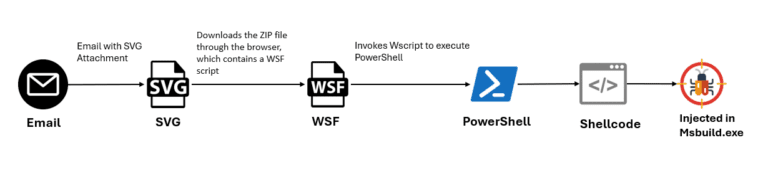
Cybersecurity researchers at eSentire’s Threat Response Unit (TRU) have uncovered a sophisticated phishing campaign distributing the AsyncRAT...
Process Hollowing
The cybersecurity world is a battlefield of constant change – understanding your enemy’s weapons and strategies is...
The burgeoning popularity of Brazil’s instant payment system, PIX, has caught the attention of cybercriminals, who have...
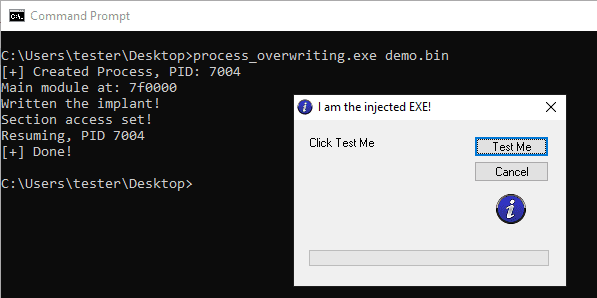
Process Overwriting Process Overwriting is a PE injection technique, closely related to Process Hollowing and Module Overloading Process Hollowing...