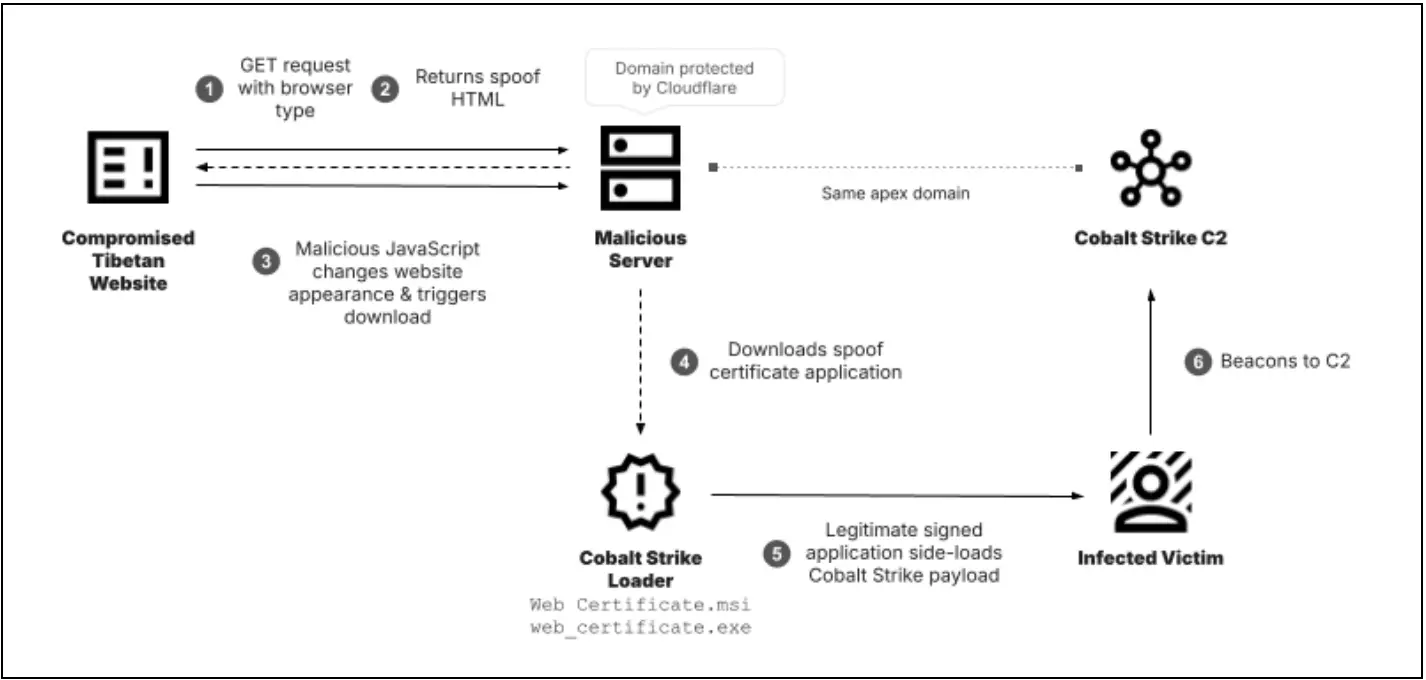
iagram of the observed infection chain Source: Recorded Future)
In a recent report by the Insikt Group, cybersecurity analysts reveal how the China-nexus threat actor TAG-112 has launched a targeted cyber-espionage campaign against the Tibetan community by compromising prominent Tibetan websites. Through a meticulously planned operation, TAG-112 deployed malicious JavaScript to distribute Cobalt Strike, a widely recognized penetration testing tool frequently repurposed by threat actors for malicious purposes.
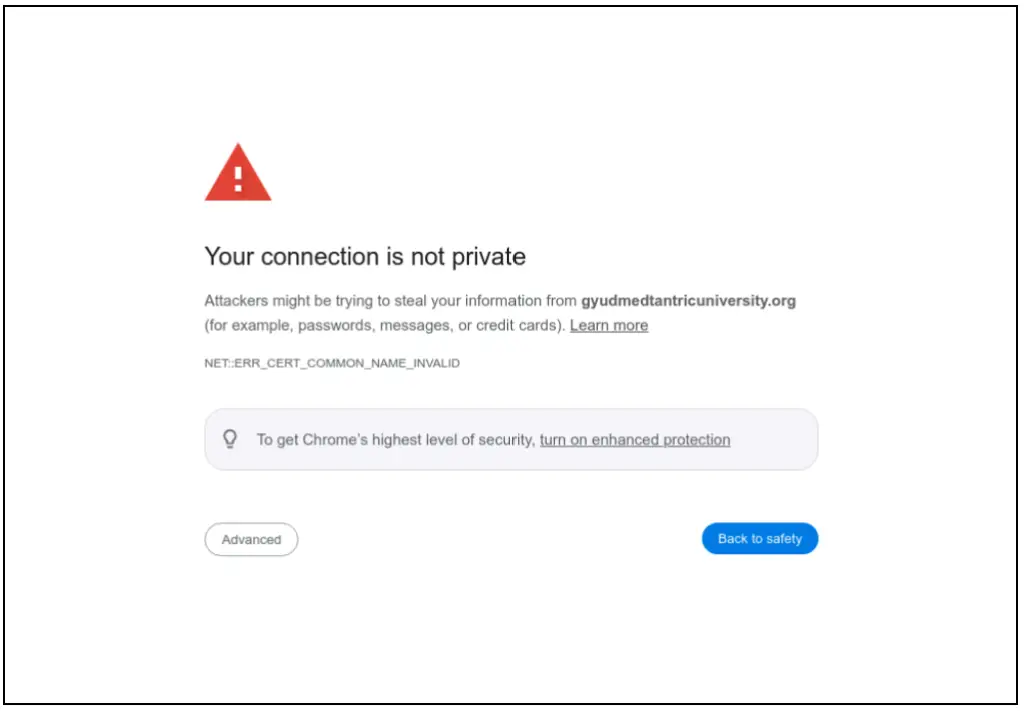
According to Insikt Group’s findings, at least two Tibetan community websites, Tibet Post and Gyudmed Tantric University, were compromised in late May 2024. The attackers modified these sites’ scripts with malicious JavaScript that mimicked a security certificate error, prompting unsuspecting visitors to download malware under the guise of a legitimate “security certificate.” The report states, “The compromised websites were manipulated to prompt visitors to the sites to download a malicious executable disguised as a ‘security certificate’ that ultimately loaded a Cobalt Strike payload upon execution.”
TAG-112 leveraged a vulnerability in the websites’ content management system, Joomla, a platform often used for community-based websites. By exploiting outdated versions of Joomla, TAG-112 uploaded the malicious code, taking advantage of these legacy systems that lacked recent security patches.
TAG-112 went to great lengths to mask the origins of this attack. Using Cloudflare as its name server provider, TAG-112 successfully obfuscated its IP address, complicating efforts to trace the malicious infrastructure back to the perpetrators. This technique, the report notes, is “increasingly observed among APT groups” and is designed to evade attribution efforts by security researchers.
Additionally, TAG-112’s infrastructure incorporated multiple domains, including maskrisks[.]com, and utilized Cloudflare Origin certificates. These domains served as control points for the malicious payloads, directing targeted users to download Cobalt Strike through secure-looking URLs. Insikt Group identified several IP addresses in South Korea linked to this infrastructure.
TAG-112’s campaign is not an isolated case but rather part of a broader strategy aligned with Chinese intelligence requirements. Insikt Group suggests that TAG-112 operates as a likely subgroup of TAG-102, also known as Evasive Panda, an advanced persistent threat (APT) group with a long history of targeting entities perceived as adversaries to the Chinese government. This includes not only Tibetan groups but also human rights organizations, academics, and other voices critical of the Chinese Communist Party (CCP).
While TAG-112’s tactics exhibit some overlap with TAG-102, including similar use of fake security prompts, Insikt Group notes distinctions between the two groups, particularly in TAG-112’s focus on deploying Cobalt Strike instead of custom malware and its lack of JavaScript obfuscation—a sign of relatively lower sophistication.
The TAG-112 attack on Tibetan websites reflects an ongoing challenge for minority communities worldwide, particularly those with digital platforms that may not have the resources to maintain robust cybersecurity defenses. As the Insikt Group report concludes, “It is highly likely that TAG112 and TAG102 Evasive Panda), among a myriad of other Chinese APT groups, will continue their targeting of ethnic, religious, and human rights-linked organizations that operate in or have a nexus to China.”
Related Posts:
- Threat Actors Exploit GitHub to Spread Malware, Targeting Multiple Operating Systems
- Predator Spyware Roars Back: New Infrastructure, Evasive Tactics
- Mirai variant botnet targets the financial sector
- Cyber-Espionage Campaign Unveiled: Operation Cobalt Whisper Hits Sensitive Industries
- From Espionage to Ransomware: Iran’s Strategic Assault on the West Revealed