
Cybersecurity firm Proofpoint has uncovered a new phishing campaign by the Iranian-backed threat actor TA453 (aka Charming Kitten, Mint Sandstorm, APT42). In this campaign, TA453 impersonated the Institute for the Study of War (ISW), a prominent think tank, to target a high-profile religious figure.
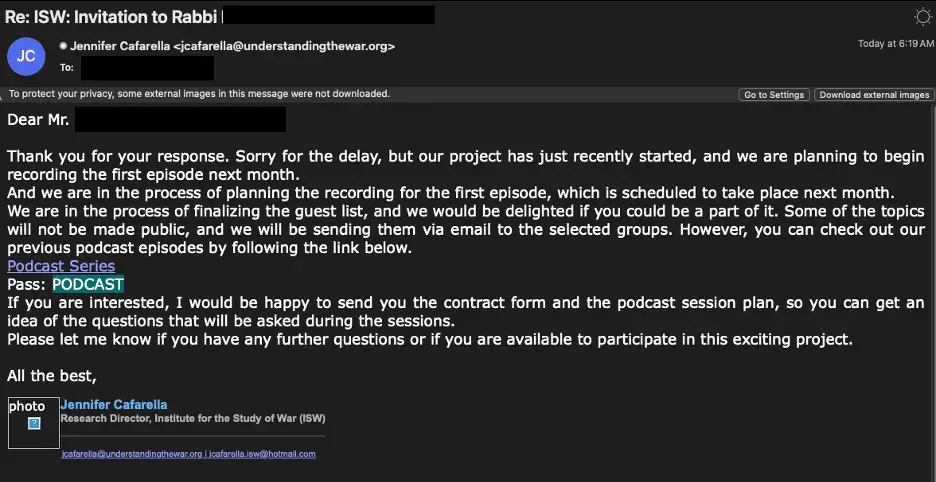
Beginning on July 22, 2024, TA453 initiated contact with multiple email addresses associated with the target, posing as the Research Director for the Institute for the Study of War (ISW). The initial email invited the target to participate as a guest on a podcast supposedly hosted by ISW. This sophisticated social engineering tactic is consistent with TA453’s known methods of building trust with their targets over time, often by spoofing legitimate organizations.
After the target responded to the initial outreach, TA453 sent a DocSend URL, leading to a password-protected text file that further linked to the actual ISW podcast. This step was likely designed to normalize the behavior of clicking links and entering passwords, making the target more susceptible to future malicious actions.
The attack escalated when TA453 sent a Google Drive URL to the target, leading to a ZIP archive titled “Podcast Plan-2024.zip.” Inside the ZIP file was an LNK (shortcut) file that, when executed, delivered the BlackSmith malware toolset. BlackSmith is a sophisticated, multi-component toolkit designed for intelligence collection, representing an evolution of TA453’s previous malware frameworks such as GorjolEcho, TAMECURL, and CharmPower.
The infection chain begins with the LNK file, which disguises itself behind a decoy PDF and extracts several files into the system’s %TEMP% directory. These files include malicious DLLs and an encrypted PowerShell script hidden within a steganographically concealed PNG image. The malware is designed to evade detection and persist on the target’s system, allowing TA453 to conduct extensive reconnaissance and data exfiltration.
At the core of the BlackSmith toolset is AnvilEcho, a modular PowerShell trojan that consolidates TA453’s various capabilities into a single, comprehensive framework. AnvilEcho is capable of bypassing SSL certificate validation, extending browser timeouts to maintain long-term command and control (C2) connections, and using advanced encryption techniques to exfiltrate collected intelligence. The trojan also includes mechanisms to bypass antivirus software and detect system defenses, further complicating detection and remediation efforts.
The attack infrastructure used by TA453 includes domains such as d75[.]site and deepspaceocean[.]info, both of which are consistent with historical TA453 operations. These domains are hosted on servers linked to previous campaigns, reinforcing the assessment that this attack is part of a broader effort to collect intelligence on behalf of the IRGC.
While Proofpoint cannot directly link TA453 to specific IRGC members, the group is widely believed to support IRGC Intelligence Organization operations. This conclusion is drawn from overlapping indicators, including unit numbering correlations, past indictments, and the targeting patterns observed in TA453 campaigns.
Related Posts:
- TikTok Hit by Zero-Day Attack: High-Profile Accounts Compromised
- Iranian APT42 Ramps Up Phishing Campaigns Against Israel, U.S. Election Targets
- Iran-Linked CyberAv3ngers Hacker Disrupt Water Operations in Western Pennsylvania