tcpcopy: A TCP Stream Replay Tool
TCPCopy – A TCP Stream Replay Tool
TCPCopy is a TCP stream replay tool to support real testing of Internet server applications.
Although the real live flow is important for the test of Internet server applications, it is hard to simulate it as online environments are too complex. To support more realistic testing of Internet server applications, we develop a live flow reproduction tool – TCPCopy, which could generate the test workload that is similar to the production workload.
TCPCopy has little influence on the production system except occupying additional CPU, memory, and bandwidth. Moreover, the reproduced workload is similar to the production workload in request diversity, network latency, and resource occupation.
Scenarios
- Distributed stress testing
- Use tcpcopy to copy real-world data to stress test your server software. Bugs that only can be produced in high-stress situations can be found
- Live testing
- Prove the new system is stable and find bugs that only occur in the real world
- Regression testing
- Performance comparison
Architecture
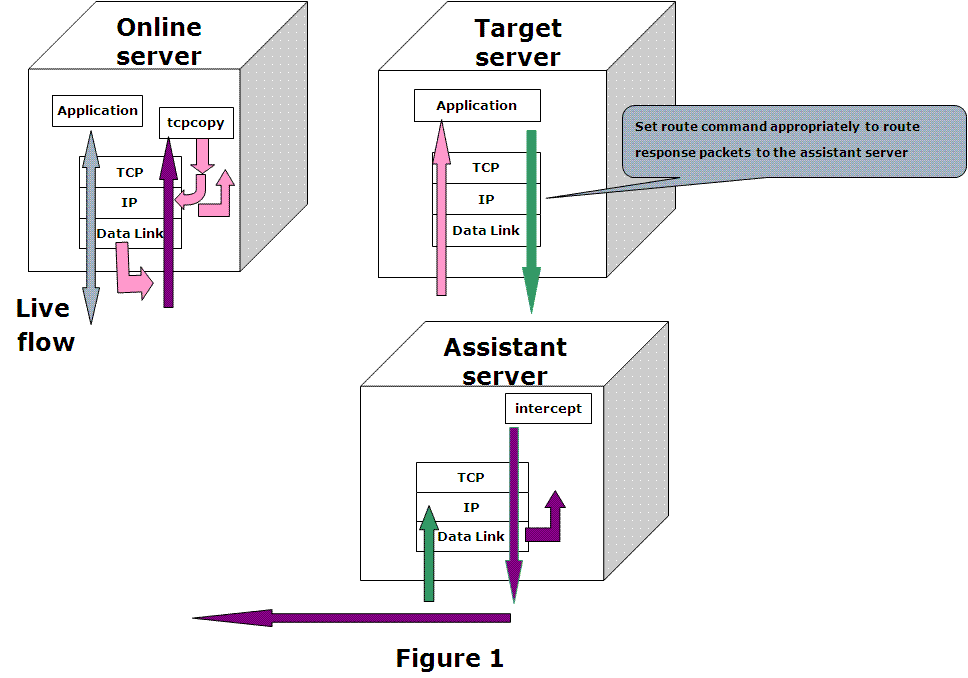
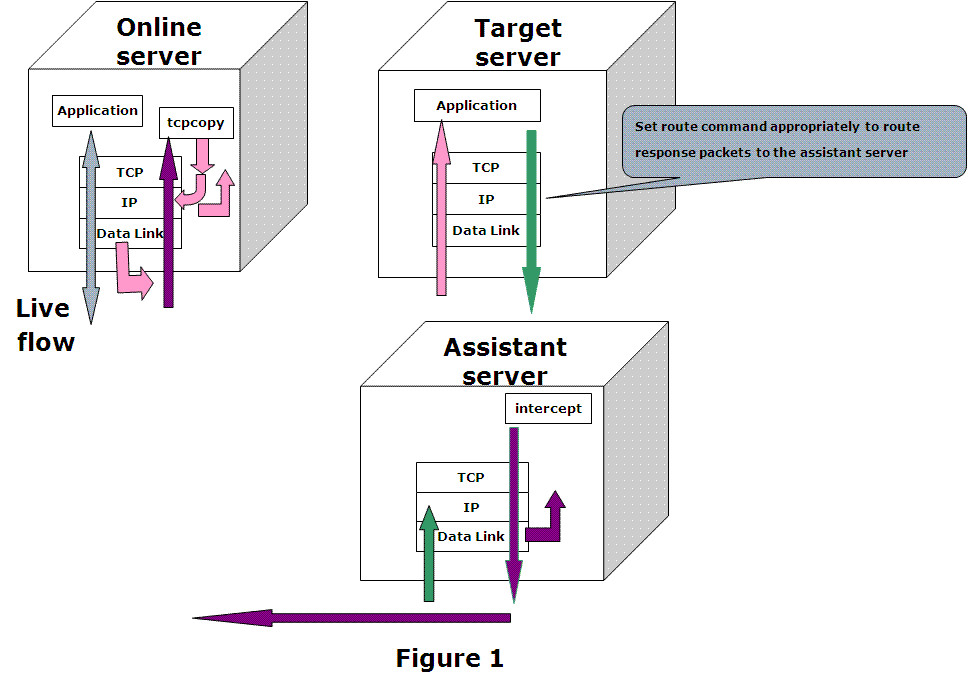
As shown in Figure 1, TCPCopy consists of two parts: tcpcopy and intercept. While tcpcopy runs on the online server and captures the online requests, intercept runs on the assistant server and does some assistant work, such as passing response info to tcpcopy. It should be noted that the test application runs on the target server.
tcpcopy utilizes raw socket input technique by default to capture the online packets at the network layer and does the necessary processing (including TCP interaction simulation, network latency control, and common upper-layer interaction simulation), and uses raw socket output technique by default to send packets to the target server (shown by pink arrows in the figure).
The only operation needed on the target server for TCPCopy is setting appropriate route commands to route response packets (shown by green arrows in the figure) to the assistant server.
intercept is responsible for passing the response header(by default) to tcpcopy. By capturing the response packets, intercept will extract response header information and send the response header to tcpcopy using a special channel(shown by purple arrows in the figure). When tcpcopy receives the response header, it utilizes the header information to modify the attributes of online packets and continues to send another packet. It should be noticed that the responses from the target server are routed to the assistant server which should act as a black hole.
Copyright (C) 2011-2014 NetEase, Inc.
Copyright (C) 2012-2014 Alibaba Group Holding Limited
Copyright (C) 2011-2014 ChangYou.com Limited