SysmonSearch: Investigate suspicious activity by visualizing Sysmon’s event log
SysmonSearch
SysmonSearch makes event log analysis more effective and less time to consume, by aggregating event logs generated by Microsoft’s Sysmon.

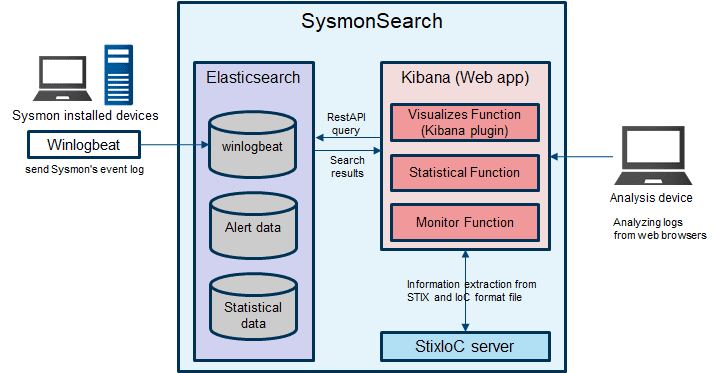
System Overview
SysmonSearch uses Elasticserach and Kibana (and Kibana plugin).
- Elasticserach
Elasticsearch collects/stores Sysmon’s event log. - Kibana
Kibana provides the user interface for your Sysmon’s event log analysis. The following functions are implemented as Kibana plugin.- Visualizes Function
This function visualizes Sysmon’s event logs to illustrate the correlation of processes and networks. - Statistical Function
This function collects the statistics of each device or Sysmon’s event ID. - Monitor Function
This function monitor incoming logs based on the preconfigured rules, and triggers alert.
- Visualizes Function
- StixIoC server
You can add search/monitor condition by uploading STIX/IOC file. From StixIoC server Web UI, you can upload STIXv1, STIXv2 and OpenIOC format files.
Download && Tutorial
Copyright (C) 2015 JPCERT Coordination Center. All Rights Reserved.