
Cyble Research and Intelligence Labs (CRIL) has uncovered a multi-stage cyberattack campaign targeting the manufacturing industry. Leveraging advanced techniques and a combination of Lumma Stealer and Amadey Bot, this campaign demonstrates the increasing sophistication of modern threat actors.
The campaign begins with a spear-phishing email containing a deceptive LNK file disguised as a PDF document. According to CRIL, “the malicious LNK file hosted on the URL impersonates LogicalDOC, a cloud-based document management system commonly used in Manufacturing and Engineering firms.” Upon execution, the LNK file launches ssh.exe to run a PowerShell command, setting the stage for further payload deployment.
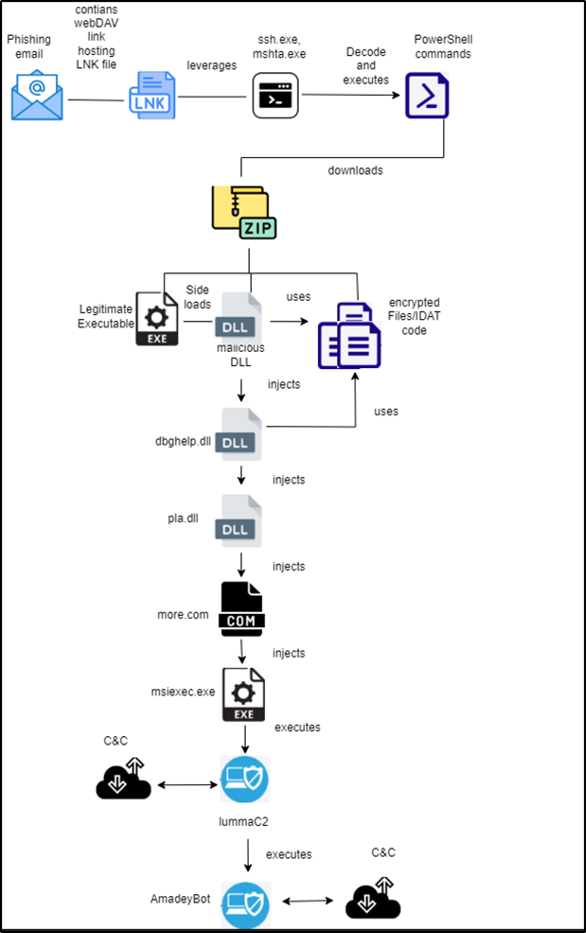
Threat actors employed several legitimate system tools, also known as Living-off-the-Land Binaries (LOLBins), to bypass traditional security mechanisms. These tools included:
- ssh.exe: Triggered to run obfuscated PowerShell commands.
- mshta.exe: Used to fetch additional payloads from remote servers.
- PowerShell: Utilized for downloading, decoding, and executing malicious scripts.
A critical aspect of the attack chain involves the abuse of Google Accelerated Mobile Pages (AMP) and shortened URLs to host malicious PowerShell scripts. The PowerShell command manipulates security protocols and performs actions such as fetching a payload from a Pastebin URL and executing it in memory.
The attackers deployed Lumma Stealer and Amadey Bot through an intricate process involving DLL sideloading and file injection techniques:
- DLL Sideloading: Legitimate executables, such as
syncagentsrv.exe, were manipulated to load malicious DLLs. - Code Injection: Malicious code was injected into processes like
msiexec.exeandexplorer.exeto ensure stealth and persistence. - Persistence Mechanism: The malware created a Task Scheduler entry named “NodeJS Web Framework” to maintain control over infected systems.
Lumma Stealer and Amadey Bot were used to gather sensitive information and establish long-term persistence. Lumma Stealer targeted sensitive data from compromised machines, while Amadey Bot ensured continuous monitoring and control. As CRIL highlights, “the malicious code in ‘more.com’ is responsible for deploying the final payload by injecting it into a newly created process.”
The attackers showcased advanced techniques, including fileless execution and encrypted payload delivery, to evade detection. Their reliance on legitimate tools further complicates detection. CRIL observed, “The final payload, which involves the deployment of both Lumma Stealer and Amadey Bot, highlights the TA’s intent to steal sensitive information and maintain persistent control over compromised systems.”
For the detection rules, visit CRIL’s GitHub repository.
Related Posts:
- New Alert: Amadey Trojan Spearheads APT-C-36’s Malicious Campaign
- Divulge, Dedsec, and Duck: The Rise of Advanced Stealer Malware
- LUMMA Malware: Cybercriminals Elevate Tactics with Fake Invoice Campaign
- MaaS in Action: How Lumma Stealer Employs Advanced Delivery Techniques
- Cybercriminals Turn Discord into Malware Playground with Lumma Stealer