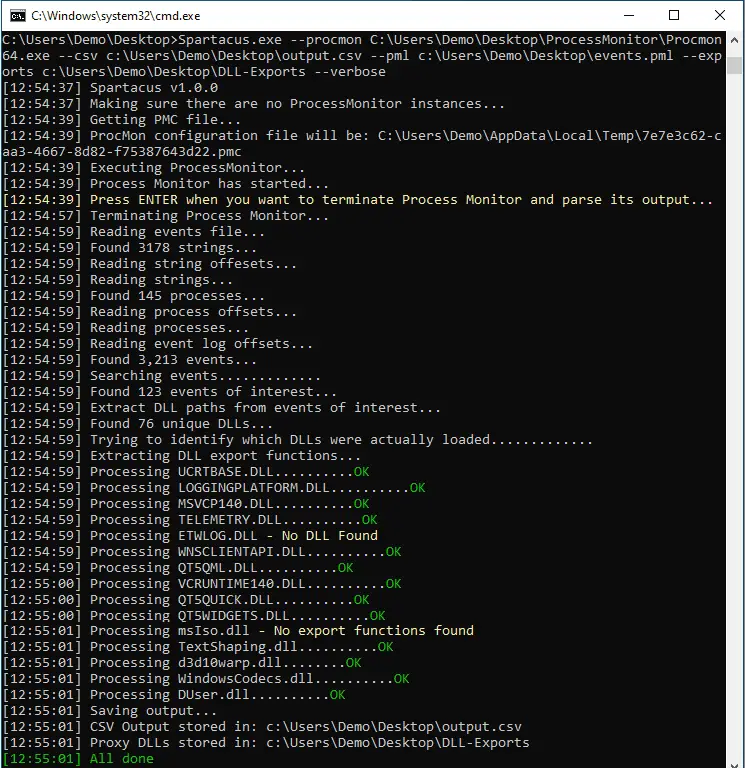
Spartacus DLL Hijacking
Spartacus is utilising the SysInternals Process Monitor and is parsing raw PML log files. You can leave ProcMon running for hours and discover 2nd and 3rd level (ie an app that loads another DLL that loads yet another DLL when you use a specific feature of the parent app) DLL Hijacking vulnerabilities. It will also automatically generate proxy DLLs with all relevant exports for vulnerable DLLs.

Features
- Parsing ProcMon PML files natively. The config (PMC) and log (PML) parsers have been implemented by porting partial functionality to C# from https://github.com/eronnen/procmon-parser/. You can find the format specification here.
- Spartacus will create proxy DLLs for all missing DLLs that were identified. For instance, if an application is vulnerable to DLL Hijacking via version.dll, Spartacus will create a version.dll.cpp file for you with all the exports included in it. Then you can insert your payload/execution technique and compile.
- Able to process large PML files and store all DLLs of interest in an output CSV file. Local benchmark processed a 3GB file with 8 million events in 45 seconds.
- [Defence] Monitoring mode trying to identify running applications proxying calls, as in “DLL Hijacking in progress”. This is just to get any low-hanging fruit and should not be relied upon.
Use
Execution Flow
- Generate a ProcMon (PMC) config file on the fly, based on the arguments passed. The filters that will be set are:
- Operation is CreateFile.
- Path ends with .dll.
- Process name is not procmon.exe or procmon64.exe.
- Enable Drop Filtered Events to ensure minimum PML output size.
- Disable Auto Scroll.
- Execute Process Monitor.
- Halt its execution until the user presses ENTER.
- Terminates Process Monitor.
- Parses the output Event Log (PML) file.
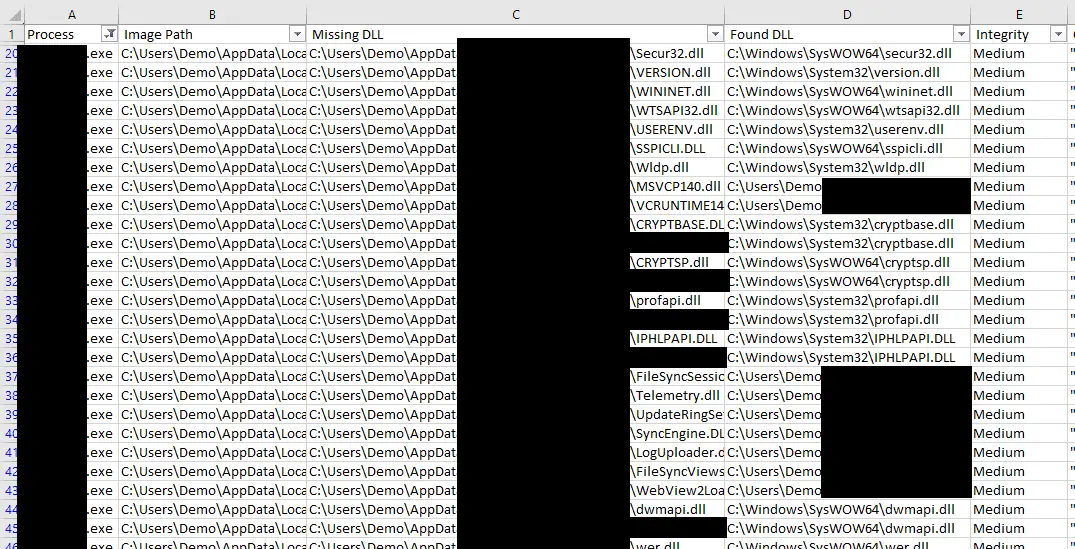
- Creates a CSV file with all the NAME_NOT_FOUND and PATH_NOT_FOUND DLLs.
- Compares the DLLs from above and tries to identify the DLLs that were actually loaded.
- For every “found” DLL it generates a proxy DLL with all its export functions.
Changelog v2.2
[New]IncludedExamples.mdin the distribution archive.[New]As command line arguments were becoming too much, createdCommandLineGenerator.html.[New]Implement thesignmode, to enable creating self-signed certificates and using any given certificate to sign an executable/DLL. The code was taken & customised from https://github.com/Danielku15/SigningServer, under MIT License – original author is Danielku15.[Fix]Fixed PostBuildEvent in proxy.vcxproj, PR by https://github.com/Signum21.[Fix]Fixed placeholder creation when DLL does not exist, PR by https://github.com/kost.
Download & Tutorial
Copyright (c) 2022 Accenture Security