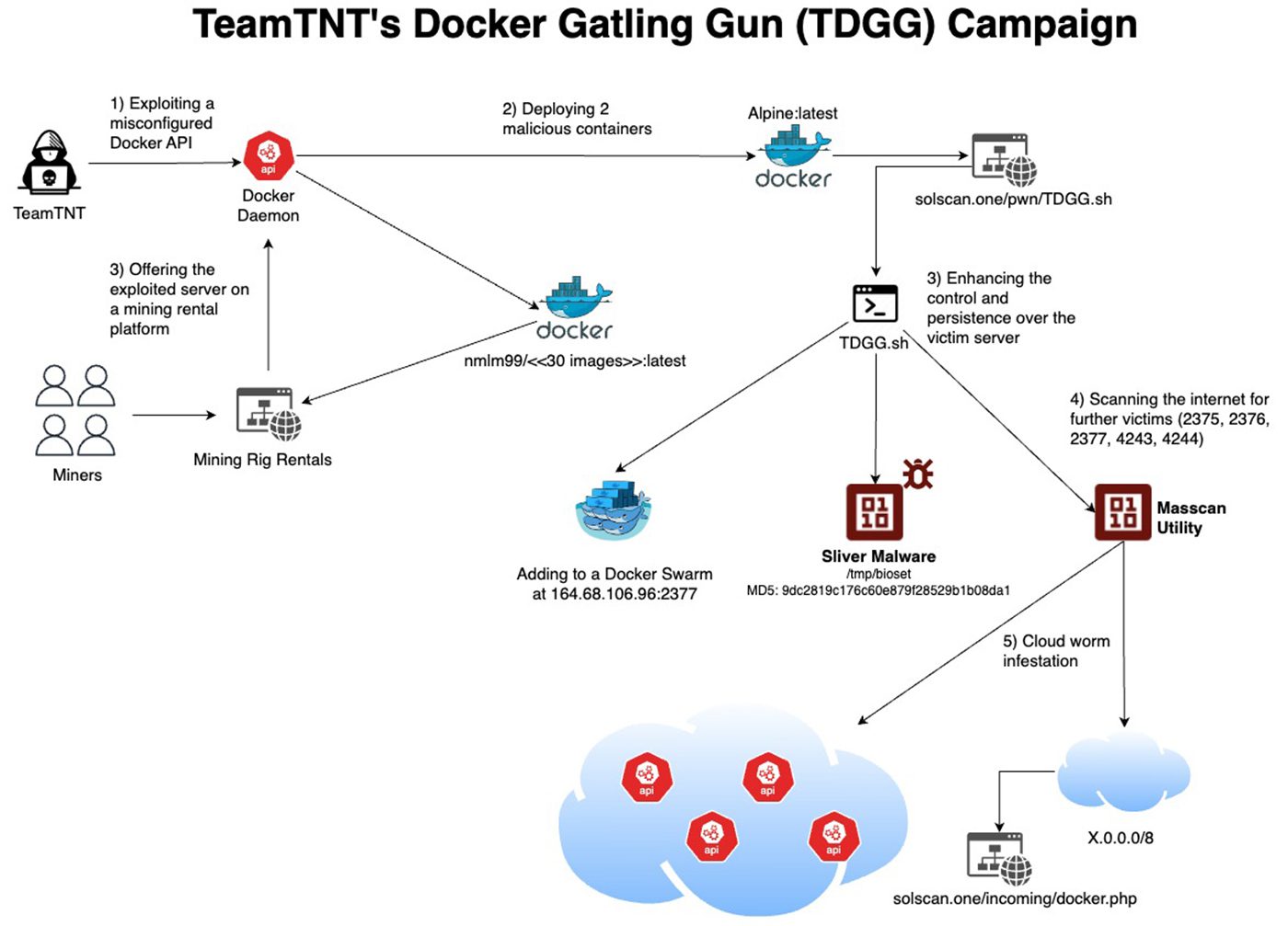
The entire attack flow | Image: Aqua Nautilus
A new report from Aqua Nautilus, led by Assaf Morag, Director of Threat Intelligence, has revealed a large-scale campaign by the notorious hacking group TeamTNT, known as the “Docker Gatling Gun.” TeamTNT, which previously abandoned some of its attack strategies, has returned with a renewed focus on exposed Docker environments, leveraging them to deploy cryptominers, malware, and even sell compromised computing power to third parties.
In this campaign, TeamTNT uses “native capabilities in cloud environments by appending compromised Docker instances to a Docker Swarm,” facilitating malware deployment through shared resources. They have also introduced the powerful Sliver malware, an upgrade from their previous Tsunami backdoor, which enables advanced Command and Control (C2) capabilities over multiple protocols like HTTPS and DNS.
The report describes TeamTNT’s attack flow as methodical and multifaceted. The group begins by scanning for exposed Docker daemons on ports 2375, 2376, 4243, and 4244, using a custom attack script dubbed “Docker Gatling Gun” that targets up to 16.7 million IP addresses. Once access is gained, they deploy an initial script, TDGGinit.sh, from Docker Hub, which “executes an Alpine Linux image with malicious commands,” thus taking over the Docker instance.
From here, TeamTNT incorporates multiple malicious techniques that reflect their campaign’s overall goals:
- Resource Hijacking: After compromising a system, they either install cryptomining software or rent out the victim’s computational power, generating revenue without needing to manage cryptomining infrastructure.
- C2 with Sliver Malware: Sliver replaces the less stealthy Tsunami malware, adding encryption and multi-protocol support for C2 channels, which makes it harder for defenders to detect. Sliver’s implants support Command and Control (C2) over multiple protocols, including mTLS, WireGuard, HTTP(S), and DNS
- Lateral Movement and Persistence: By exploiting local networks, TeamTNT spreads its infection across additional Docker instances within the same infrastructure, integrating these compromised nodes into a Docker Swarm for seamless control.
- Credential Theft and Misconfigurations: The report notes that TeamTNT actively searches for misconfigured files, such as SSH and cloud service credentials, storing these details to spread malware through unsecured accounts. As TeamTNT expands its infrastructure, it gains persistent access and deeper control over targeted environments.
TeamTNT also resorts to a familiar tactic—leveraging Docker Hub as a storage and distribution hub for malicious images. The report indicates that TeamTNT compromised a Docker Hub account, “uploading around 30 images, divided into infrastructure and impact images,” which allows them to target victims with ease and scale their campaign effectively. In another sign of persistence, they have revived their former domain, teamtnt.red, and registered new malicious domains to support their campaign’s resurgence.
Given the scale and sophistication of TeamTNT’s latest operations, Aqua Nautilus advises organizations to secure Docker environments rigorously. Recommendations include:
- Restricting Docker daemon access to prevent unauthorized connections.
- Regularly monitoring Docker Hub for suspicious or unusual activity.
- Enforcing multi-factor authentication and privileged access controls to reduce exposure.