A new report by Wiz Threat Research highlights critical misconfigurations in Spring Boot Actuator, exposing sensitive data and creating avenues for remote code execution (RCE) in cloud environments. With over 60% of cloud deployments leveraging Spring Boot Actuator, organizations are at risk unless proper security measures are implemented.
Spring Boot Actuator is widely adopted to monitor Java applications, offering real-time insights into system health and performance. However, when misconfigured, this powerful tool can expose sensitive information or even allow attackers to execute malicious code. Wiz explains: “Misconfigurations can lead to exposure of sensitive data and credentials (e.g., API keys, tokens, and passwords) and even enable remote code execution (RCE) in certain versions of Spring Boot.”
Alarmingly, Wiz found that 11% of cloud environments running Spring Boot Actuator have instances publicly exposed to the internet, and 1 in 4 of these environments contain misconfigurations. These issues often stem from human error, insecure default settings, or testing oversights that persist into production systems.
Common Misconfigurations and Their Impacts
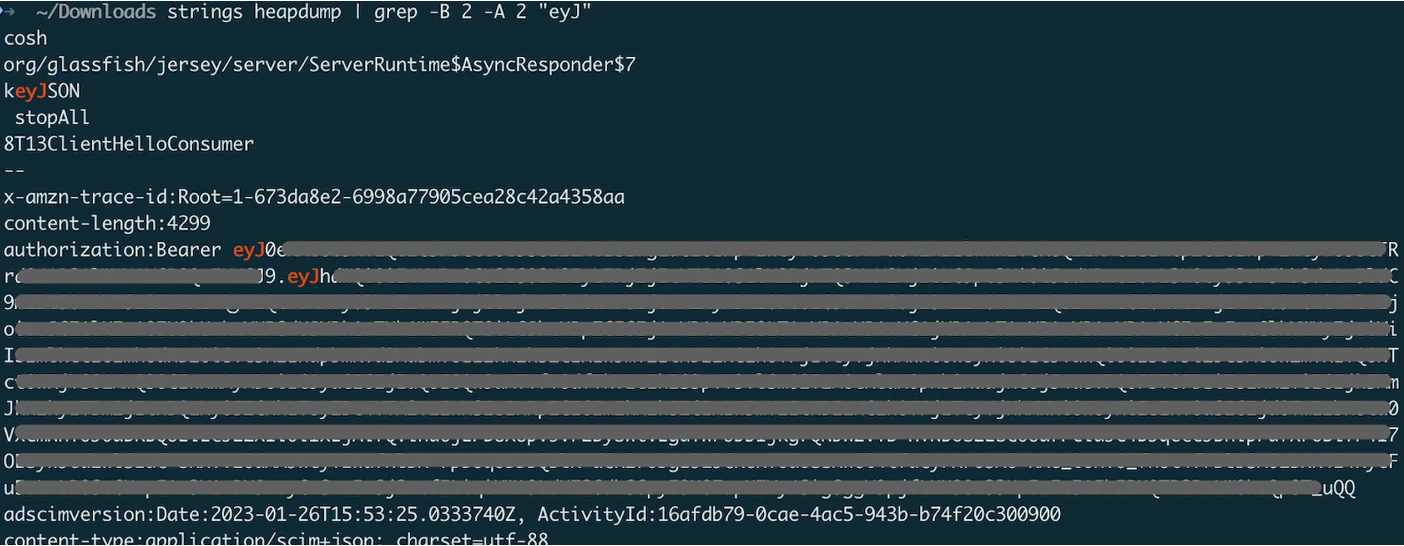
1. Exposed HeapDump Files
The /heapdump endpoint, designed for diagnosing memory issues, can inadvertently expose critical secrets stored in the application memory, such as AWS access keys, JWT tokens, and user session data. Wiz highlights: “If credentials such as passwords, tokens, cloud keys, or other secrets are loaded into the memory of a Java application’s JVM during its runtime, these might be included in the heap dump.”
Attackers can exploit exposed endpoints using simple tools:
2. Exposed Gateway Endpoints Enabling RCE (CVE-2022-22947)
Spring Cloud Gateway versions 3.0.0 to 3.0.6 and 3.1.0 are vulnerable to remote code execution (RCE) if misconfigured to allow unauthenticated public access. Exploiting this involves creating malicious routes that execute commands on the server, such as querying AWS metadata services for credentials.
Wiz found that 28% of cloud environments using Spring Cloud Gateway include at least one vulnerable instance. Proper configuration is critical, as insecure endpoints allow attackers to gain unauthorized access to sensitive services.
3. Exposed Env Endpoint
The /env endpoint exposes runtime environment variables, including database credentials, API keys, and configuration properties. Wiz explains: “When accessing the env endpoint, it returns a structured JSON response… potentially exposing sensitive information to unauthorized users.”
Similar to heap dumps, attackers can scan and parse these endpoints to extract valuable credentials.
Misconfigurations, unlike CVEs, are harder to address because they stem from improper configurations rather than code flaws. Wiz emphasizes their significance: “While immediate remote code execution (RCE) might not always be feasible, these details support reconnaissance efforts, expanding attackers’ capabilities and potential access to sensitive resources.”
Even without RCE, exposed credentials can enable initial access, lateral movement, and privilege escalation within cloud environments.
Although no publicly documented threat campaigns have yet exploited Spring Boot Actuator misconfigurations, Wiz warns that such blind spots could already be used in undetected breaches. Organizations must act proactively to mitigate these risks. Wiz recommends:
- Enforce Authentication: Protect sensitive endpoints like
/heapdump,/gateway/routes, and/envwith proper authentication. - Minimize Exposure: Limit public access to Actuator endpoints and restrict access to trusted IP addresses.
- Update and Secure Defaults: Always use the latest versions of Spring Boot Actuator and enforce secure configurations.
Wiz concludes with a clear message: “By expanding the scope of software security scanning beyond just CVEs, we can gain a more comprehensive view of attack surface areas and better safeguard sensitive systems.”
Related Posts:
- New Phishing Campaign Targets AWS Accounts: Security Experts Warn
- No Deal: Wiz Rejects Google, Sets Sights on IPO
- Alphabet to Acquire Cybersecurity Powerhouse Wiz for $23 Billion
