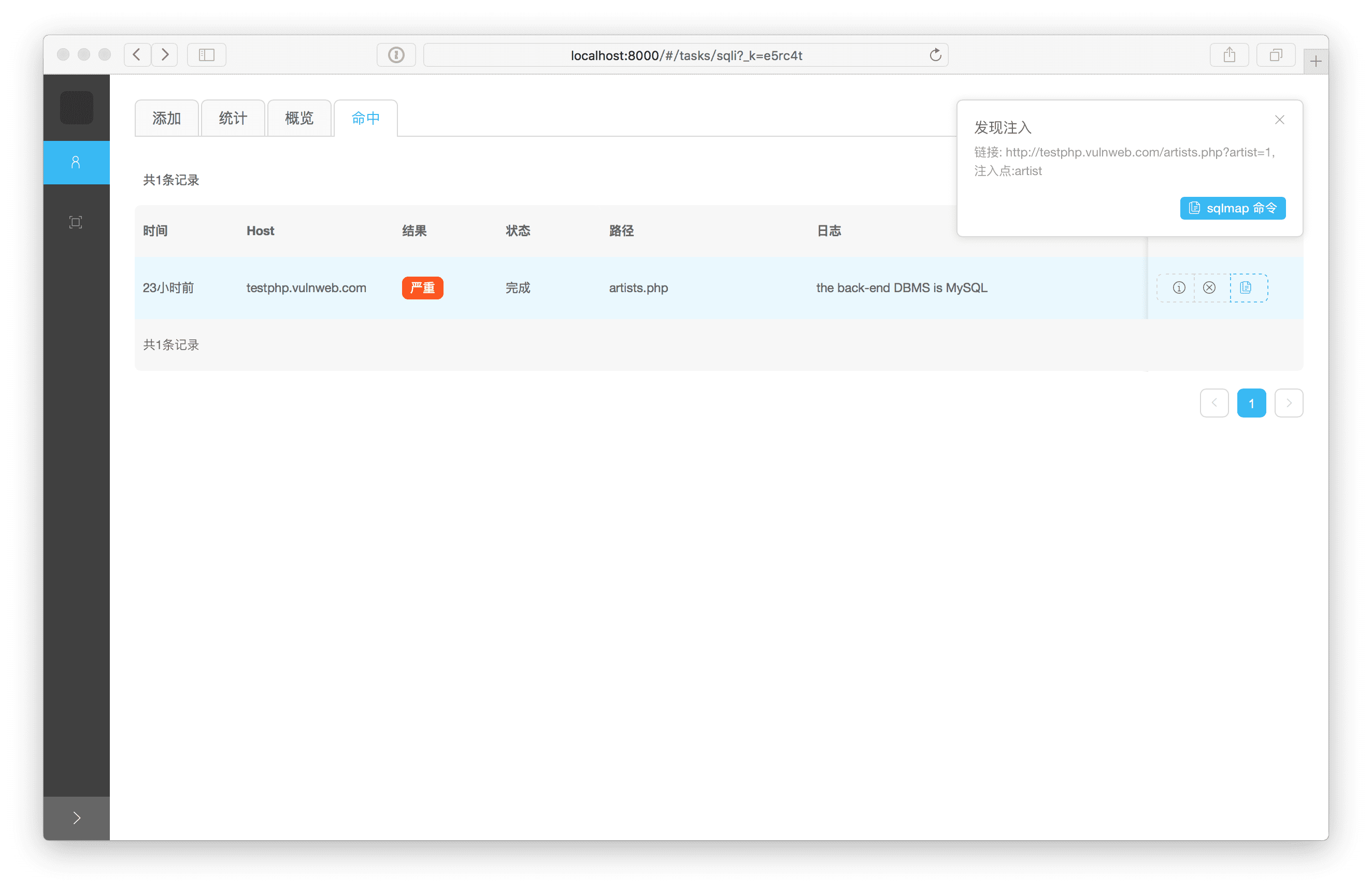
SQLiScanner: Automatic SQL injection with Charles and sqlmap api

SQLiScanner
Automatic SQL injection with Charles and sqlmapapi
Installation
Preferably, you can download SQLiScanner by cloning the Git repository:
git clone https://github.com/0xbug/SQLiScanner.git --depth 1
You can download sqlmap by cloning the Git repository:
git clone https://github.com/sqlmapproject/sqlmap.git –depth 1
SQLiScanner works with Python version 3.x on Linux and OSX.
Create virtualenv and install requirements
cd SQLiScanner/ virtualenv --python=/usr/local/bin/python3.5 venv source venv/bin/activate pip install -r requirements.txt
Setting
DATABASES Setting
SQLiScanner/settings.py:85
SendEmail Setting
SQLiScanner/settings.py:158
scanner/tasks.py:14
Syncdb
python manage.py makemigrations scanner
python manage.py migrate
Create superuser
python manage.py createsuperuser
Run
redis-server
python sqlmapapi.py -s -p 8775
python manage.py celery worker –loglevel=info
python manage.py runserver
Copyright (C) 2017 0xbug
Source: https://github.com/0xbug/