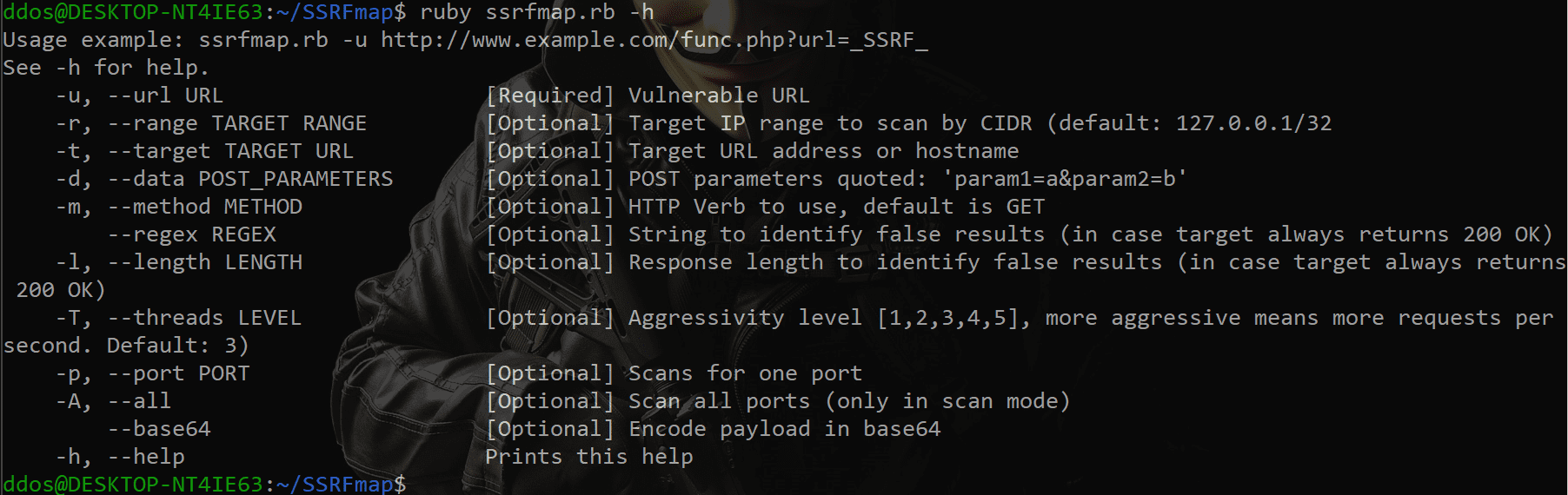
SSRFmap
A simple service scanner for Server Side Request Forgery vulnerabilities.
Installation
git clone https://github.com/dreadlocked/SSRFmap.git
cd SSRFmap
bundle install
Use

Usage examples
Request a single resource via GET request
ruby ssrfmap.rb –url http://www.example.com/controller?url=_SSRF_ –target http://169.254.169.254/
Request a single resource via POST request
ruby ssrfmap.rb –url http://www.example.com/controller –data “url=_SSRF_” –target http://169.254.169.254/
Default range scan on 127.0.0.1/32 via GET requests
ruby ssrfmap.rb --url http://www.example.com/controller?url=_SSRF_
Range scan on 192.168.0.0/24 via GET requests
ruby ssrfmap.rb --url http://www.example.com/controller?url=_SSRF_ --range 192.168.0.0/24
Specify a regex for those websites who always return 200 OK
ruby ssrfmap.rb –url http://www.example.com –data “{\”url\”:\”_SSRF_\”}” –regex “Example Domain”