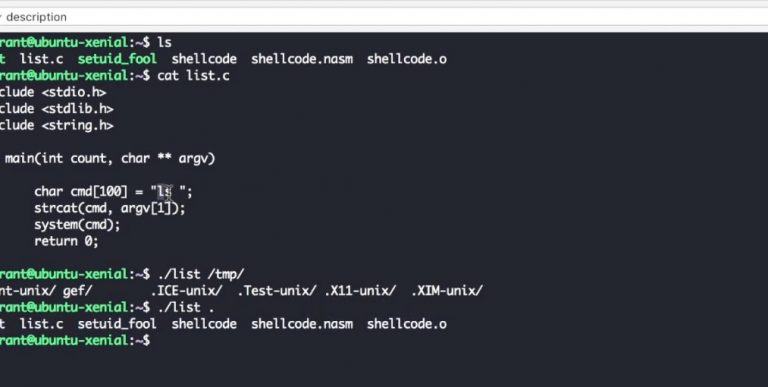
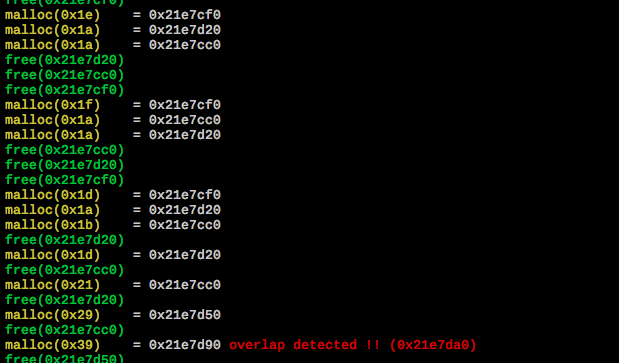
Linux Binary Exploitation Topics Lecture 1. Memory Layout of the C program. ELF binaries. Overview of the...
Linux binary Exploitation
HITCON-Training For Linux binary Exploitation Outline Basic Knowledge Introduction Reverse Engineering Static Analysis Dynamic Analysis Exploitation Useful...