SprayingToolkit: make password spraying attacks against Lync/S4B & OWA
SprayingToolkit
A set of Python scripts/utilities that tries to make password spraying attacks against Lync/S4B & OWA a lot quicker, less painful and more efficient.
Download
git clone https://github.com/byt3bl33d3r/SprayingToolkit.git
Use
Atomizer
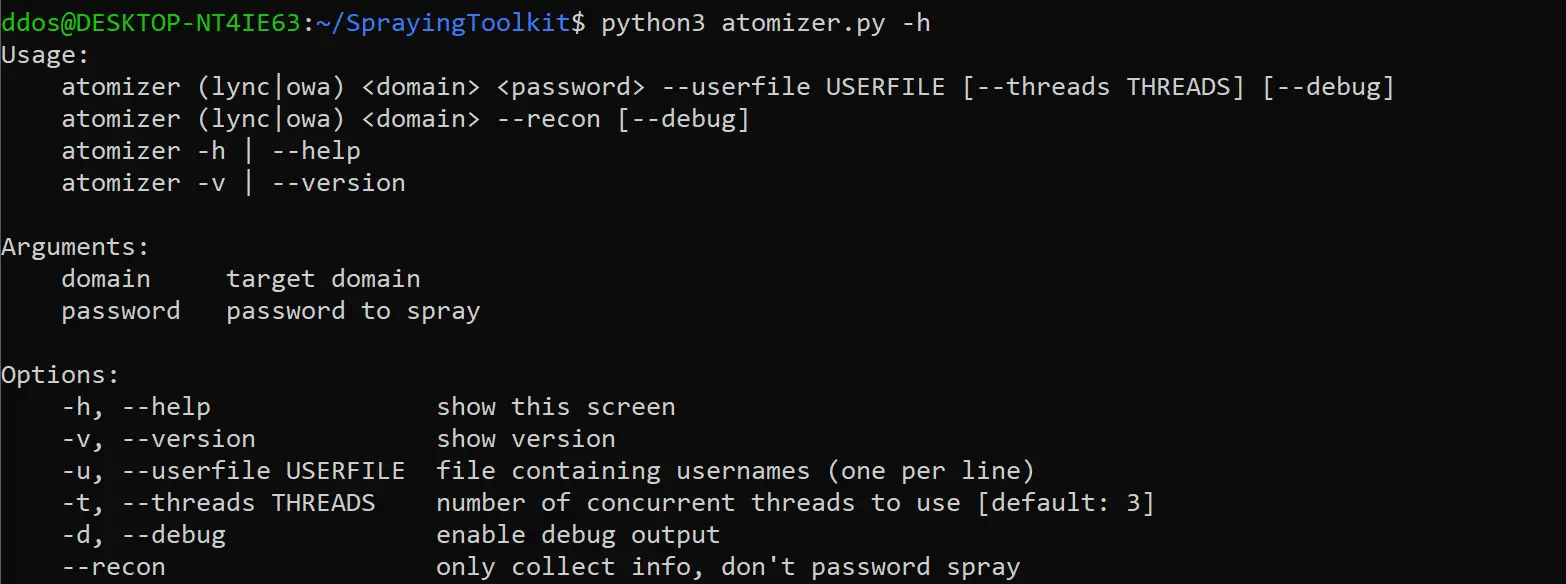
A blazing fast password sprayer for Lync/Skype For Business and OWA, built on Asyncio and Python 3.7
Usage
Vaporizer
A port of @OrOneEqualsOne‘s GatherContacts Burp extension to mitmproxy with some improvements.
Scrapes Google and Bing for LinkedIn profiles, automatically generate emails from the profile names using the specified pattern and performs password sprays in real-time.
(Built on top of Atomizer)
Usage
mitmdump -s vaporizer.py –set sprayer=(lync|owa) –set domain=domain.com –set password=password –set email_format='{f}.{last}’
By default email_format is set to {first}.{last} pattern and is not a required argument.
Install the mitmproxy cert, set the proxy in your browser, go to google and/or bing and search (make sure to include the /in):
site:linkedin.com/in “Target Company Name”
Emails will be dumped to emails.txt in the specified format and passed to Atomizer for spraying.
Aerosol
Scrapes all text from the target website and sends it to AWS Comprehend for analysis to generate custom wordlists for password spraying.
Still a work in progress
Usage
mitmdump -s aerosol.py --set domain=domain.com
Copyright (C) 2018 byt3bl33d3r
Source: https://github.com/byt3bl33d3r/





