
Telegram app Phishing page
Cybersecurity researchers at K7 Security Labs have pulled back the curtain on a sophisticated and insidious Android Remote Administration Tool (RAT) they’ve dubbed “SpyMax.” This malicious software, specifically designed to target unsuspecting Telegram users, has the potential to compromise user privacy and security on a massive scale.
SpyMax’s attack strategy begins with a seemingly harmless phishing image that cleverly mimics the official Telegram app. Unsuspecting victims, lured by this familiar facade, are tricked into downloading a malicious APK file named “ready.apk,” masquerading as a legitimate Telegram app update. This marks the first step in a meticulously orchestrated attack designed to gain complete control over the victim’s device.
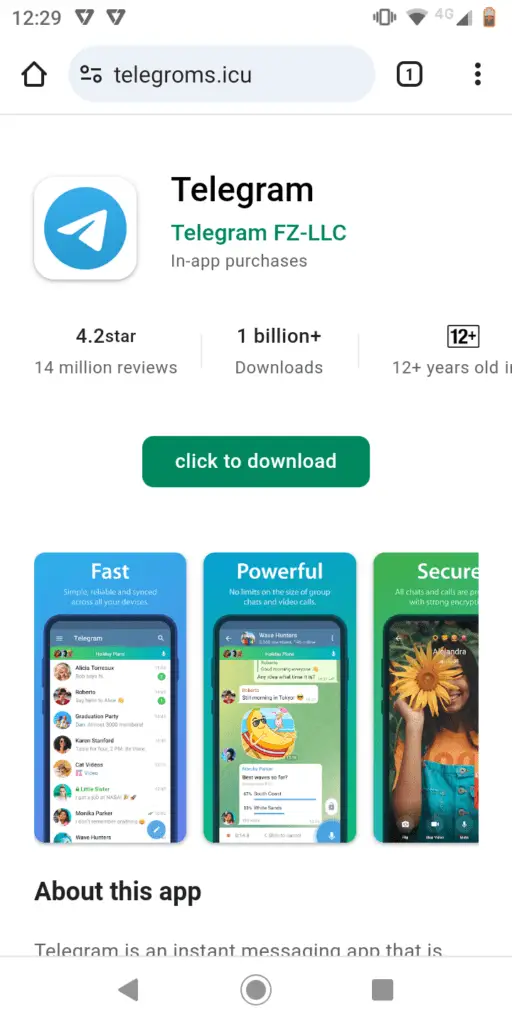
Once installed, SpyMax doesn’t immediately reveal its true nature. Instead, it patiently bides its time, subtly requesting access to the device’s Accessibility Service. This seemingly innocuous request, if granted, opens the floodgates for SpyMax to unleash its full arsenal of malicious capabilities.
With Accessibility Service permissions in hand, SpyMax sheds its disguise and transforms into a full-fledged trojan horse. It silently activates a keylogger, meticulously recording every keystroke made by the unsuspecting user, potentially capturing sensitive information like passwords, credit card numbers, and private conversations.
SpyMax’s reach extends far beyond mere keystrokes. It systematically harvests a wealth of personal data, including precise location information (altitude, latitude, longitude, and even the speed at which the device is moving), device details, and more. This stolen information is then carefully compressed and transmitted to a remote command-and-control (C2) server, where it falls into the hands of malicious actors who can exploit it for nefarious purposes.
What makes SpyMax particularly menacing is its ability to communicate with the C2 server. This connection allows attackers to remotely control the compromised device, potentially executing commands, installing additional malware, or exfiltrating even more sensitive data. The C2 server essentially transforms the victim’s device into a puppet, subject to the whims of the threat actors.
To protect yourself from falling victim to such threats, it’s imperative to remain vigilant. Always download apps from official sources, exercise caution when clicking on links or attachments, and keep your device’s software up to date.