Before leaving office, U.S. President Joe Biden signed a new law regulating artificial intelligence (AI) chips, imposing...
artificial intelligence
Researchers in Uruguay have recently discovered a method to use artificial intelligence (AI) to eavesdrop on victims’...
A critical vulnerability (CVE-2024-5480) has been discovered in PyTorch’s distributed RPC (Remote Procedure Call) framework, exposing machine...
In the shadowy realms of cyberspace, threats evolve as swiftly as the technologies they exploit. Resecurity’s insightful...
In a groundbreaking collaboration, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the UK National Cyber...
Recently, the Commander of the U.S. Cyber Command and Director of the National Security Agency, Army Gen....
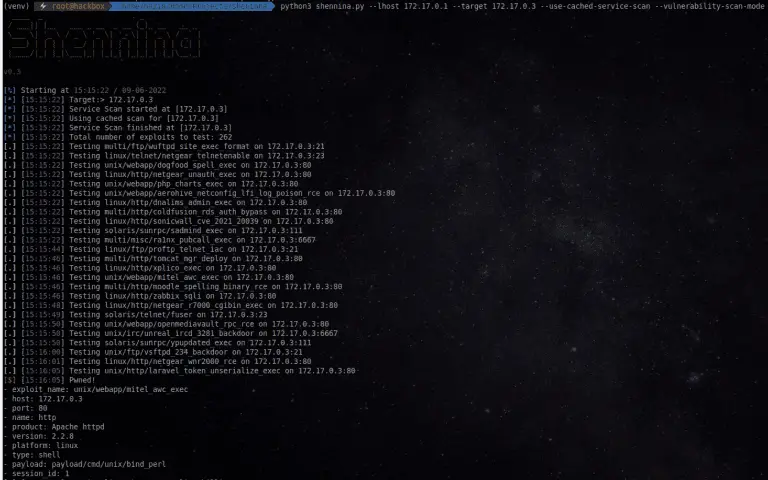
shennina Shennina is an automated host exploitation framework. The mission of the project is to fully automate...
The future is now! Still, you may not notice that, but it is a fact. After all,...
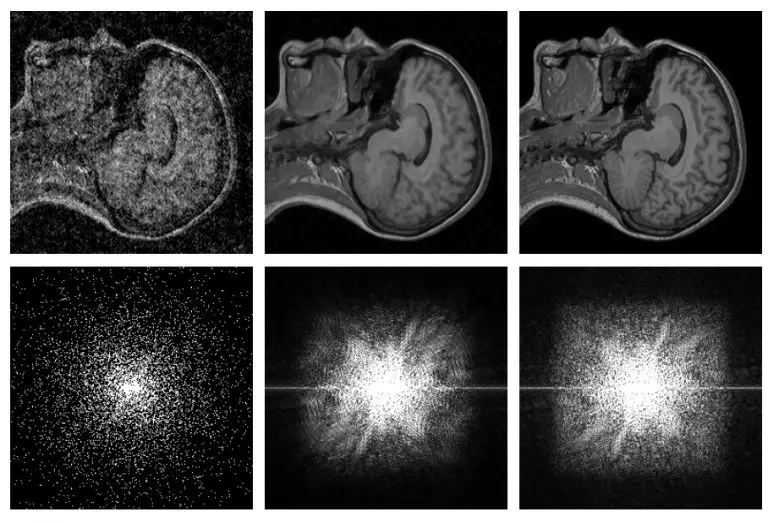
Research teams at the NVIDIA Institute and the Massachusetts Institute of Technology are using artificial intelligence to...
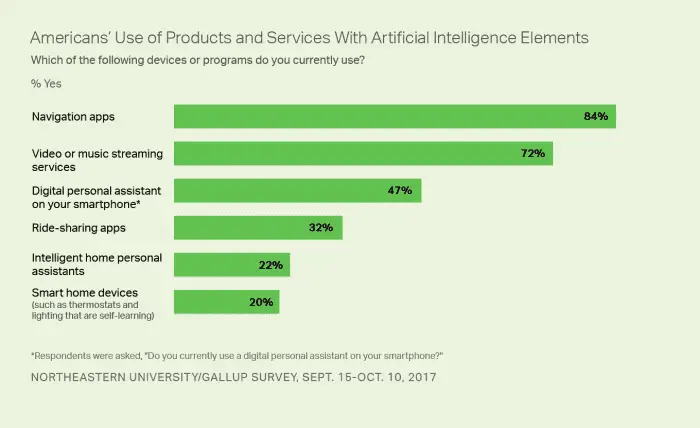
According to NYTimes reports, most Americans believe that AI technology is a problem for people’s employment. A recent...
According to newatlas, just as the United Nations continues to formulate clear international treaties related to deadly...
Machine learning is defined as “the ability to learn without being explicitly programmed,” and it can have...