
Overview of TAG-100 operations (Source: Recorded Future)
A newly identified cyberespionage group, dubbed TAG-100 by cybersecurity firm Recorded Future, has been linked to a series of sophisticated attacks targeting high-profile government, intergovernmental, and private sector organizations worldwide. The group’s modus operandi involves exploiting vulnerabilities in internet-facing appliances to gain initial access, followed by the deployment of open-source remote access tools like Pantegana and SparkRAT.
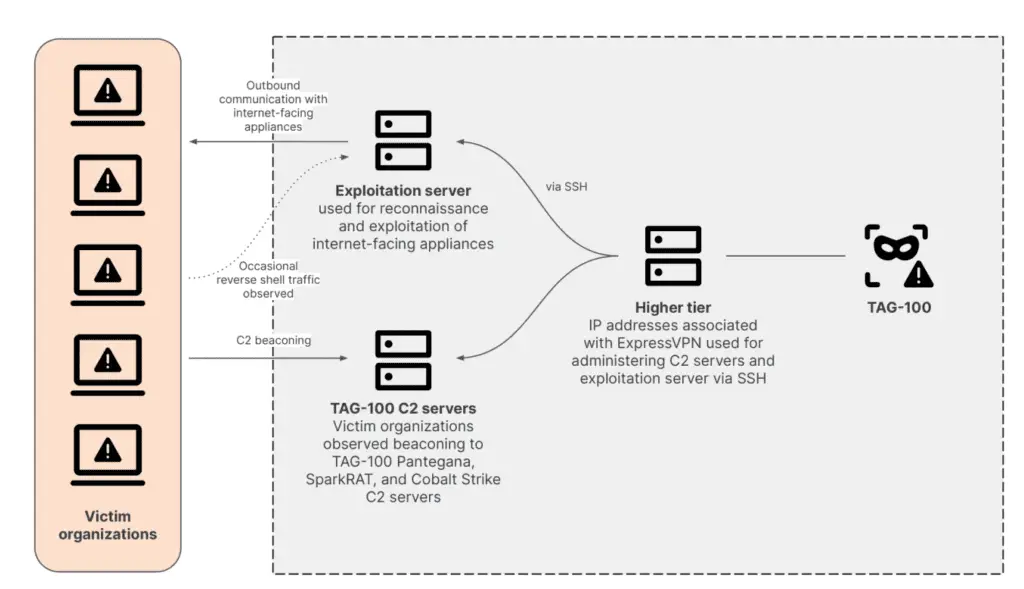
The group’s primary method of initial access involves exploiting vulnerabilities in internet-facing devices, including Citrix NetScaler ADC and Gateway, F5 BIG-IP, Zimbra Collaboration Suite, Microsoft Exchange, SonicWall, Cisco ASA, Palo Alto Networks GlobalProtect (CVE-2024-3400), and Fortinet FortiGate. These devices often have limited visibility, logging capabilities, and support for traditional security solutions, making them attractive targets for threat actors. The exploitation of these devices has been a focal point of international cybersecurity efforts, including emergency patch requests in the United States and secure-by-design legislation in the United Kingdom. Despite these measures, the widespread targeting of these devices continues to pose significant risks.
Among the victims of TAG-100’s campaign are the secretariats of two major Asia-Pacific intergovernmental organizations, along with diplomatic entities, ministries of foreign affairs, industry trade associations, and organizations in the semiconductor supply chain, non-profit sector, and religious sector. The attacks have impacted organizations in at least ten countries across Africa, Asia, North America, South America, and Oceania.
TAG-100 has employed various open-source and offensive security tools, including:
- Pantegana: An open-source malware family written in Go, featuring cross-platform payloads for Windows, Linux, and OSX. Pantegana supports file upload/download, system fingerprinting, and command-line interaction with infected hosts, using HTTPS for command-and-control (C2) communications. The group has also used obfuscation techniques to evade detection.
- SparkRAT and LESLIELOADER: TAG-100 has concurrently used another open-source Go backdoor, SparkRAT, along with the Go loader LESLIELOADER to deploy SparkRAT in various instances. These tools facilitate post-exploitation activities across multiple operating systems.
- Cobalt Strike: The group has utilized both traditional Windows Cobalt Strike Beacon payloads and the open-source, cross-platform CrossC2 to generate Beacons for Linux systems. This versatility in tool usage underscores the group’s capability to adapt to different environments and targets.
While the exact identity of TAG-100 remains unknown, the nature of their targets and tactics suggests a potential link to state-sponsored actors. Cybersecurity experts urge organizations to prioritize the security of their internet-facing appliances, implement robust vulnerability management practices, and enhance their detection and response capabilities to mitigate the risks posed by such sophisticated cyber threats.
For further analysis, please download the PDF report.