
In a recent study, researchers from Korea University have unveiled “SysBumps,” the first successful Kernel Address Space Layout Randomization (KASLR) break attack targeting macOS systems running on Apple Silicon processors. The findings, presented at CCS ’24, highlight vulnerabilities in speculative execution that expose critical kernel memory addresses, posing significant risks to macOS users.
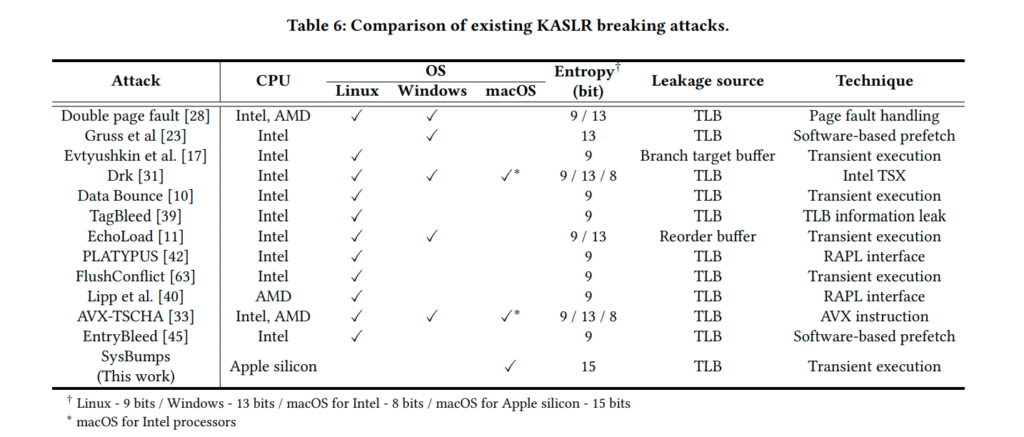
KASLR is a vital kernel hardening technique that randomizes memory addresses to mitigate memory corruption vulnerabilities. Apple has bolstered its implementation on macOS for Apple Silicon with kernel isolation, separating kernel and user address spaces. However, the researchers identified a critical flaw: speculative execution during system calls. This flaw enables attackers to bypass kernel isolation and infer the validity of kernel addresses.
“ By using Spectre-type gadgets in system calls, an unprivileged attacker can cause translations of the attacker’s chosen kernel addresses, causing the TLB to change according to the validity of the address,” the researchers noted, emphasizing the role of Translation Lookaside Buffers (TLBs) as a side-channel source for the attack.
The SysBumps attack exploits speculative execution vulnerabilities in macOS system calls. Key steps include:
- Triggering Speculative Execution: Attackers manipulate system calls to bypass kernel address validation checks during speculative execution.
- TLB Probing: Using reverse-engineered TLB properties, attackers detect whether a kernel address is valid by observing changes in TLB state.
- Revealing Kernel Layout: This process allows attackers to infer kernel base addresses, effectively breaking KASLR.
The researchers reverse-engineered Apple’s M-series TLB architecture, uncovering critical details like its shared design between user and kernel processes. They achieved this using Apple’s performance monitoring units (PMUs).
The study demonstrated that SysBumps can break KASLR with 96.28% accuracy across various M-series processors and macOS versions. Remarkably, the attack executes within three seconds, showcasing its practicality for real-world exploitation.
Breaking KASLR undermines a core defense mechanism in macOS, exposing systems to advanced memory corruption exploits. This attack bypasses robust kernel isolation, revealing significant implications for system security.
Apple acknowledged the findings and is investigating the root cause of the vulnerability.
The full study and source code for SysBumps will be available on GitHub, offering valuable insights for addressing emerging security threats.
Related Posts:
- Researcher found new variant of spectre security flaw
- Microsoft Tackles Speculative Execution Security with New PowerShell Script
- Intel pays $100,000 in prize money for new Spectre variant discoverers
- Microsoft will pay $250,000 in bonuses to find flaws like Meltdown and Spectre