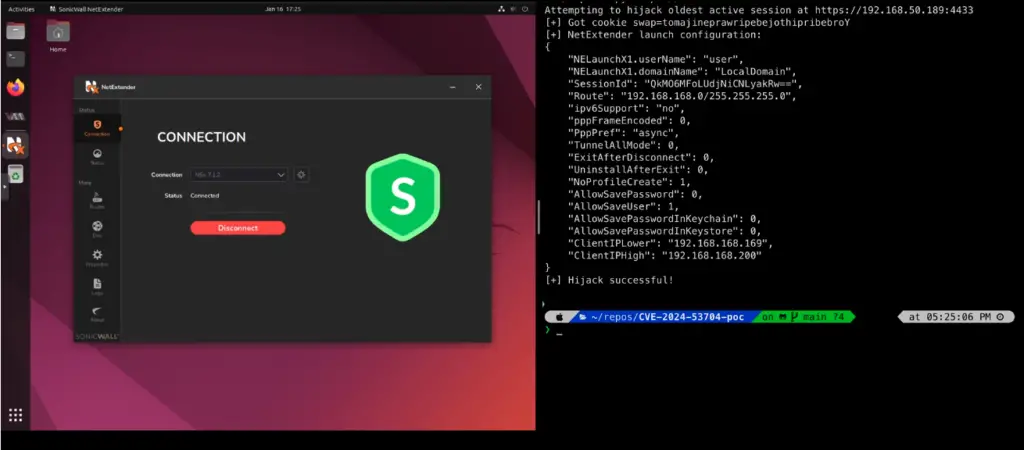
Source: Bishop Fox
A recently disclosed vulnerability in SonicWall firewalls, tracked as CVE-2024-53704, is now under active attack. This high-severity flaw allows unauthenticated attackers to bypass multi-factor authentication (MFA), access sensitive information, and disrupt VPN sessions.
The vulnerability, which resides in the SSLVPN authentication mechanism of SonicOS, was initially reported to SonicWall in early January. While a patch was released, the recent publication of proof-of-concept (PoC) exploit code by Bishop Fox has triggered a wave of attacks.
Arctic Wolf, a cybersecurity firm, has confirmed observing exploitation attempts in the wild, highlighting the urgent need for action. Attackers are leveraging this vulnerability to gain unauthorized access to networks, potentially leading to data breaches, ransomware deployment, and other malicious activities.
The following SonicWall firewall models running specific SonicOS versions are affected:
- Gen7 Firewalls: SonicOS versions 7.1.x (7.1.1-7058 and older) and 7.1.2-7019.
- Gen7 NSv: SonicOS versions 7.1.x (7.1.1-7058 and older) and 7.1.2-7019.
- TZ80: SonicOS version 8.0.0-8035.
SonicWall urges users to immediately upgrade their SonicOS firmware to the latest fixed versions:
- Gen7 Firewalls and Gen7 NSv: Upgrade to SonicOS 7.1.3-7015 or higher.
- TZ80: Upgrade to SonicOS 8.0.0-8037 or higher.
SonicWall SSL VPN SMA100 and SMA1000 series products are not affected by this vulnerability.
Additional Recommendations:
- Restrict SSLVPN access: Limit access to trusted sources or disable SSLVPN access from public networks.
- Follow patching and testing guidelines: Minimize potential operational impact by adhering to your organization’s patching procedures.
The availability of exploit code and active exploitation attempts make it crucial to take immediate action. Upgrading to the latest SonicOS version is the most effective way to protect your network from this threat. Delaying mitigation efforts could have severe consequences, including ransomware infections, data breaches, and business disruption.
Related Posts:
- SonicWall Issues Important Security Advisory for Multiple Vulnerabilities in SonicOS
- CVE-2024-53704 – Authentication Bypass in SonicOS: PoC Published
- SonicWall Confirms Critical CVE-2024-40766 Vulnerability Actively Exploited in the Wild
- Akira Ransomware Exploits SonicWall SSLVPN Flaw (CVE-2024-40766)
- CVE-2023-0656: unauthenticated Denial of Service vulnerability in SONICOS