Image: 0x6rss
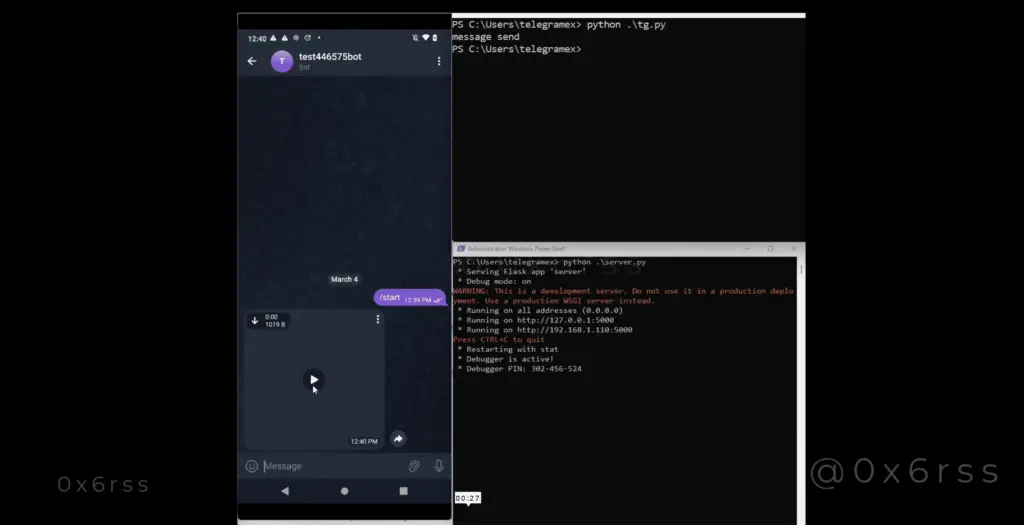
In June 2024, a vulnerability was discovered in the instant messaging platform Telegram, specifically affecting Telegram for Android. This flaw enabled hackers to craft specially designed APK files and send them to users, appearing as embedded videos in messages and automatically downloading upon receipt.
If a user attempted to play the video, a system notification would prompt them to install the unknown APK file. This deceptive tactic allowed attackers to lure victims into installing malicious applications, ultimately leading to the theft of sensitive information, such as private keys for encrypted wallets.
Now, this vulnerability has resurfaced. While it no longer permits automatic APK downloads and installation prompts as before, it can still disguise malicious links as embedded videos, enticing users to click external links.
Security researcher 0x6rss identified that fraudsters are leveraging this flaw to distribute malware. The fraudsters’ modus operandi is as follows:
- They create an .htm file containing the exploit.
- They modify the file, embedding a malicious application’s web link.
- They send this .htm file to targeted users.
When received by Telegram for Android, the file appears as a playable video. However, when users attempt to play it, they receive a prompt stating the video cannot be played and are advised to open it in an external browser.
Upon clicking again, users are redirected to a phishing page masquerading as Google Play. If they download and install the malicious APK from this page, the fraudsters achieve their objective.
For the attack to succeed, users must click the embedded link 3–4 times, disable Android’s security restriction on installing apps from unknown sources, and ultimately proceed with the installation. Though the process requires multiple steps, less tech-savvy users may still fall victim to it.
Researchers have named this vulnerability EvilLoader, as it builds upon the EvilVideo exploit discovered in June of the previous year. They also noted that the .htm file facilitating this attack has been available for sale on underground hacker forums since at least January 15, 2025.
At its core, the vulnerability stems from Telegram erroneously identifying .htm files as videos—a flaw nearly identical to last year’s issue. Telegram appears to misclassify various file types as video content, which is being exploited once again.
Since Telegram has yet to patch this vulnerability, users seeking enhanced security should disable auto-download feature.
Related Posts:
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- Following Russian, Iran also issued a signal to ban Telegram
- Android App Bundles and Dynamic Delivery will customize application packages for different versions of Android