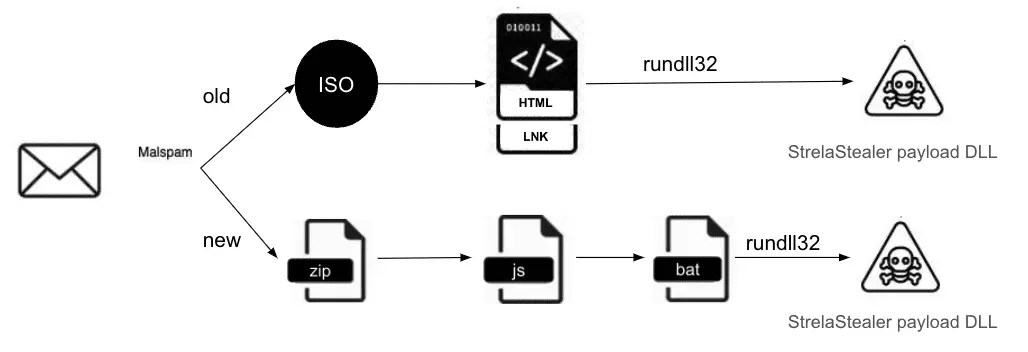
Infection chain | Image: Unit 42
Researchers at Unit 42 have uncovered a major new attack campaign deploying an updated version of the StrelaStealer malware. Targeting organizations across the European Union and the United States, this wave arrives after multiple large-scale attacks throughout 2023. This latest variant shows the attackers are actively refining their methods to evade detection.
What is StrelaStealer?
First unearthed by cybersecurity researchers at DCSO_CyTec in November 2022, StrelaStealer is a type of malware classified as an “infostealer,” designed to infiltrate systems and pilfer sensitive user information. In this case, it specializes in hijacking email credentials. Initial infection typically occurs when a victim opens a malicious attachment disguised as an invoice, order confirmation, or another common business document.
Once inside your system, StrelaStealer lays the groundwork for serious consequences. Attackers can use your stolen email credentials to:
- Spy on Your Communications: Illicitly reading sensitive emails could expose trade secrets, financial data, or private customer information.
- Impersonate You or Your Company: Fraudulent emails sent from your address could trick colleagues, clients, or suppliers into clicking malicious links, sharing confidential files, or even wiring money to attackers.
- Gain Deeper Access: A compromised email account is a powerful springboard, allowing cybercriminals to escalate attacks within your company’s network.
What’s New in the 2024 Campaign

The latest campaigns have seen StrelaStealer delivered through a chameleon-like series of spam emails, with attachments that morph in format to dodge detection by previously generated signatures. The malware authors have fine-tuned the DLL payload, arming it with advanced obfuscation and anti-analysis mechanisms.
At the heart of the StrelaStealer campaigns lies a meticulously crafted spear-phishing operation. Attackers entice victims with emails containing ZIP file attachments that, once opened, unleash a JScript file onto the system. This script is the harbinger of doom, paving the way for the drop of a Base64-encrypted file and a batch file, culminating in the execution of a Portable Executable (PE) DLL file. This DLL, masquerading under the guise of benign software, calls forth the “hello” function via rundll32.exe, executing the payload that seeks out and transmits email login data back to the attackers’ command and control (C2) server.
The malware employs a control flow obfuscation technique that not only complicates analysis but also poses a risk of timeout during sandbox execution. This updated packer is a testament to the malware developers’ relentless pursuit of evasion, showcasing their ability to stay several steps ahead of cybersecurity defenses.
The focus is still on companies in the EU and the US, but analysis suggests attackers may be prioritizing high-tech organizations with potentially valuable intellectual property or research data.
The Ongoing Battle
The StrelaStealer campaign underscores the constant cat-and-mouse game of cybersecurity. Attackers relentlessly refine their tools and tactics to stay ahead of defenses. Businesses and individuals alike need to maintain vigilance, promote smart online practices, and invest in robust security solutions to safeguard their valuable data.