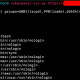
RedSails: bypassing host based security monitoring and logging
Redsails About A post-exploitation tool capable of: maintaining persistence on a compromised machine subverting many common host event logs (both network and account logon) generating false logs/network traffic Based on...