
The Securonix Threat Research team has uncovered a sophisticated phishing campaign named FLUX#CONSOLE, leveraging tax-related lures and the use of Windows MSC (Microsoft Management Console) files to deploy a stealthy backdoor.
The campaign begins with tax-themed phishing emails, often including documents such as “Income-Tax-Deduction-and-Rebates202441712.pdf.” While these PDFs are benign and serve only as distractions, the real threat unfolds when the user interacts with an accompanying malicious MSC file disguised as a PDF.
Microsoft Management Console files can execute embedded scripts or commands under the guise of legitimate administrative tools. This ability allows attackers to exploit MSC files for arbitrary code execution.
How FLUX#CONSOLE Works
- Obfuscated MSC Loader: The MSC file acts as both a loader and a dropper, either downloading or decoding an embedded payload. The payload contains a malicious DLL file (DismCore.dll), which is sideloaded via the legitimate Windows Dism.exe process.
- Hiding in Plain Sight: The MSC file is cleverly disguised with PDF-like icons, making it appear trustworthy. Default settings in Windows that hide file extensions further aid the attackers.
- Persistence and Obfuscation: To maintain persistence, the campaign uses scheduled tasks, while layers of obfuscation—ranging from Base64 encoding to complex JavaScript—complicate analysis.
- Command-and-Control Communication: The malware communicates with its command-and-control (C2) server hosted at siasat[.]top, using encoded POST requests to exfiltrate data.
Unlike the more common LNK files used in previous campaigns like SLOW#TEMPEST and SHROUDED#SLEEP, FLUX#CONSOLE opts for MSC files, exploiting their inherent trust within Windows administrative workflows. “This approach, combined with the use of highly obfuscated JavaScript to deliver a malicious sideloaded DLL stress the importance of robust endpoint monitoring solutions that are capable of adapting quickly to the rapidly changing threat landscape,” the report states.
The embedded payload delivers the DismCore.dll backdoor, enabling:
- Data exfiltration to C2 servers.
- Execution of remote commands.
- Persistent control over infected systems.
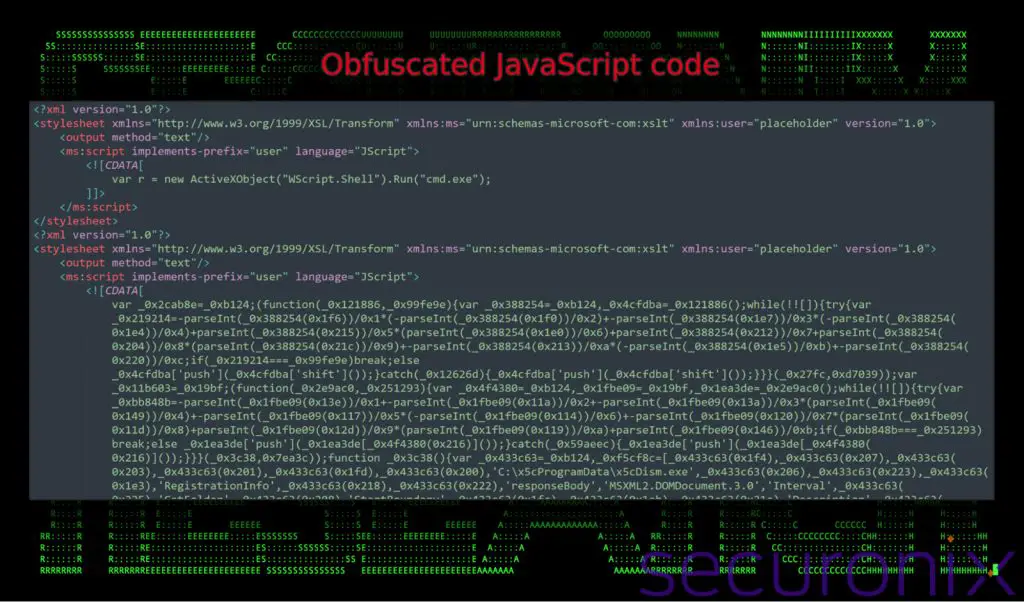
The analysis highlights that “The remote and embedded payloads in the .msc file both aim to accomplish the same goal: delivering and executing a malicious DLL. By providing redundancy in the attack chain, this double approach ensures if one delivery mechanism is blocked or fails, the other can still achieve execution.”
The campaign appears to target users in Pakistan, as evidenced by the tax-themed documents written in English and localized to the region. However, no known advanced persistent threat (APT) group has been definitively linked to this operation.
