Leveraging restricted management AUs to create sticky backdoor accounts | Image: Datadog Security Labs
In recent research, Datadog Security Labs has shed light on a potential security risk within Microsoft Entra ID (formerly Azure Active Directory), Microsoft’s cloud-based identity and access management solution. The report details how Entra ID’s administrative units (AUs), a feature designed to streamline permissions management, can be exploited by malicious actors to establish persistent backdoor access within a compromised tenant.
AUs in Microsoft Entra ID allow administrators to restrict permissions in a role to a defined scope within the organization. This can help in limiting potential damage by assigning roles more granularly—similar to how Organizational Units (OUs) are used in Active Directory. However, the research emphasizes that this useful feature can also be misused by attackers, making it difficult for organizations to detect and remove unauthorized users.
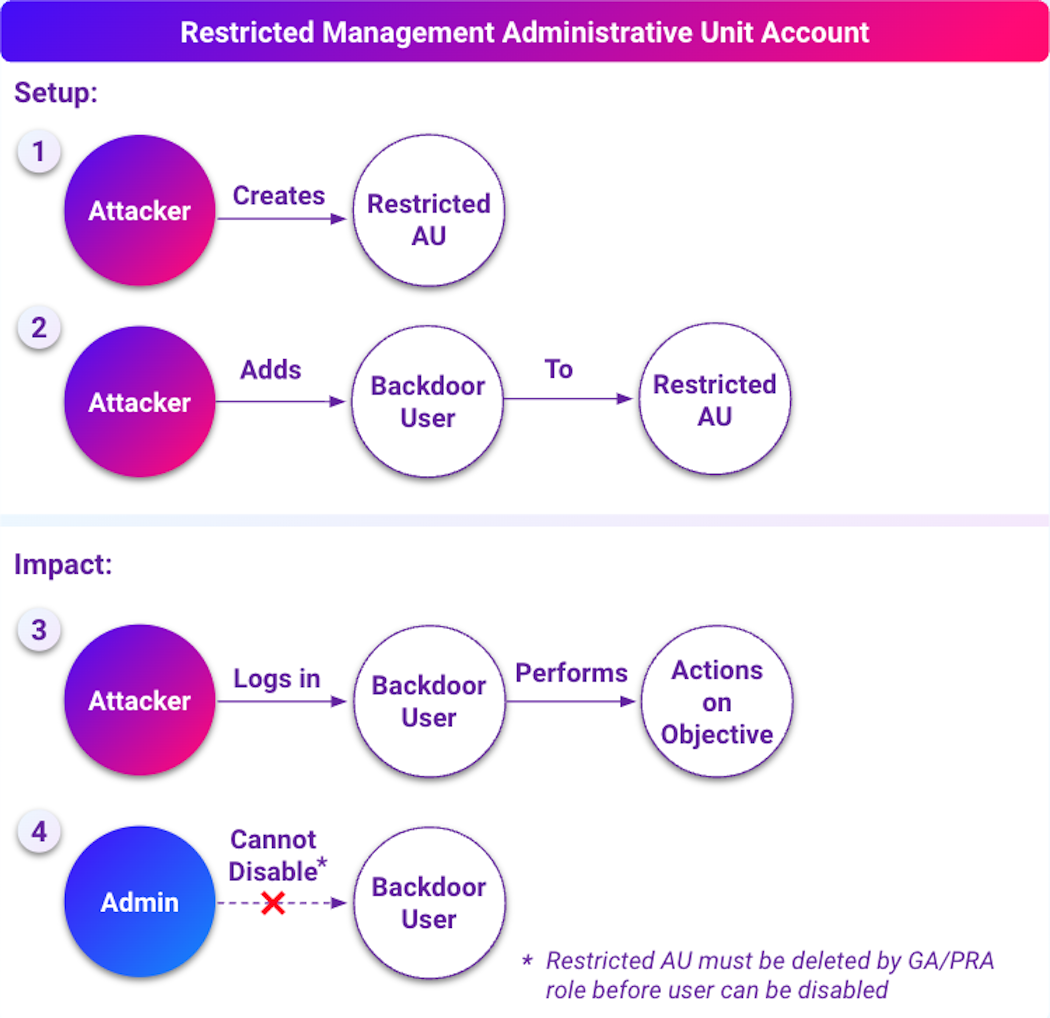
Restricted management AUs can be configured to prevent any modifications to user accounts within the AU, except by designated administrators. An attacker could leverage this feature to create a “sticky” backdoor account that remains active even after their initial access is revoked.
Hidden membership AUs conceal the list of users within the AU from most administrators, making it challenging to identify which accounts are affected by a particular role assignment. This feature could be used to grant an attacker’s backdoor account powerful permissions without raising suspicion.
Datadog presents two main scenarios where these features could be abused:
- Scenario 1: Sticky Backdoor Account: An attacker could create a backdoor account within a restricted management AU. Even tenant-wide administrators would be unable to modify or remove this account directly without first removing it from the AU. This provides attackers with long-lasting persistence in a compromised environment.
- Scenario 2: Covert Role Assignment: By using a hidden membership AU, attackers could assign privileged roles (like Privileged Authentication Administrator) to their backdoor accounts, allowing them to modify passwords, reset MFA methods, and take over key accounts without being detected by most security analysts.
By combining these techniques, an attacker could establish a backdoor account that is not only invisible to most administrators but also grants them the ability to make changes that go unnoticed by security teams. This attack persistence could be devastating if not detected and remediated promptly.
While Microsoft Entra ID’s AUs offer useful capabilities for managing large cloud environments, they can also be misused to facilitate persistent and stealthy attacks. Organizations should be aware of these risks and implement safeguards to detect and respond to any misuse of these features swiftly.
For more details on the research and how to safeguard your environment, visit Datadog Security Labs.
Related Posts:
- Phishing for Profits: Attackers Mine Crypto & Spam Through OAuth Apps
- Sticky Werewolf Targets Aviation Sector in Latest Malicious Campaign